Remove Dfltsearch.com browser hijacker virus from your computer by reading my virus removal guide.
First and foremost, let’s find out what Dfltsearch.com is before we can discuss how to remove it. Further knowledge of this threat will aid you in recognizing similar threats quickly in the future.
By taking a closer look at it, it becomes apparent that Dfltsearch.com is more than just a mere browser tool; it is a browser hijacker. This means that everytime you open your internet browser, it secretly compels you to visit a specific website (Dfltsearch.com).
This happens after it has been installed by slyly modifying your web browser’s settings.
The sneaky thing about Dfltsearch.com is how it gets onto your PC. Sometimes, people unknowingly add this software as they might think that their browsing experience could be better or when it comes bundled with other programs so they do not see any harm in installing them. Once installed however, such programs change your search results and home pages which now point to the Dfltsearch.com without your consent.
What makes this even annoying is that while trying to go back to your usual sites, you still keep ending up on this hijacker instead. That’s not just inconvenient; also remember that there are privacy issues associated with spammers who always track users’ online activities.
What exactly is Dfltsearch.com?
Positioning itself as an easy-to-use homepage option for users looking for smooth browsing experiences, Dfltsearch.com is not what it claims to be on the surface. This software operates as a browser hijacker at its core.
When we say browser hijackers modify settings within your web browser without receiving permission from the user, one of clear indications of their influence can tell when they change the default search engine and take over any new tabs’ homepages, redirecting them to their own site — in this case: Dfltsearch.com.
Dfltsearch.com browser hijacker
Summary:
- Dfltsearch.com presents itself as a handy homepage option and search tool.
- It claims to offer seamless browsing experiences to users.
- It is a browser hijacker.
- It modifies settings within your web browser without permission.
- It alters the default search engine and takes over the new tab’s homepage.
- It redirects the homepage to its page.
Dfltsearch.com domain WHOIS record:
Domain Name: DFLTSEARCH.COM
Registry Domain ID: 2888035201_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.cloudflare.com
Registrar URL: http://www.cloudflare.com
Updated Date: 2025-05-07T04:10:39Z
Creation Date: 2024-06-06T07:51:54Z
Registry Expiry Date: 2026-06-06T07:51:54Z
Registrar: Cloudflare, Inc.
Registrar IANA ID: 1910
Registrar Abuse Contact Email: registrar-abuse@cloudflare.com
Registrar Abuse Contact Phone: +1.6503198930
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Name Server: CHAD.NS.CLOUDFLARE.COM
Name Server: MARGOT.NS.CLOUDFLARE.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2025-08-01T18:59:20Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Dfltsearch.com domain age:
1 years, 1 months, 26 days
Why is Dfltsearch.com Harmful?
Although Dfltsearch.com might initially appear harmless or useful, it conceals its primary intent: data collection. The browser hijacker is designed to gather various data from your web activities. This could range from your search histories, visited websites, and interactions on specific sites to personal data like location, IP address, and more.
The data amassed by Dfltsearch.com isn’t merely stored; it’s actively monetized. It is often sold to advertising networks, thereby allowing tailored ads to be shown to you, often in an intrusive manner. The barrage of targeted ads isn’t just annoying; it can slow browsing and expose you to potential threats.
Additionally, because Dfltsearch.com extracts data without users’ explicit consent, it’s tagged as a potentially unwanted program (PUP). The PUP classification is reserved for programs that might not be malicious, like viruses, but can pose risks or annoyances to the user.
Summary:
- Dfltsearch.com is a browser hijacker that collects data from users’ web activities
- It collects information such as search histories, visited websites, and personal data like location and IP address
- The collected data is monetized and sold to advertising networks for targeted ads
- This can lead to annoying and intrusive ads, as well as potential browsing issues and security threats
- Dfltsearch.com is considered a potentially unwanted program (PUP) because it extracts data without explicit user consent
How Does Dfltsearch.com Spread?
Even though Dfltsearch.com might seem harmless or beneficial at first sight, it masks its major purpose – to collect data. Most often, browser hijackers extract all possible information from your web activities.
It can include the search history, visited pages and actions in some websites to personal data like our location and IP address.
The collected information by Dfltsearch.com is not just stored; it is actively monetized. By selling these data to advertisement networks, you are able to see personalized ads most times annoyingly popping up on your device. The incessantness of directed advertisements does not only bother; but likewise slows down the internet while exposing you to threats.
