There are two ways to remove Jiilyis.info Use my removal guide to help remove this malicious website.
So let me tell you in this article what is Jiilyis.info is and how it works and give simple steps to make the pop-up ads no longer appear on your screen or what to do to prevent the site from being a nuisance.
We’re going to explore specifics regarding this site, how it operates, and ways to eliminate the ads.
So what is Jiilyis.info?
It’s a deceptive website. It generates false error messages in your browser, making you think that clicking on “Allow Notifications” will remedy the problem. But once you access it, it inundates your device with lotsof little annoying, offensive pop-up ads. Certain advertisements may continue whether you are actively surfing the internet or not.
If you need help with regard to Jiilyis.info? You are misled. Jiilyis.info can be found being actively spread via malicious advertising networks and via redirects from either compromised or malicious websites attempting to trick victims to enable notifications.
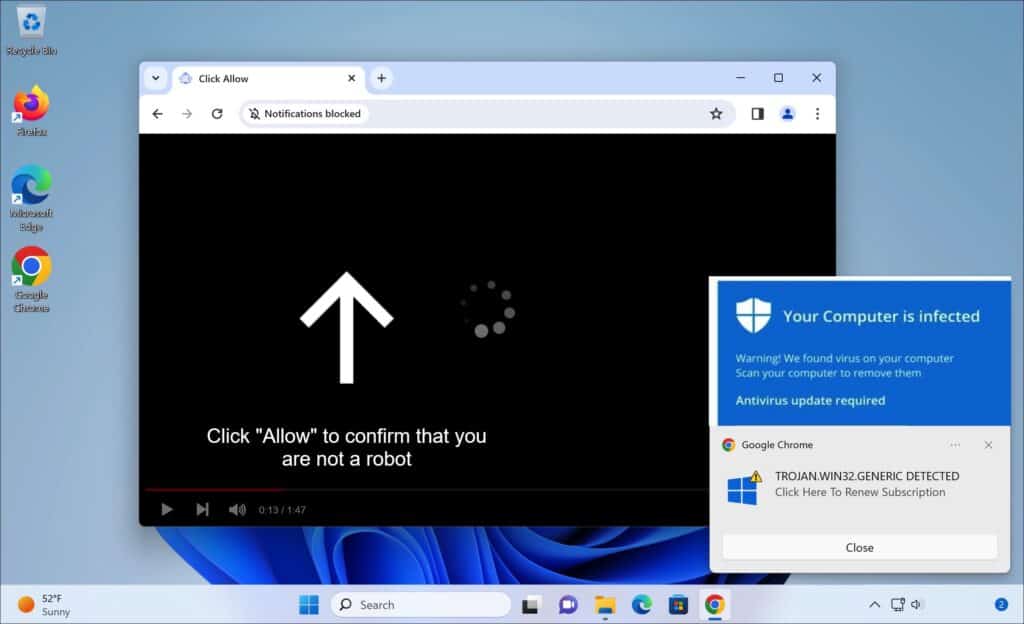
Here is some more information about the Jiilyis.info domain:
Jiilyis.info domain WHOIS record:
Domain Name: jiilyis.info
Registry Domain ID: 5ea9721f86ff460eae505c5bd97a8baa-DONUTS
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: http://www.namesilo.com
Updated Date: 2025-01-12T18:46:39Z
Creation Date: 2025-01-07T18:46:36Z
Registry Expiry Date: 2026-01-07T18:46:36Z
Registrar: NameSilo, LLC
Registrar IANA ID: 1479
Registrar Abuse Contact Email: abuse@namesilo.com
Registrar Abuse Contact Phone: +1.6024928198
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Name Server: carter.ns.cloudflare.com
Name Server: gigi.ns.cloudflare.com
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://icann.org/wicf/
>>> Last update of WHOIS database: 2025-08-01T16:04:41Z <<<
For more information on Whois status codes, please visit https://icann.org/epp
Terms of Use: Access to WHOIS information is provided to assist persons in determining the contents of a domain name registration record in the registry database. The data in this record is provided by Identity Digital or the Registry Operator for informational purposes only, and accuracy is not guaranteed. This service is intended only for query-based access. You agree that you will use this data only for lawful purposes and that, under no circumstances will you use this data to (a) allow, enable, or otherwise support the transmission by e-mail, telephone, or facsimile of mass unsolicited, commercial advertising or solicitations to entities other than the data recipient's own existing customers; or (b) enable high volume, automated, electronic processes that send queries or data to the systems