Many individuals report facing issues with a website called Check-tl-ver-294-3.com. This website tricks users into accepting notifications, then bombards them with annoying advertisements on their phones or computers.
In this article, we’ll explain what Check-tl-ver-294-3.com is, how it operates, and provide simple steps to stop the ads from appearing on your screen or prevent the site from being a nuisance.
We’ll delve into details about this website, its workings, and methods to remove the ads.
So what is Check-tl-ver-294-3.com?
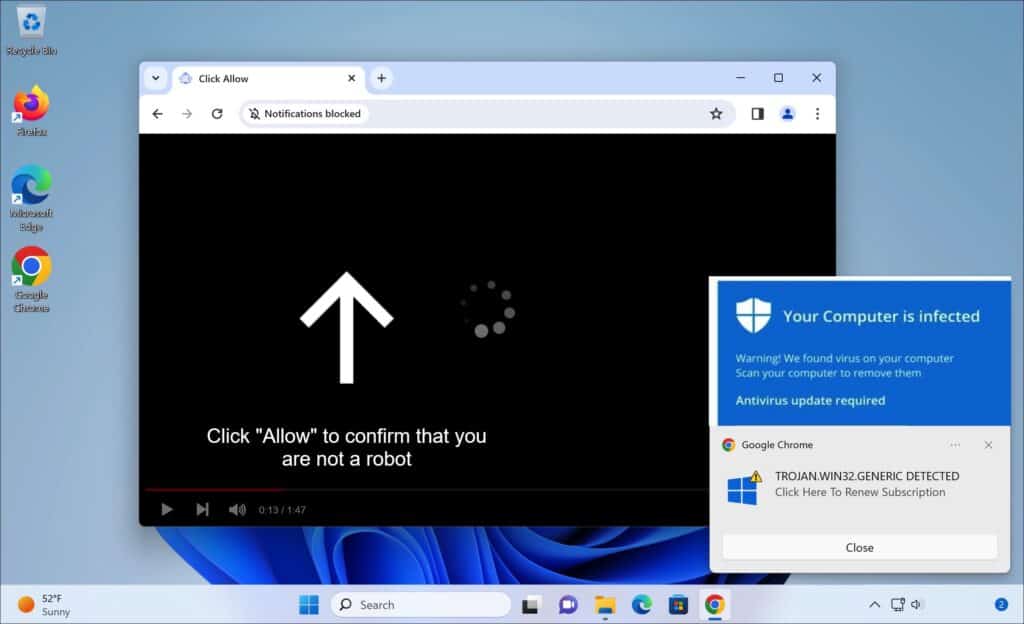
It’s a deceptive website. Through your browser, it displays fake error messages, tricking you into thinking “Allow Notifications” will fix something. But once accessed, it floods your device with multiple irritating, offensive pop-up ads. Some advertisements persist even when you’re not actively browsing the internet. Here’s a common way it deceives people:
Check-tl-ver-294-3.com domain WHOIS record:
Domain Name: CHECK-TL-VER-294-3.COM
Registry Domain ID: 2990698300_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.namerider.com
Registrar URL: http://namerider.com
Updated Date: 2025-07-16T05:41:33Z
Creation Date: 2025-06-10T18:43:31Z
Registry Expiry Date: 2026-06-10T18:43:31Z
Registrar: Domain Science Kutatasi Szolgaltato Korlatolt Felelossegu Tarsasag
Registrar IANA ID: 3882
Registrar Abuse Contact Email: verisign@virtuadrug.com
Registrar Abuse Contact Phone: +36 204191293
Domain Status: ok https://icann.org/epp#ok
Name Server: NS13.122TRK.COM
Name Server: NS14.122TRK.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
>>> Last update of whois database: 2025-08-01T19:41:57Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
NOTICE: The expiration date displayed in this record is the date the
registrar's sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant's agreement with the sponsoring
registrar. Users may consult the sponsoring registrar's Whois database to
view the registrar's reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services' ("VeriSign") Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Check-tl-ver-294-3.com domain age:
0 years, 1 months, 22 days
What does this popup do?
- False Alerts for Notifications: This site tricks you into turning on push notifications with fake system warnings. For instance, it might falsely warn you that your browser is outdated and needs an update.
- Unwanted Ads: Once you enable notifications, the site bombards your device with inappropriate ads. These can vary from adult content and dating site promotions to fake software update scams and questionable products.
- Bypassing Pop-up Blockers: By deceiving you into accepting push notifications, Check-tl-ver-294-3.com can get around the pop-up blockers in your browser. This means it can send ads straight to your device, even if you have a pop-up blocker activated.
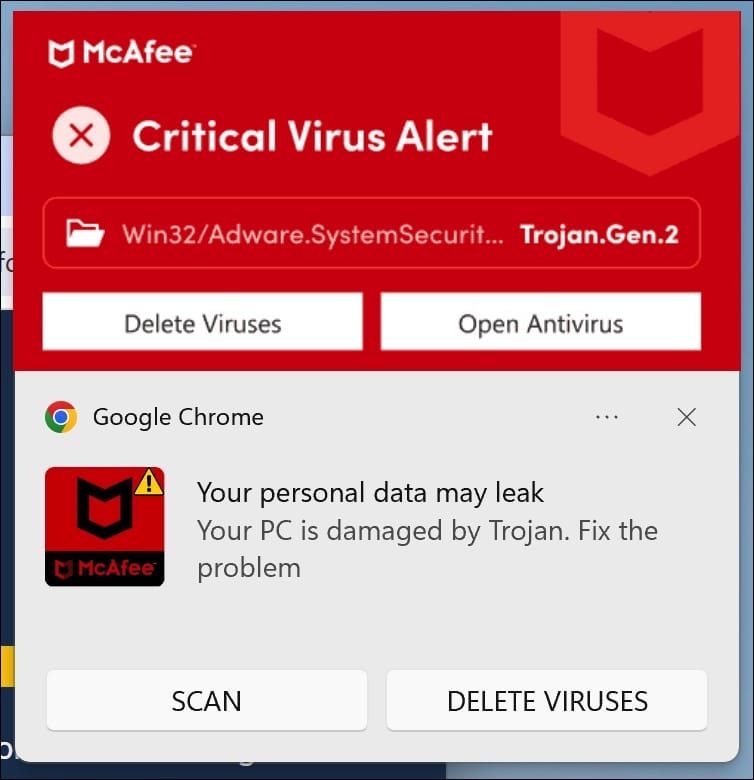
Why am I seeing these ads?
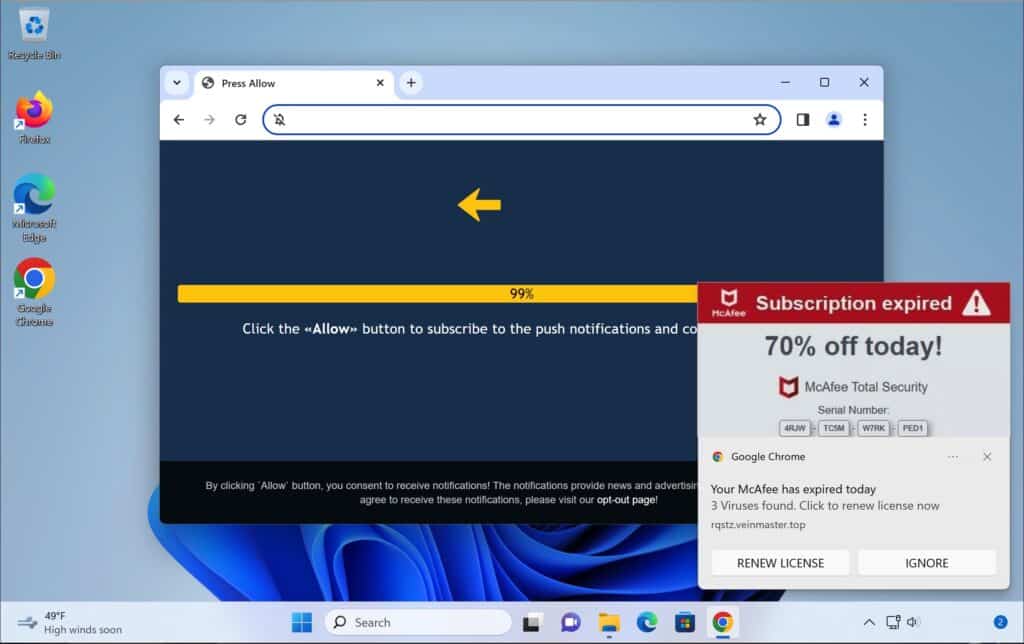
You may notice many pop-ups from Check-tl-ver-294-3.com. This likely happened because you accidentally enabled push notifications for that site. They might have tricked you in these ways:
- Showing fake error messages. These make you think enabling notifications is required.
- Hiding notification requests sneakily. So, you agreed without realizing.
- Redirecting unexpectedly. Sometimes it brings you there from another site or pop-up.