Additionally, as Dfltsearch.com takes hold of users’ data without their explicit permission it classifies it as potentially unwanted program (PUP). However, PUPs are programs that may not be harmful like viruses but may pose risks or annoyances to a user.
Summary:
- Dfltsearch.com is a browser hijacker that captures user’s online activity
- It gathers such information as search histories, visited sites and also individuals’ private details like places of residence and IP addresses
- The information gathered is commercialized through selling them advertising agencies hence leading to targeted ads
- These are irritating and intrusive ads that can result in browsing issues as well as security threats
Remove Dfltsearch.com from Google Chrome, Microsoft Edge or Firefox
Remove the Extension via Chrome:
- Go to
chrome://extensionsand try to delete the extension there.
Extensions with Enterprise Policy:
Some extensions may have an “enterprise policy” preventing deletion. In this case, try the following steps before proceeding to the Last Resort methods below:
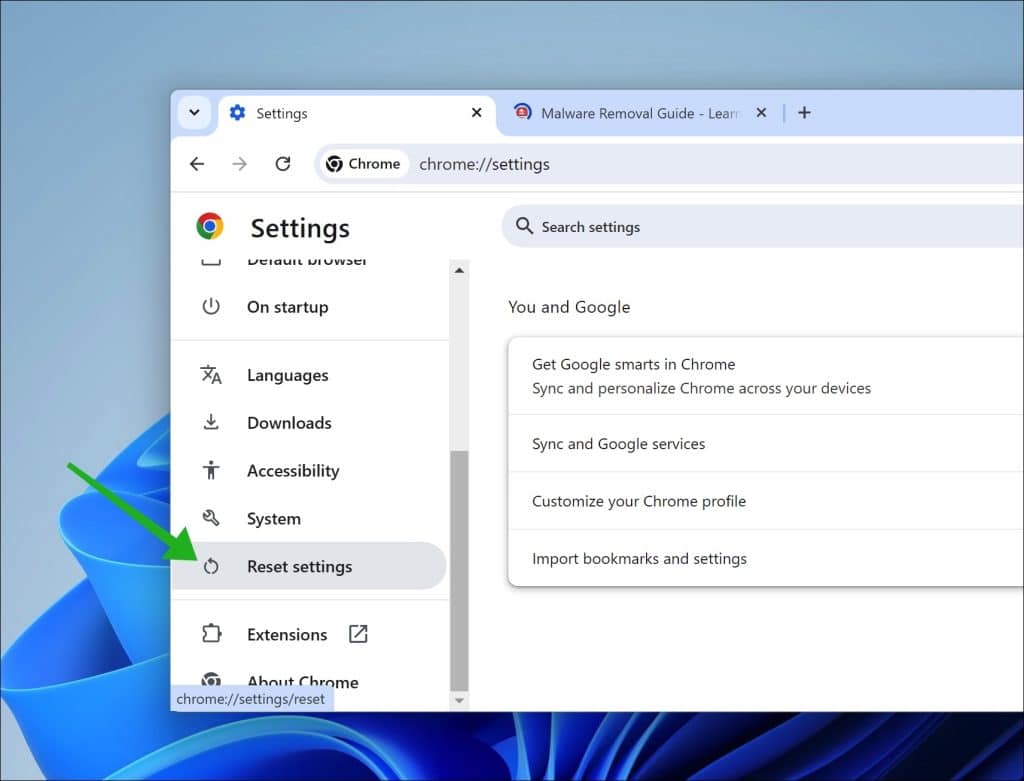
1. Reset browser to Default Settings:
Google Chrome
- Open the menu at the top right.
- Go to Settings.
- Scroll down to Reset settings.