of Registry Operator, a Registrar, or Identity Digital except as reasonably necessary to register domain names or modify existing registrations. When using the Whois service, please consider the following: The Whois service is not a replacement for standard EPP commands to the SRS service. Whois is not considered authoritative for registered domain objects. The Whois service may be scheduled for downtime during production or OT&E maintenance periods. Queries to the Whois services are throttled. If too many queries are received from a single IP address within a specified time, the service will begin to reject further queries for a period of time to prevent disruption of Whois service access. Abuse of the Whois system through data mining is mitigated by detecting and limiting bulk query access from single sources. Where applicable, the presence of a [Non-Public Data] tag indicates that such data is not made publicly available due to applicable data privacy laws or requirements. Should you wish to contact the registrant, please refer to the Whois records available through the registrar URL listed above. Access to non-public data may be provided, upon request, where it can be reasonably confirmed that the requester holds a specific legitimate interest and a proper legal basis for accessing the withheld data. Access to this data provided by Identity Digital can be requested by submitting a request via the form found at https://www.identity.digital/about/policies/whois-layered-access/. The Registrar of Record identified in this output may have an RDDS service that can be queried for additional information on how to contact the Registrant, Admin, or Tech contact of the queried domain name. Identity Digital Inc. and Registry Operator reserve the right to modify these terms at any time. By submitting this query, you agree to abide by this policy.
Jiilyis.info domain age:
0 years, 6 months, 24 days
What kind of pop-up ads does Jiilyis.info trigger?
Fake System Warnings — This one is the classic trick to turn on your push notifications on your browser. It may warn, for instance, that your browser is out of date and in need of an update — falsely.
Obnoxious Ads: The site bombards your device with unwanted inappropriate ads as soon as you go ahead and turn on notifications. These may range from adult content and dating site promotional material to phony software update scams and dubious products.
How it in bypassed your pop up blockers: By tricking you into accepting push notifications like Jiilyis.info can bypass the pop-up blockers in your browser. That means it can send ads directly to your device, even if you enable a pop-up blocker.
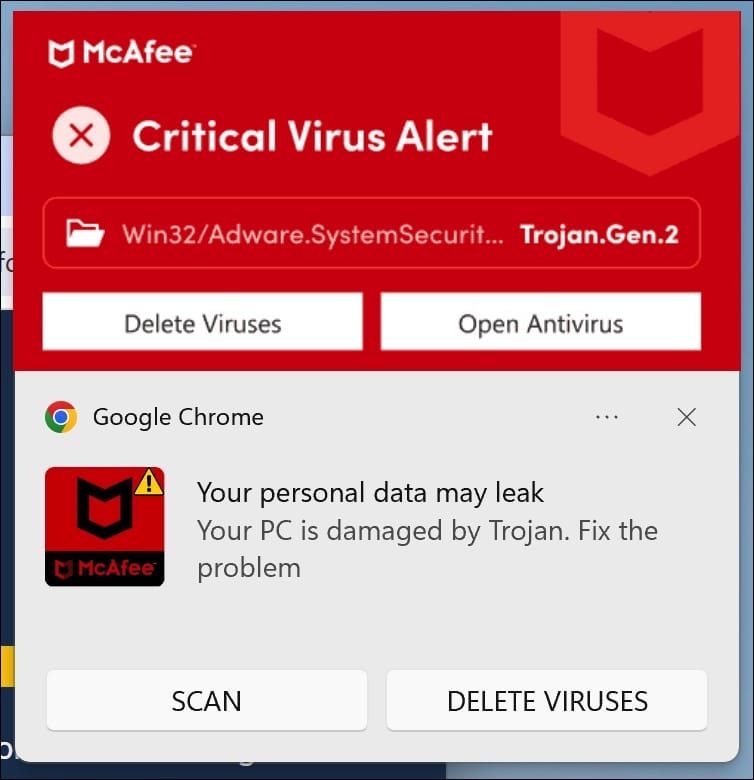
Why am I seeing these unwanted ads?