- Including in software installs. Some free programs bundle Check-tl-ver-294-3.com, enabling notifications secretly.
- Falsely claiming virus. It may say your computer’s infected and notifications remove “malware.”
This guide aims to help you identify and remove any unwanted software and potential malware related to Check-tl-ver-294-3.com from your computer.
- Begin by checking your browsers for any permissions inadvertently granted to Check-tl-ver-294-3.com.
- Review the applications installed on Windows 10 or 11 to rule out any related threats.
- There are specialized tools available that can detect and eliminate malware from your system. Employing such tools in this process is advised.
- After this guide, consider incorporating a reputable browser extension to fend off adware intrusions and block malicious pop-ups similar to those from Check-tl-ver-294-3.com.
Do not worry. In this guide, I will show you how to remove Check-tl-ver-294-3.com.
How to remove Check-tl-ver-294-3.com
Adware, malicious software, and unwanted applications can clutter your computer, compromising performance and security. This guide aims to walk you through a systematic process to clean your computer from such threats, especially those associated with pesky domains like Check-tl-ver-294-3.com.
Step 1: Remove permission for Check-tl-ver-294-3.com to send push notifications using the browser
First, we’ll withdraw access to Check-tl-ver-294-3.com from your browser settings. This action will halt Check-tl-ver-294-3.com from dispatching additional notifications to your browser. After finalizing this procedure, you won’t see any more intrusive ads linked to Check-tl-ver-294-3.com.
For guidance on executing this, please check the directions corresponding to your primary browser below and proceed to revoke the privileges granted to Check-tl-ver-294-3.com.
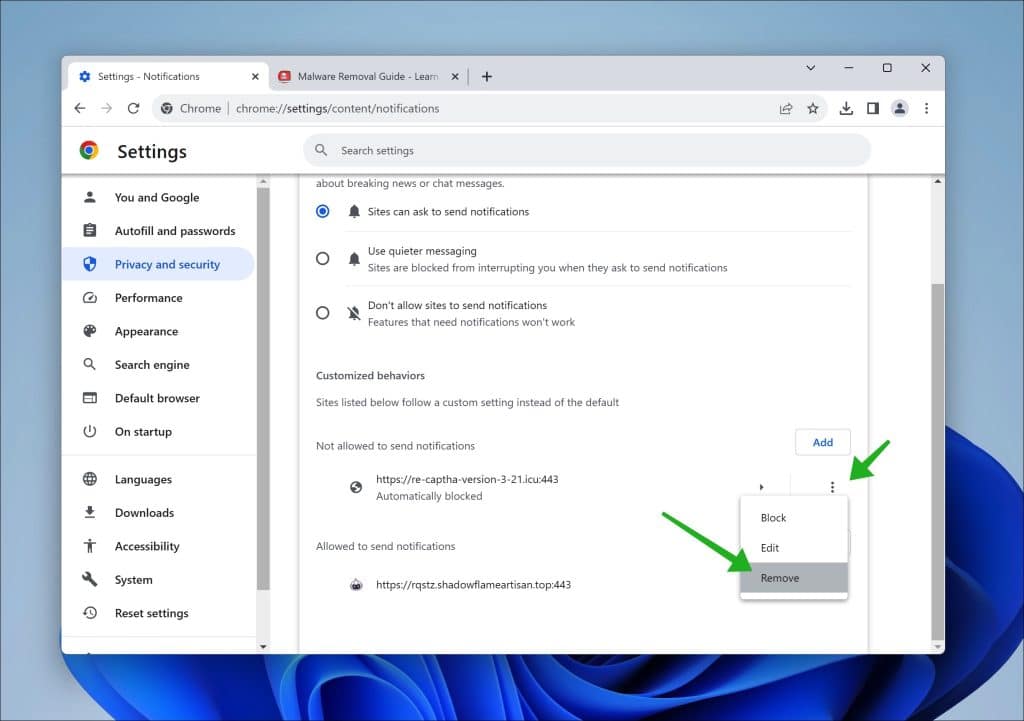
 Remove Check-tl-ver-294-3.com from Google Chrome
Remove Check-tl-ver-294-3.com from Google Chrome
- Open Google Chrome.
- Click on the three vertical dots in the top right corner to open the menu.
- Select “Settings.”
- On the left, click on “Privacy and security.”
- Click on “Site Settings.”
- Scroll down to “Permissions” and select “Notifications.”
- Under the “Allow” section, find and click on the Check-tl-ver-294-3.com entry.
- Click on the three vertical dots next to the entry and choose “Remove” or “Block.”
→ Go to the next step: Malwarebytes.
 Remove Check-tl-ver-294-3.com from the Android
Remove Check-tl-ver-294-3.com from the Android
- Open the “Settings” app on your Android device.
- Scroll down and tap on “Apps & notifications” or just “Apps,” depending on your device.
- Tap on “See all apps” if you don’t see the browser you use in the initial list.
- Find and tap on your browser app where you’re receiving the notifications (e.g., Chrome, Firefox).
- Tap on “Notifications.”
- Under the “Sites” or “Categories” section, find Check-tl-ver-294-3.com.
- Turn off the toggle next to it to block notifications.
If it doesn’t work, try the following for Google Chrome on Android.
- Open the Chrome app.
- Tap on the three vertical dots in the top-right corner to open the menu.
- Tap on “Settings.”
- Scroll down and tap on “Site Settings.”
- Tap on “Notifications.”
- Under the “Allowed” section, you will see Check-tl-ver-294-3.com if you’ve permitted it.
- Tap on Check-tl-ver-294-3.com, then turn off the “Notifications” toggle.
→ Go to the next step: Malwarebytes.
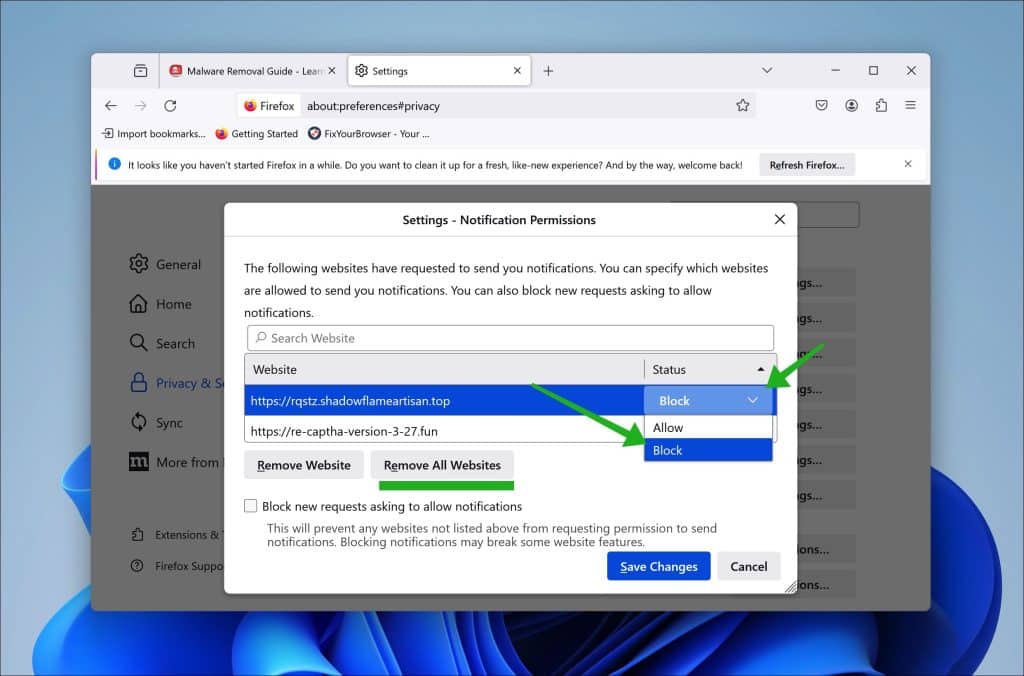
 Remove Check-tl-ver-294-3.com from Firefox
Remove Check-tl-ver-294-3.com from Firefox
- Open Mozilla Firefox.
- Click on the three horizontal lines in the top right corner to open the menu.
- Select “Options.”
- Click on “Privacy & Security” in the left sidebar.
- Scroll down to the “Permissions” section and click on “Settings” following “Notifications.”
- Locate Check-tl-ver-294-3.com in the list.
- In the drop-down menu next to its name, select “Block.”
- Click “Save Changes.”
→ Go to the next step: Malwarebytes.