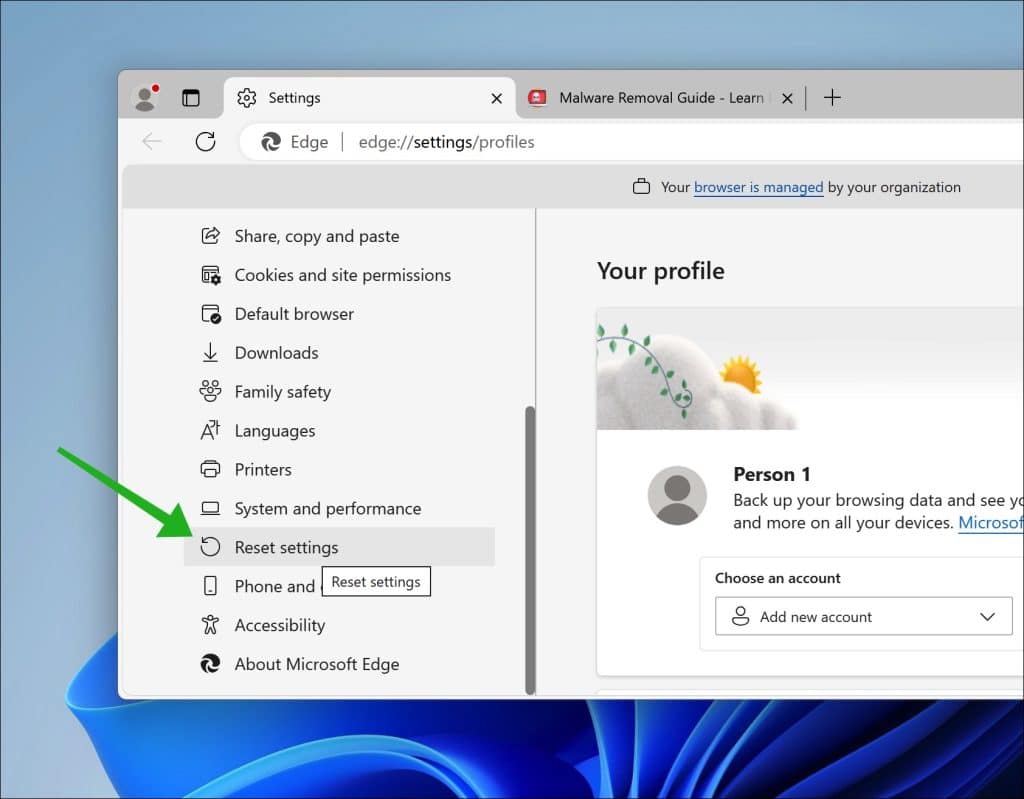
Microsoft Edge
- Open the menu at the top right.
- Go to Settings.
- Scroll down to Reset settings.
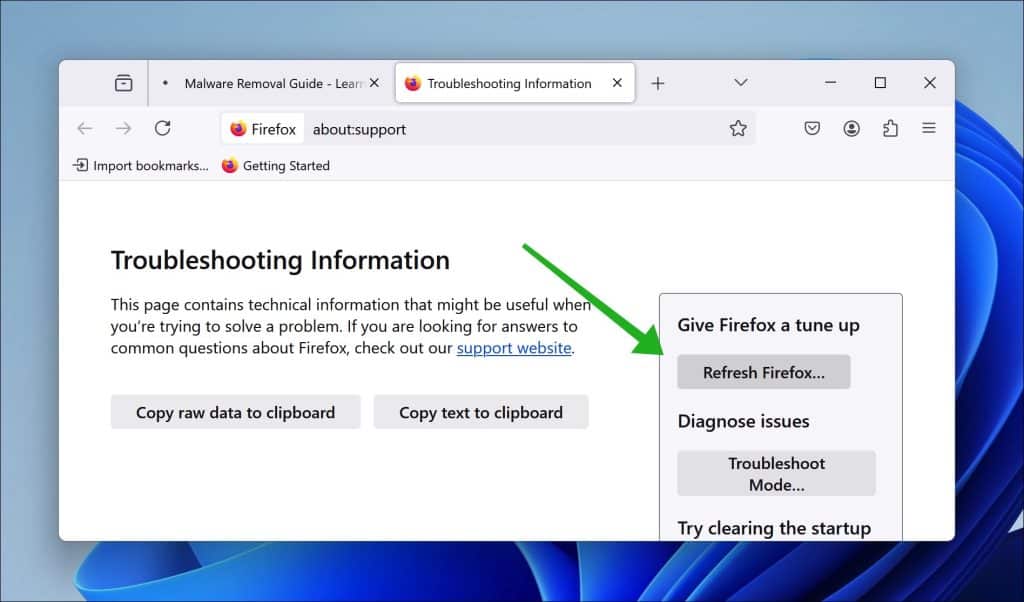
Firefox browser
- Open the menu at the top right.