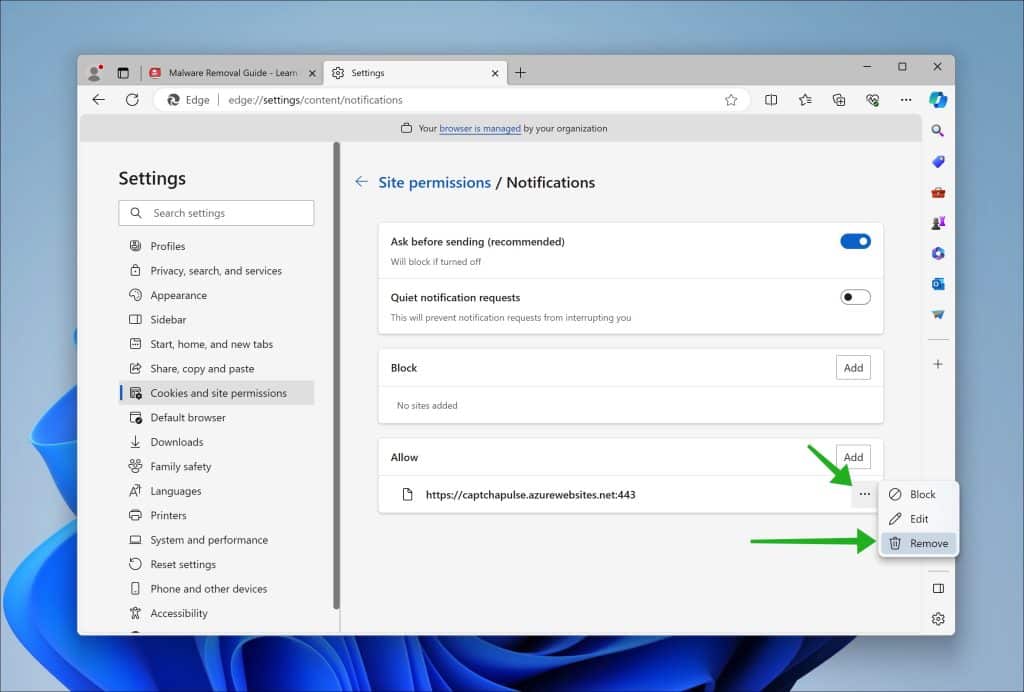
 Remove Check-tl-ver-294-3.com from Microsoft Edge
Remove Check-tl-ver-294-3.com from Microsoft Edge
- Open Microsoft Edge.
- Click on the three horizontal dots in the top right corner.
- Select “Settings.”
- Under “Privacy, search, and services,” click on “Site permissions.”
- Select “Notifications.”
- Under the “Allow” section, find the Check-tl-ver-294-3.com entry.
- Click on the three horizontal dots next to the entry and select “Block.”
→ Go to the next step: Malwarebytes.
 Remove Check-tl-ver-294-3.com from Safari on Mac
Remove Check-tl-ver-294-3.com from Safari on Mac
- Open Safari.
- In the top menu, click “Safari” and choose “Preferences.”
- Go to the “Websites” tab.
- In the left sidebar, select “Notifications.”
- Locate Check-tl-ver-294-3.com in the list.
- In the drop-down menu next to its name, select “Deny.”
→ Go to the next step: Malwarebytes.
Step 2: Remove adware browser extensions
Web browsers are extensively used for gathering information, communication, work, and leisure activities. Extensions enhance these tasks by providing additional functionality. However, it is crucial to exercise caution as not all extensions are benign. Some may attempt to obtain your personal data, display advertisements, or redirect you to malicious websites.
Identifying and removing such extensions is essential for safeguarding your security and ensuring a smooth browsing experience. This guide outlines the process of removing extensions from popular web browsers like Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari. By following the steps provided for each browser, you can enhance your browsing safety and improve the overall user experience.
 Google Chrome
Google Chrome
- Open Google Chrome.
- type: chrome://extensions/ in the address bar.
- Search for any adware browser extensions and click the “Remove” button.
It is important to check every extension installed. If you do not know or do not trust a specific extension, remove or disable it.
→ See the next step: Malwarebytes.
 Firefox
Firefox
- Open Firefox browser.
- type: about:addons in the address bar.
- Search for any adware browser add-ons and click the “Uninstall” button.
It is important to check every addon installed. If you do not know or do not trust a specific addon, remove or disable it.
→ See the next step: Malwarebytes.
 Microsoft Edge
Microsoft Edge
- Open the Microsoft Edge browser.
- type: edge://extensions/ in the address bar.
- Search for any adware browser extensions and click the “Remove” button.
It is important to check every extension installed. If you do not know or do not trust a specific extension, remove or disable it.
→ See the next step: Malwarebytes.
 Safari
Safari
- Open Safari.
- In the top left corner, click on the Safari menu.
- In the Safari menu, click on Preferences.
- Click on the Extensions tab.
- Click on the unwanted extension you want to be removed, then Uninstall.
→ See the next step: Malwarebytes.
It is important to check every extension installed. If you do not know or do not trust a specific extension, uninstall the extension.
Step 3: Uninstall adware software
Ensuring your computer is free from unwanted software like adware is crucial. Adware programs often hitchhike alongside legitimate applications you install from the internet.
They can slip in unnoticed during installation if you hastily click through prompts. This deceptive practice sneaks adware onto your system without explicit consent. To prevent this, tools like Unchecky can help you scrutinize each step, allowing you to opt out of bundled software. Following the steps below, you can scan for existing adware infections and remove them, regaining control over your device.
In this second phase, we’ll thoroughly inspect your computer for any adware that may have crept in. While you might inadvertently install such programs yourself when obtaining free software online, their presence is often masked as “helpful tools” or “offerings” during the setup process. If you’re not vigilant and breeze through installation screens, adware can quietly embed itself on your system. However, by exercising caution and employing utilities like Unchecky, you can avoid this underhanded bundling and keep your machine clean. Let’s proceed to detect and eliminate any adware currently residing on your computer.
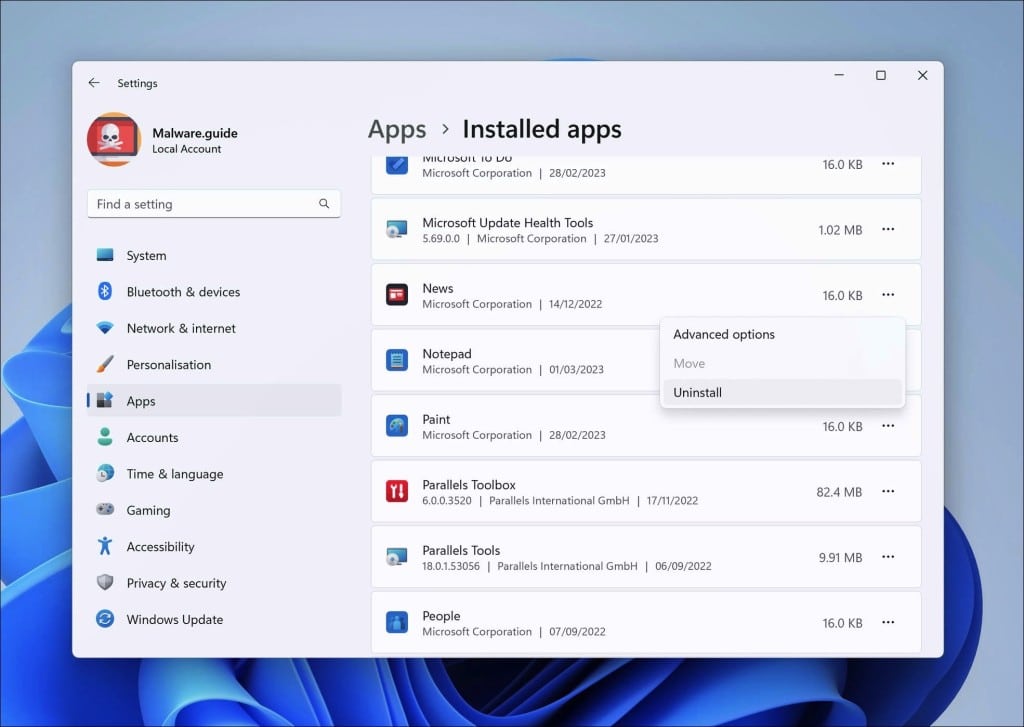
Windows 11
- Click on “Start.”
- Click on “Settings.”
- Click on “Apps.”
- Lastly, click on “Installed apps.”
- Search for any unknown or unused software in the list of recently installed apps.
- On the right-click on the three dots.
- In the menu, click on “Uninstall.”
→ See the next step: Malwarebytes.
Windows 10
- Click on “Start.”
- Click on “Settings.”
- Click on “Apps.”
- In the list of apps, search for any unknown or unused software.
- Click on the app.
- Lastly, click on the “Uninstall” button.
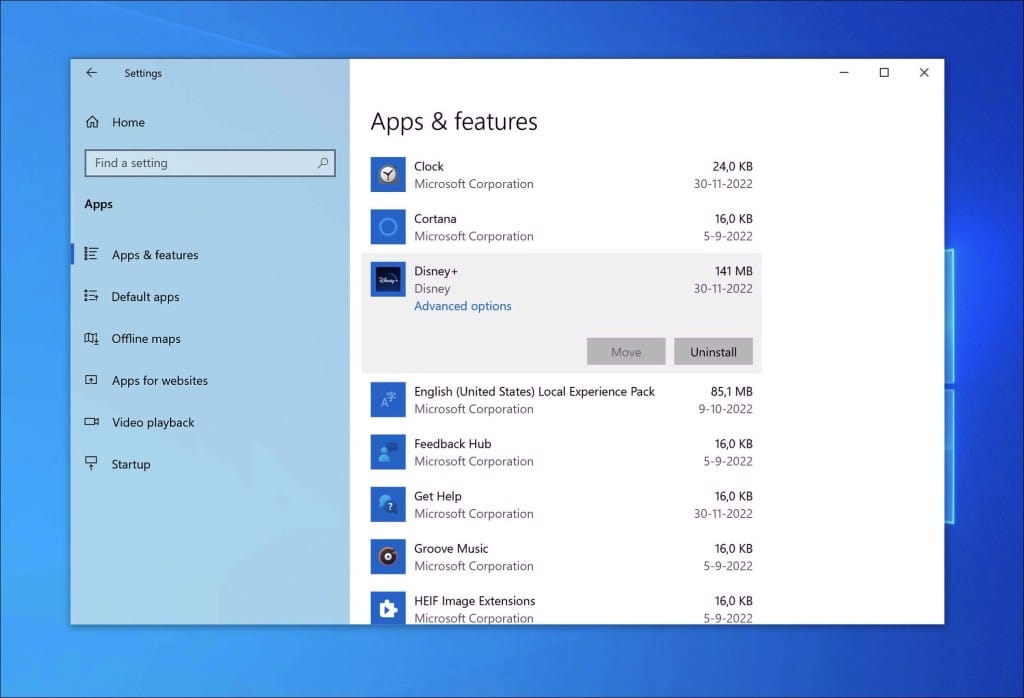
→ See the next step: Malwarebytes.
Step 4: Scan your PC for malware
Alright, now it is time to remove malware from your PC automatically. Using Malwarebytes, you can quickly scan your computer, review detections, and safely remove them from your PC.
Malwarebytes
Malwarebytes is the best – and most used – malware removal tool available today. It can detect all sorts of malware, such as adware, browser hijackers, and spyware. If it detects any malware on your computer, you can use it to remove it for free. Try it and see for yourself.
- Download Malwarebytes
- Install Malwarebytes, and follow the on-screen instructions.
- Click Scan to initiate a malware scan on your PC.
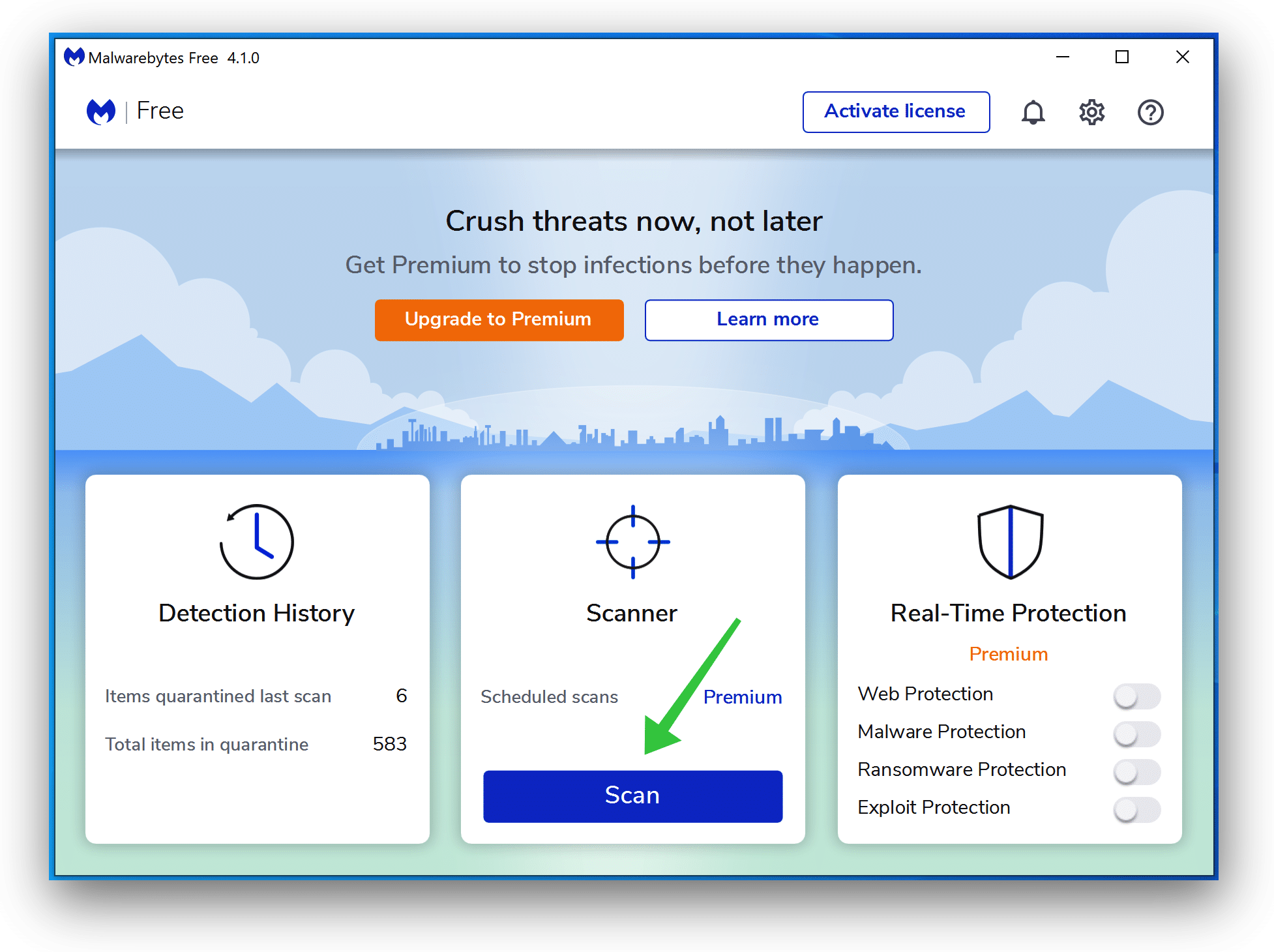
- Wait for the Malwarebytes scan to finish.
- Once completed, review the malware detections.
- Click Quarantine to continue.
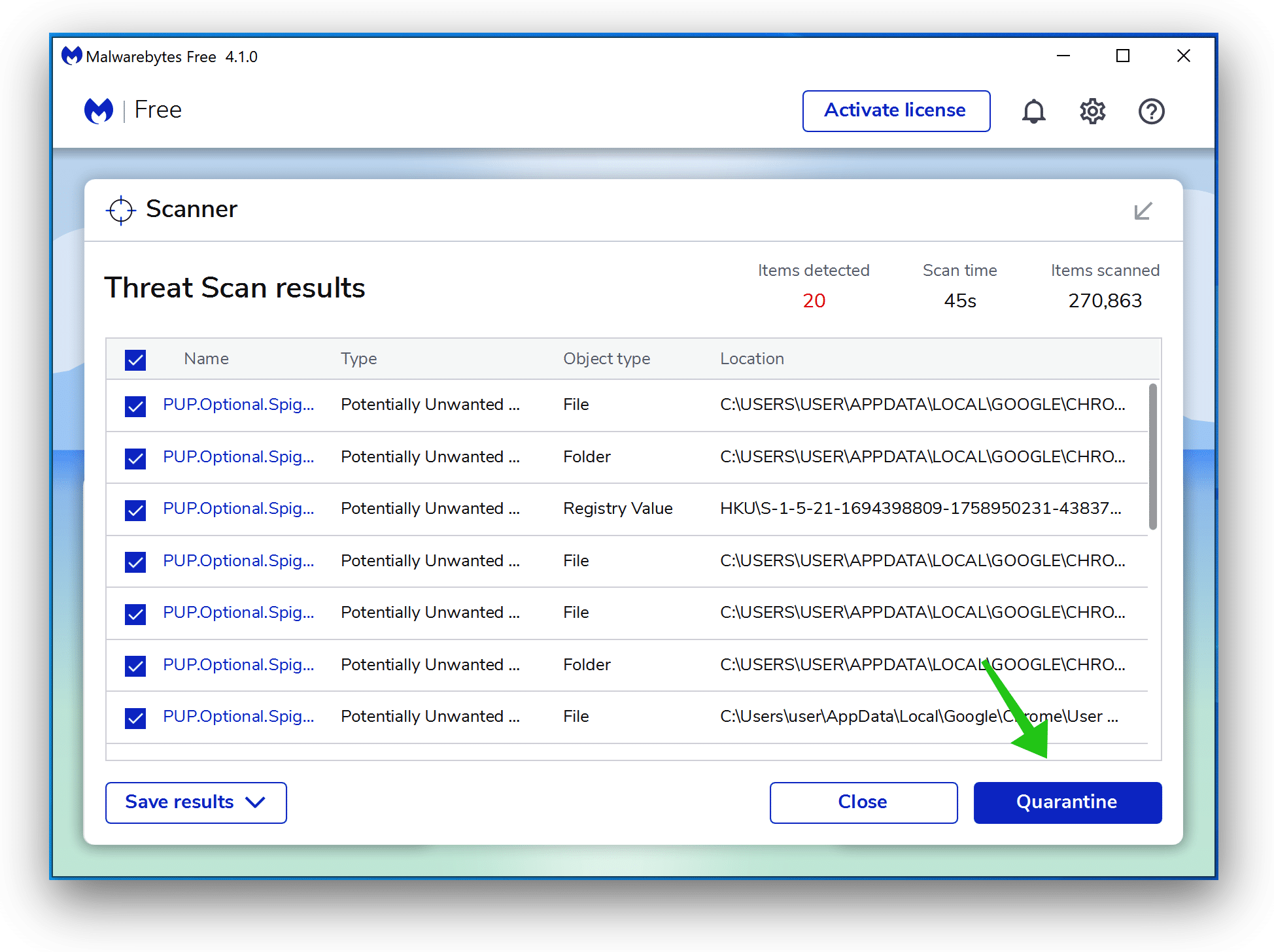
- Reboot Windows after all the malware detections are moved to quarantine.