- Go to Help.
- Go to More troubleshooting information.
- Click on Refresh Firefox.
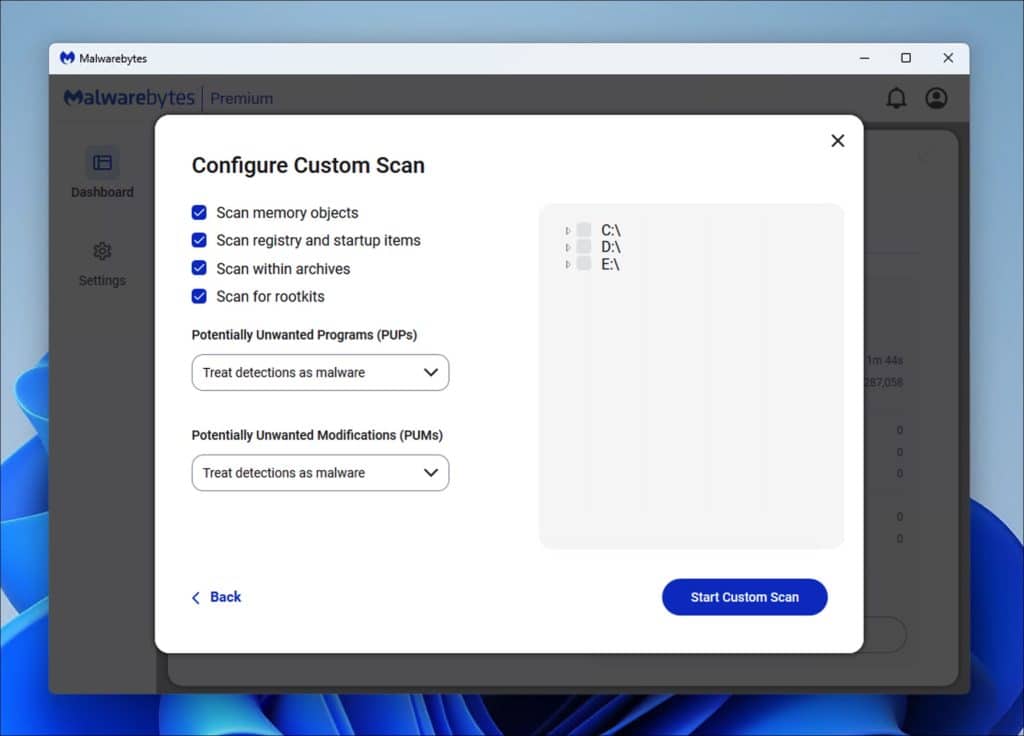
2. Download and Run Malwarebytes Anti Malware:
- Download Malwarebytes Anti Malware.
- Run a complete scan:
- Click Scan.
- Click Advanced Scan.
- Click Custom Scans.
- Select Scan for Rootkits and ensure the C: drive is ticked.
- The scan may take a while. If Malwarebytes flags any PUPS or malware, quarantine, delete, and reboot.