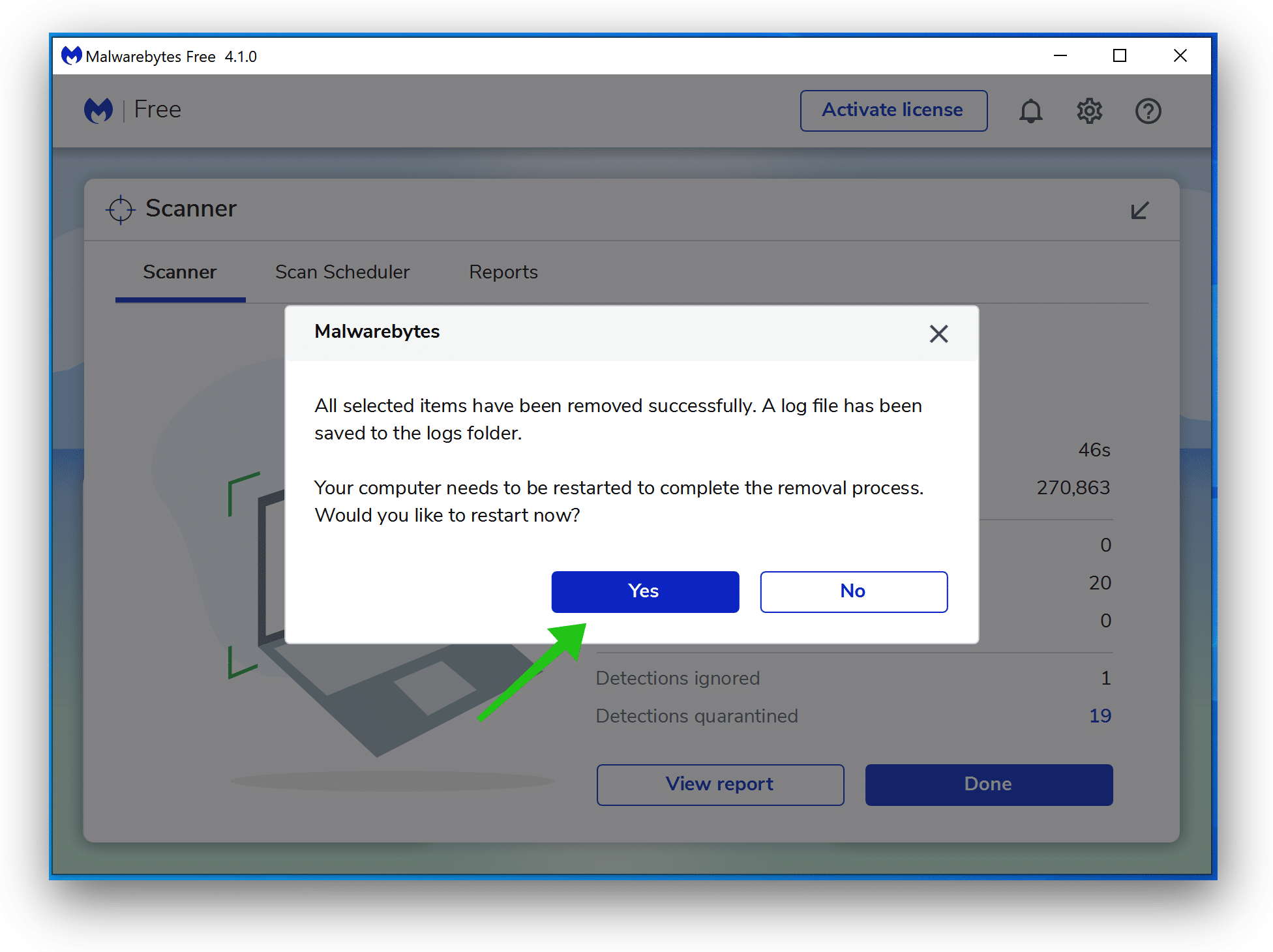
Combo Cleaner
Combo Cleaner is a cleaning and antivirus program for Mac, PC, and Android devices. It is equipped with features to protect devices from various types of malware, including spyware, trojans, ransomware, and adware. The software includes tools for on-demand scans to remove and prevent malware, adware, and ransomware infections. It also offers features like a disk cleaner, big files finder (free), duplicate files finder (free), privacy scanner, and application uninstaller.
Follow the installation instructions to install the application on your device. Open Combo Cleaner after installation.
- Click the "Start scan" button to initiate a malware removal scan.
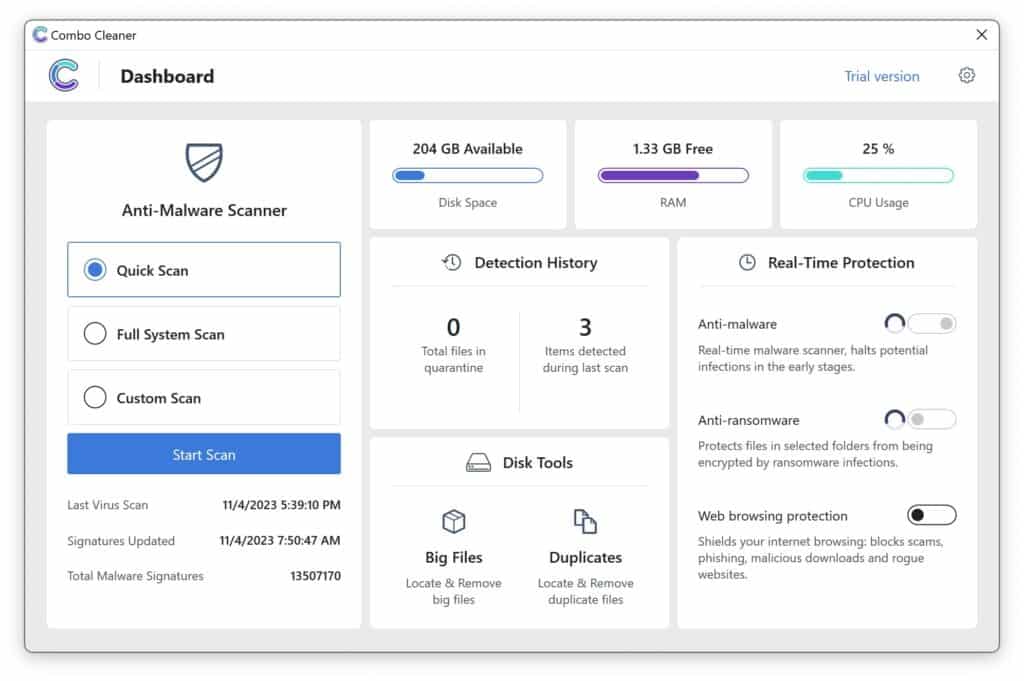
- Wait for Combo Cleaner to detect malware threats on your computer.
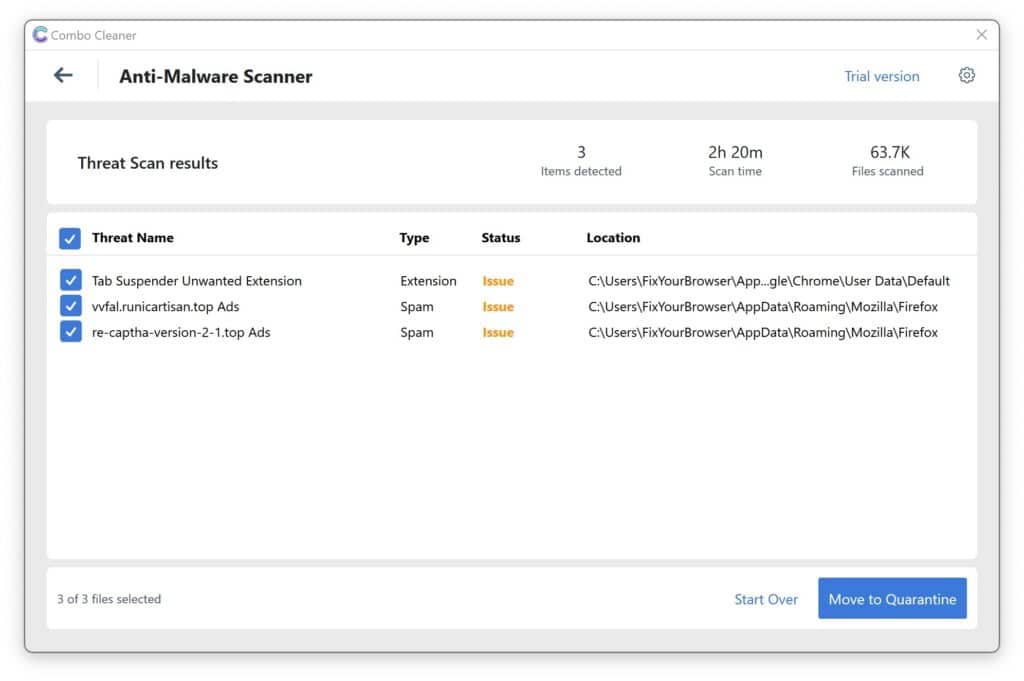
- When the Scan is finished, Combo Cleaner will show the found malware.
- Click "Move to Quarantine" to move the found malware to quarantine, where it can't harm your computer anymore.
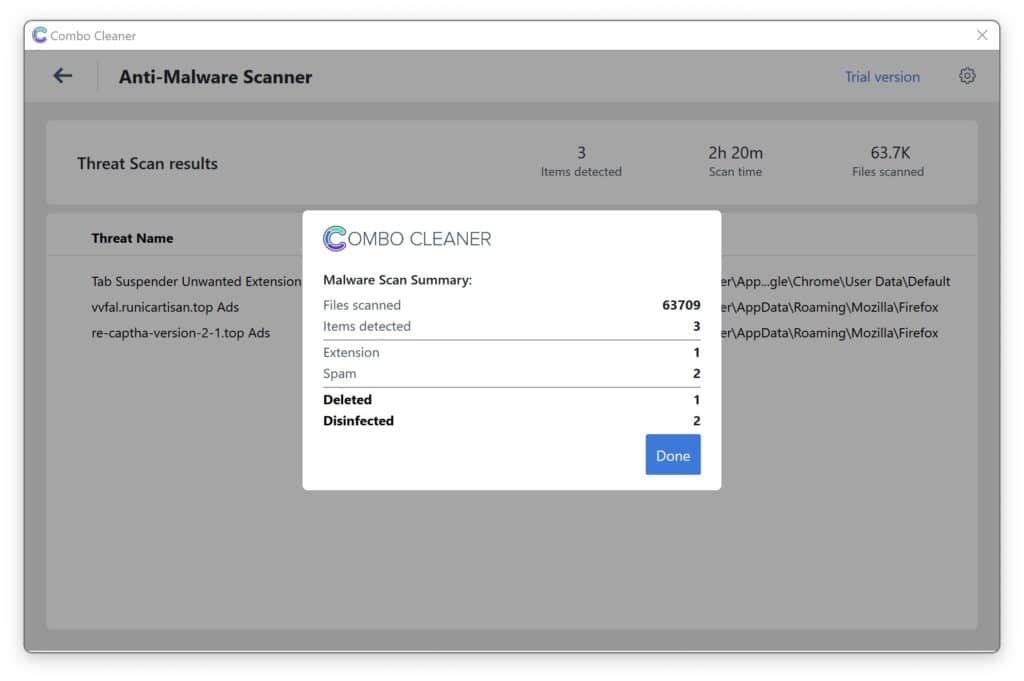
- A malware scan summary is shown to inform you about all threats found.
- Click "Done" to close the scan.
Use Combo Cleaner regularly to keep your device clean and protected. Combo Cleaner will remain active on your computer to protect your computer from future threats that try to attack your computer. If you have any questions or issues, Combo Cleaner offers a dedicated support team available 24/7.
AdwCleaner
You get stressed by pop-ups or odd browser acts? I know the fix. AdwCleaner is a free program from Malwarebytes that eliminates unwanted ad software sneaking onto computers.
It checks for apps and toolbars you didn’t intend to install. They can slow your PC or disrupt web use like that Check-tl-ver-294-3.com nuisance. Think of AdwCleaner as spyware detecting unwanted elements—no tech skills needed. Once found, it removes them safely. Is your browser misbehaving due to harmful programs? AdwCleaner can revert it to its normal condition.
- Download AdwCleaner
- No need to install AdwCleaner. You can run the file.
- Click “Scan now.” to initiate a scan.
- AdwCleaner starts downloading detection updates.
- Following is a detection scan.
- Once the detection is finished, click on “Run Basic Repair.”
- Confirm by clicking on “Continue.”
- Wait for the cleanup to complete; this won’t take long.
- When Adwcleaner is finished, click “View log file.” to review detections and cleanup processes.
Sophos HitmanPRO
Have you ever heard of HitmanPro? Think of it as an advanced investigator that not only searches for evidence on your computer, but also sends data to an intelligent hub (Sophos cloud) for further analysis.
Unlike traditional anti-malware tools, HitmanPro relies on cloud assistance to quickly and accurately detect and eliminate harmful software. If you’ve been dealing with annoying Check-tl-ver-294-3.com pop-ups, HitmanPro can help track down and eliminate them, and provide ongoing web threat protection. For a faster, cloud-powered malware detection solution, consider trying HitmanPro!
- Download HitmanPro.
- Click the “Next” button to continue the setup.
- Accept the terms and conditions to use Sophos HitmanPro.
- If you want to scan your computer regularly, click “yes.” If you do not want to scan your computer more often, click “No.”
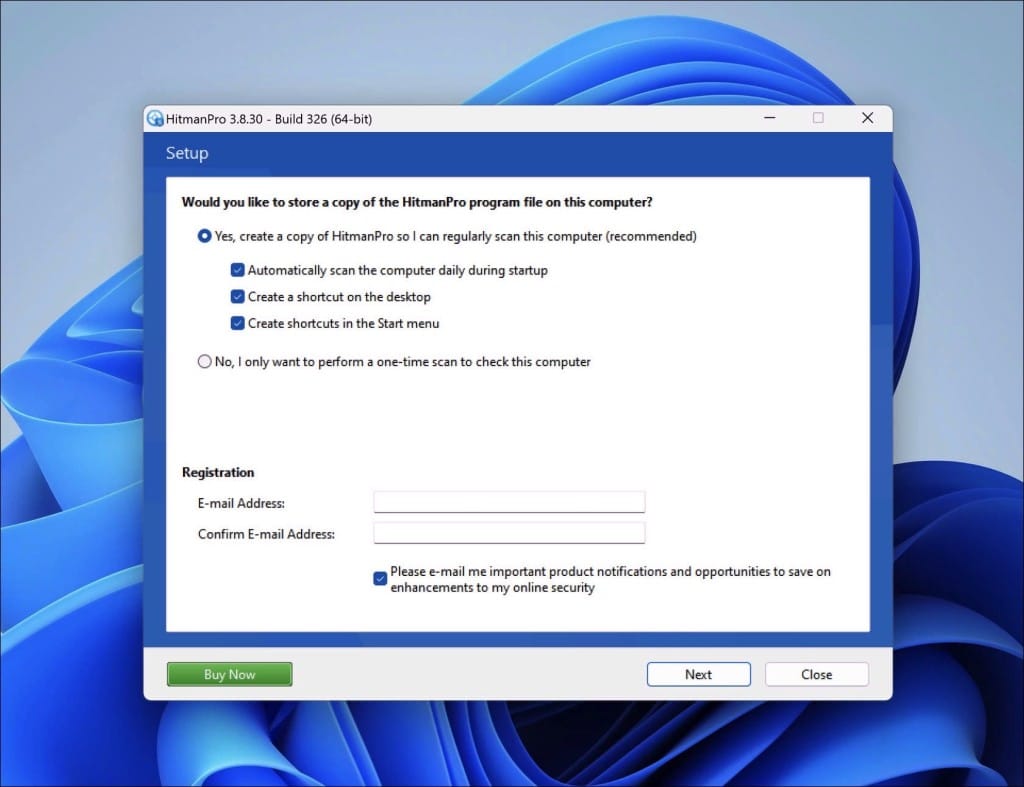
- Sophos HitmanPro will start a malware scan. Once the window turns red, it indicates malware or potentially unwanted programs have been found on your computer during this scan.
- Before removing the malware detections, you need to activate a free license.