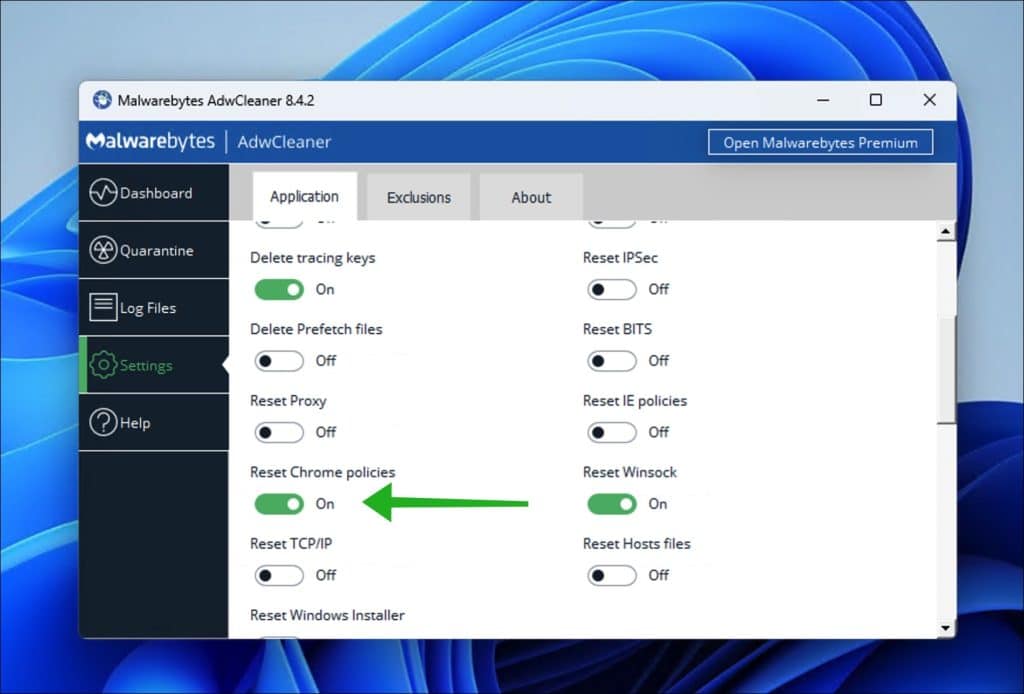
3. Download and Run Malwarebytes Adwcleaner:
- Download Malwarebytes Adwcleaner here.
- Open the Settings and ensure Reset Chrome Policies is turned on.
- Run the scan, quarantine, and delete any PUPs or adware.
- Reboot and check Chrome Extensions again.
4. Last Resort Steps (Remove browser is managed by your organization)
Google Chrome
First method
- Open Start, type
Registry Editor, and right-click Registry Editor > Run as Administrator. Enter the Administrator password when prompted. - Open Google Chrome, navigate to
chrome://extensions, and toggle Developer Mode on. - Find the extension you wish to delete, and copy the extension ID.
- Return to Registry Editor, click Edit > Find, and paste the ID into the search box. Click ‘Find Next’.
- Wait for regedit to find the key, then right-click > Delete the registry key. This should delete the extension from root.
- Reboot the computer, and run
sfc /scannowto restore any damaged system files. The computer should now be free from any remnants of the extension.
Second Method (Only Use if the First Method Does Not Work):
- Open Start, type
Registry Editor, and right-click Registry Editor > Run as Administrator. Enter the Administrator password when prompted. - Navigate to the following keys, and right-click > Delete. Make sure to delete the Folder in the left column, not just the registry entry:
-
HKEY_CURRENT_USER\Software\Google\ChromeHKEY_CURRENT_USER\Software\Policies\Google\ChromeHKEY_LOCAL_MACHINE\Software\Google\ChromeHKEY_LOCAL_MACHINE\Software\Policies\Google\ChromeHKEY_LOCAL_MACHINE\Software\Policies\Google\UpdateHKEY_LOCAL_MACHINE\Software\WOW6432Node\Google\Enrollment
-
- Navigate to
HKEY_LOCAL_MACHINE\Software\WOW6432Node\Google\Update\ClientState\{430FD4D0-B729-4F61-AA34-91526481799D}and delete the value namedCloudManagementEnrollmentTokenfrom the registry key. - Delete the directory where Google Update stores updated cached cloud policies:
%ProgramFiles(x86)%\Google\Policies.
Microsoft Edge
- Open Start, and search for
cmd. - Right-click Command Prompt, run as administrator, and type the following command:
reg delete HKLM\SOFTWARE\Policies\Microsoft\Edge /va /fRestart the Microsoft Edge browser.
5. Terminate Browser Processes:
- Close Google Chrome.
- Open Start and search for Task Manager; right-click and run Task Manager as Administrator.
- Search for the Google Update and any other Google Chrome or Google processes. Right-click and end the tasks.
6. Run System File Checker
- Close Task Manager, open Start, and search for
cmd. - Right-click Command Prompt, run as administrator, and type the following command:
sfc /scannow– This process checks for damaged system files and restores them. - Let the tool run its scan. When finished, exit CMD and reboot the computer.
- Upon reboot, open Chrome and check the extensions page. The malicious extension should now be deleted or able to be deleted. Try searching a webpage to check for any redirects.
- Run Malwarebytes again for good measure.
Your browser should be malware-free now. Thank you for reading!