- Click on the “Activate free license.” button.
- Provide your e-mail address to activate the one-time license, valid for thirty days.
- Click on the “Activate” button to continue the removal process.
- The HitmanPro product is activated successfully.
- We can now continue with the removal process.
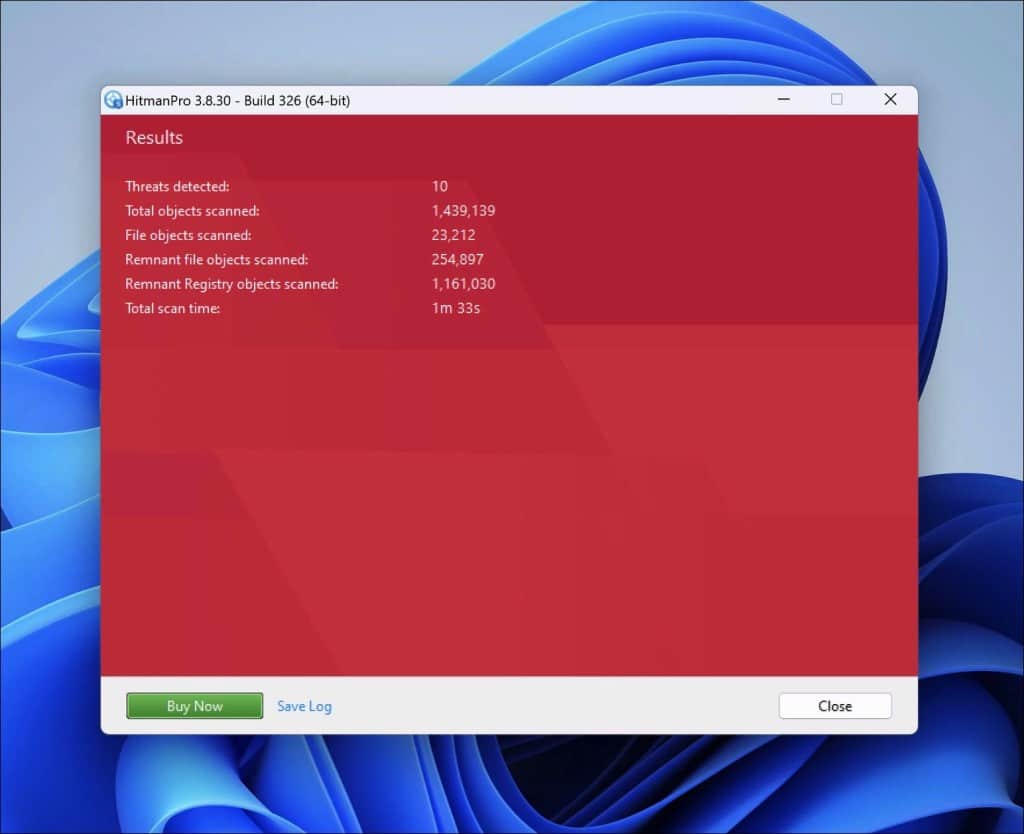
- Sophos HitmanPro will remove all detected malware from your computer. When it is done, you will see a summary of the results.
Adware removal tool by TSA
I have a suggestion that could become your computer’s new trusted ally: “Adware Removal Tool by TSA.” This useful tool acts like a versatile solution to address issues related to your web browser.
It is not limited to dealing with adware, but also effectively removes browser hijackers affecting Chrome, Firefox, Internet Explorer, and Edge. Additionally, it can eliminate cumbersome toolbars and malicious extensions, and even has a reset feature to revert your browser to its original state.
As an added bonus, it is portable and can be easily carried on a USB or recovery disk. To tidy up your digital environment, consider giving this accessible and user-friendly tool a try.
Download Adware Removal tool by TSA
Once you start the app, the adware removal tool updates its adware detection definitions. Next, click the “Scan” button to start an adware scan on your computer.
Follow the on-screen instructions to remove detected adware from your PC for free. Next, I advise installing Malwarebytes browser guard to prevent Check-tl-ver-294-3.com ads.
Malwarebytes browser guard
Malwarebytes Browser Guard is a browser extension. This browser extension is available for the most well-known browsers: Google Chrome, Firefox, and Microsoft Edge. When the Malwarebytes browser extension is used, the browser is protected against multiple online attacks—for example, phishing attacks, unwanted websites, malicious websites, and crypto miners.
I recommend installing Malwarebytes browser guard to be better protected against Check-tl-ver-294-3.com now and in the future.
- Download Malwarebytes browser guard.
- Click to install on the preferred browser.
When browsing online, and you might accidentally visit a malicious website, Malwarebytes browser guard will block the attempt, and you will receive a notice.
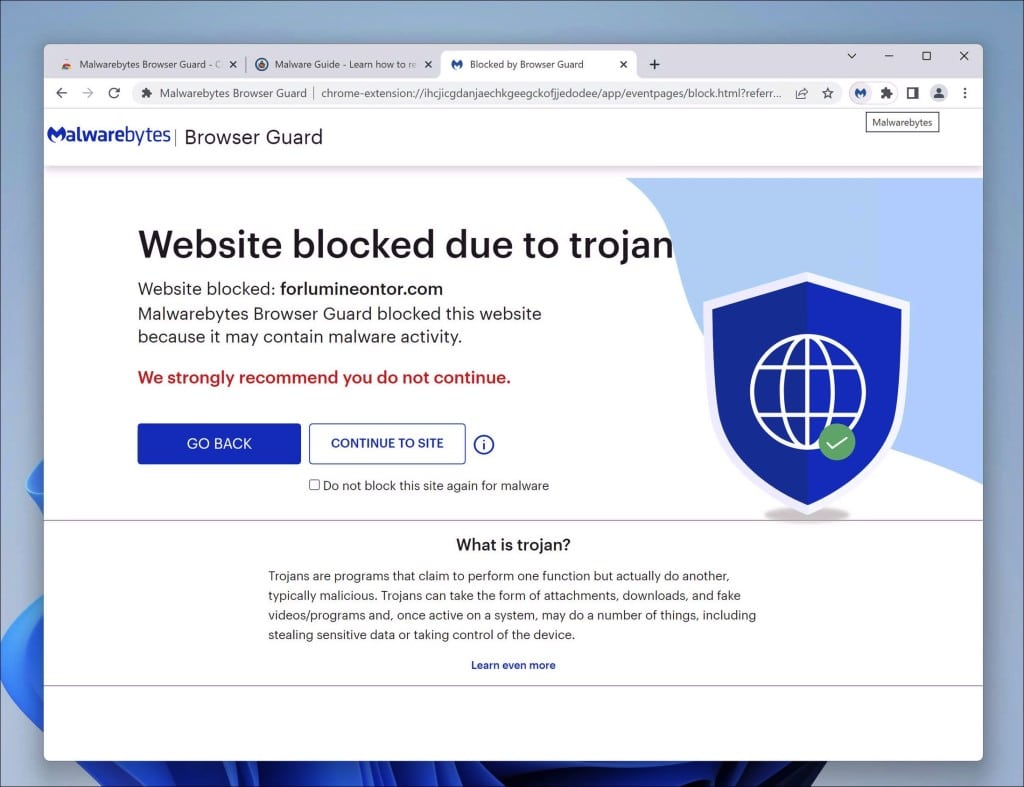
Spybot Search & Destroy
Spybot Search & Destroy is a security software that can safeguard your computer against spyware, adware and other harmful software. When you use Spybot Search & Destroy it actively scans your computers drive, memory and registry for any programs or unwanted software. Once it identifies these threats you can easily remove them.
The process begins when you initiate a scan. Spybot Search & Destroy carefully examines your system for any signs of malware paying attention to tracking cookies unwanted programs and web browser hijackers that can compromise your privacy and security.
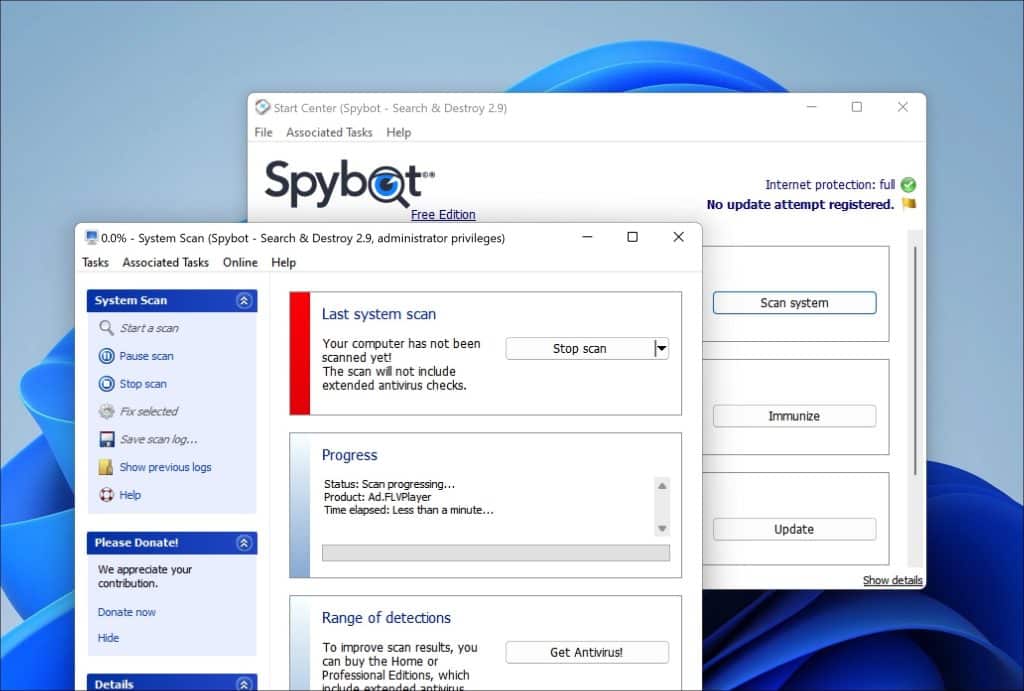
If it detects anything the software presents a list of these items, for your review.
To eliminate malware from your system you can select the items from the list. Instruct Spybot Search & Destroy to remove them. The software then takes action to clean your system by either deleting these items or isolating them in quarantine based on their nature and potential risk. This proactive approach prevents the malware from operating on your system or accessing your information.
Moreover Spybot Search & Destroy provides immunization features that fortify your systems defenses. By immunizing your system it blocks access to known websites. Prevents unauthorized installation of unwanted programs on your computer. This preventive measure effectively safeguards, against infections.
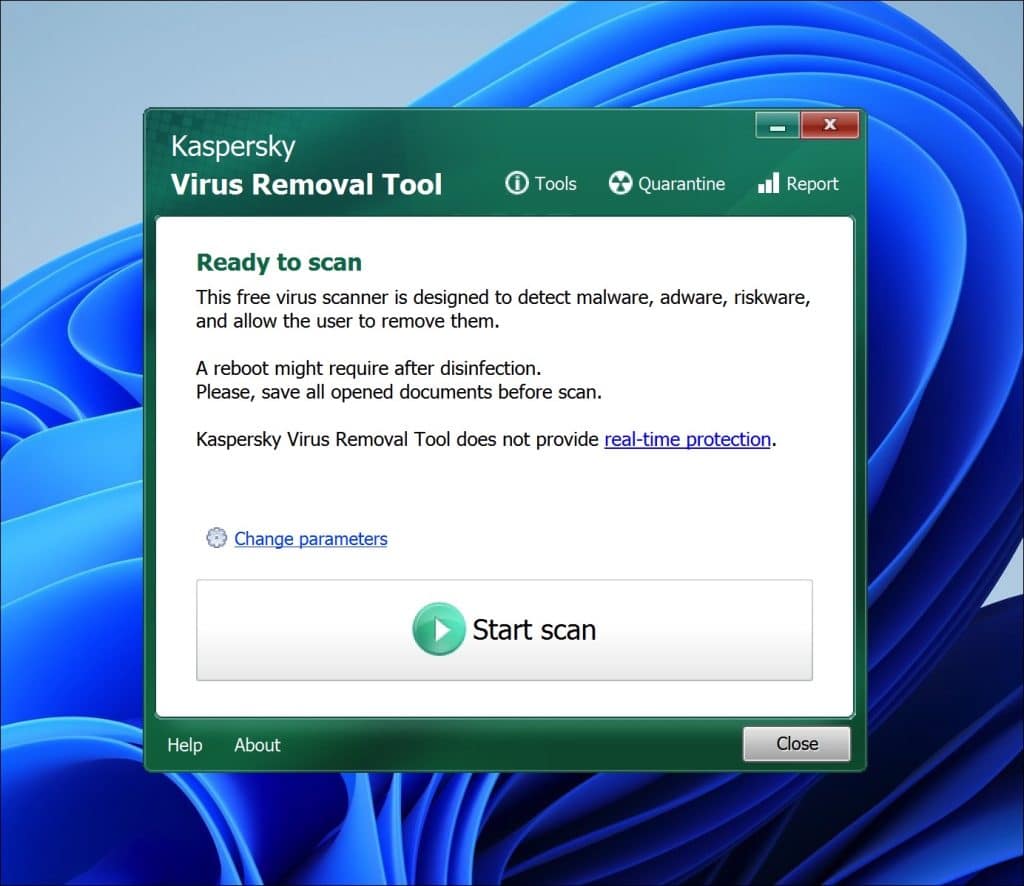
Kaspersky Virus Removal Tool
Kaspersky Virus Removal Tool is a tool that can help you scan and eliminate viruses, Trojans, worms, spyware and other malicious software from your computer. When you use this tool it conducts an examination of your system to uncover and isolate any threats.
After downloading and launching Kaspersky Virus Removal Tool it automatically updates its malware definitions to ensure that it can recognize the threats. You can then initiate a system scan by selecting areas of your computer for checking or opt for a scan that covers every part of your system.
While scanning your computer the tool utilizes detection algorithms developed by Kaspersky to identify malware and other harmful software. If any threats are detected they will be presented in a list with information, about each items nature and level of threat.
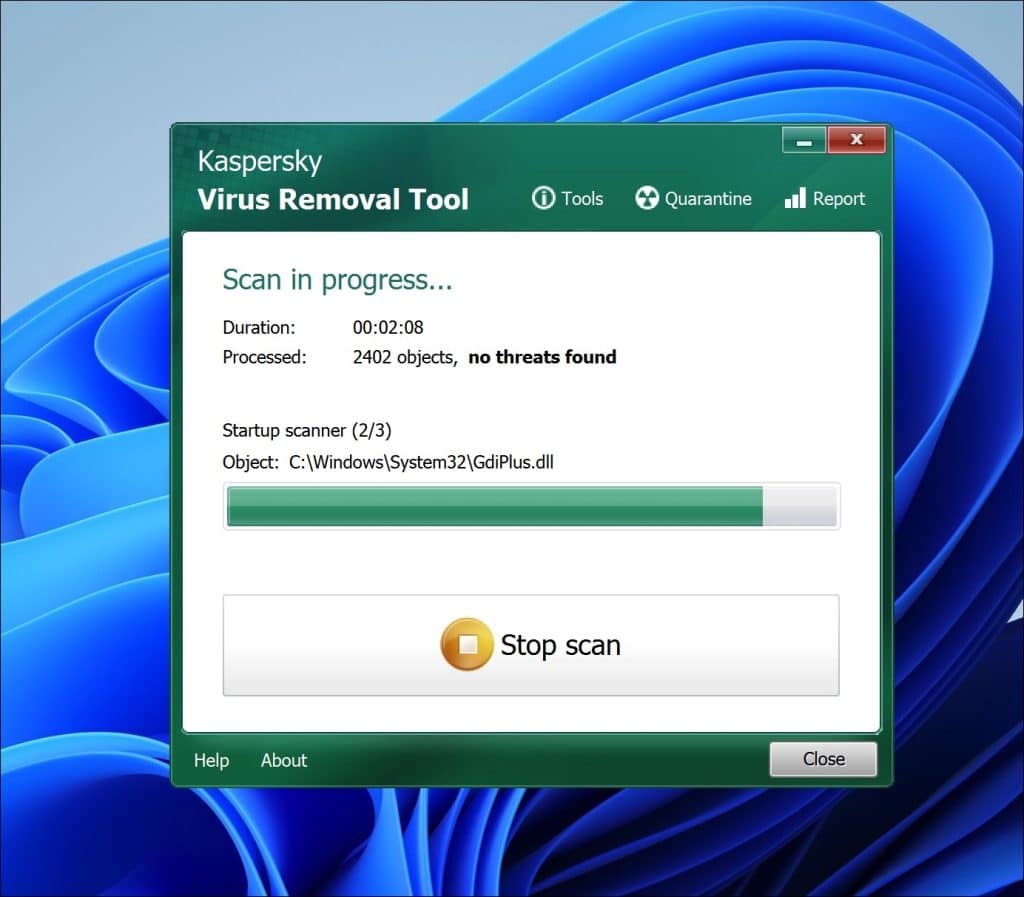
To eliminate the malware simply choose the items from the list. Select an action, for Kaspersky Virus Removal Tool to take—typically disinfection (attempting to remove the malware while keeping the infected file intact) deletion (completely removing the file) or quarantine (isolating the file to prevent harm to your system).Kaspersky Virus Removal Tool provides users with the choice of manual disinfection options depending on the severity of the infection and personal preference. Once the malware has been removed it recommends restarting your computer to ensure that the cleaning process is fully completed.
In this guide, you have learned how to remove Check-tl-ver-294-3.com. Also, you have removed malware from your computer and protected your computer against Check-tl-ver-294-3.com in the future. Thank you for reading!