You will see a lot of pop-ups from Jiilyis.info. This probably occurred since you mistakenly turned on push alerts for that internet site. They may have deceived you in the following ways:
Showing fake error messages. These in make you think enabling notifications is mandatory.
Be secretly sneaky about hiding notification requests. So without knowing, you agreed.
Redirecting unexpectedly. Sometimes it takes you there from some external site or pop-up.
Like with software installs. Free programs sometimes bundle Jiilyis.info, allowing notifications to be turned on in secret.
Falsely claiming virus. It might say your computer’s infected and alerts eliminate “malware.”
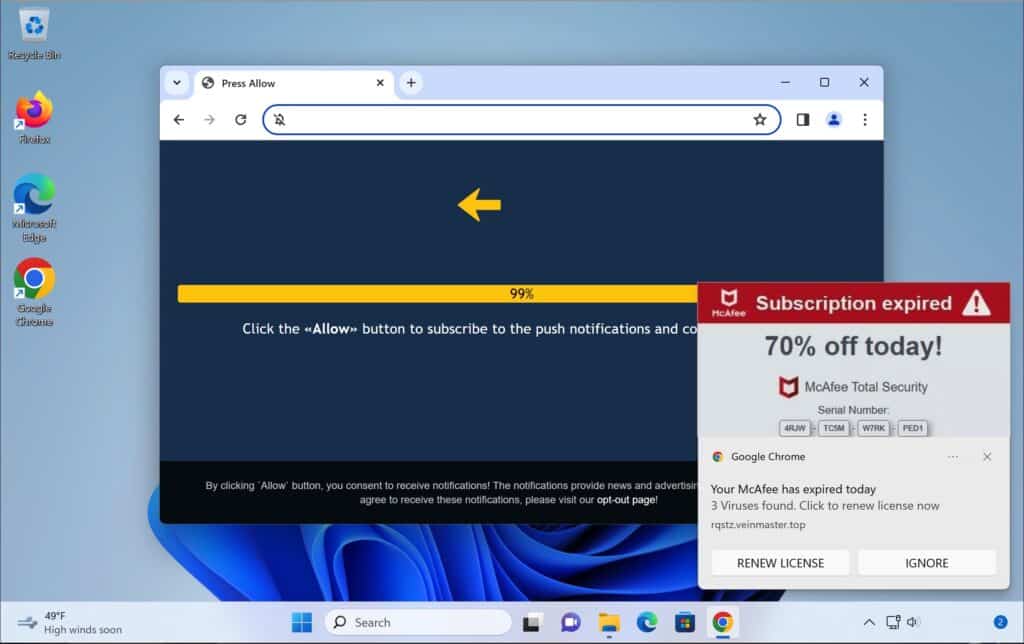
This guide aims to help you identify and remove any unwanted software and potential malware related to Jiilyis.info from your computer.
To start with, inspect your browsers if you had implicitly authorized Jiilyis.info.
Check the installed applications in Windows 10 or 11 to exclude any related threats.
There are special tools that will be able to identify negative software in your system and destroy the threats. Such tools are advised to use in this process.
After working through this guide, you should consider you a reputable browser-based extension as it helps you to fight adware invasions and block dangerously malicious pop-ups as like that of Jiilyis.info.
How to remove Jiilyis.info?
Adware, malicious software, and unwanted applications can clutter your computer, compromising performance and security. This guide aims to walk you through a systematic process to clean your computer from such threats, especially those associated with pesky domains like Jiilyis.info.
Step 1: Remove permission for Jiilyis.info to send push notifications using the browser
First, we’ll withdraw access to Jiilyis.info from your browser settings. This action will halt Jiilyis.info from dispatching additional notifications to your browser. After finalizing this step, you won’t see any more intrusive ads from Jiilyis.info.
Make sure to follow the steps below.
Follow the steps from the internet browser you use on your device, and select your standard browser.
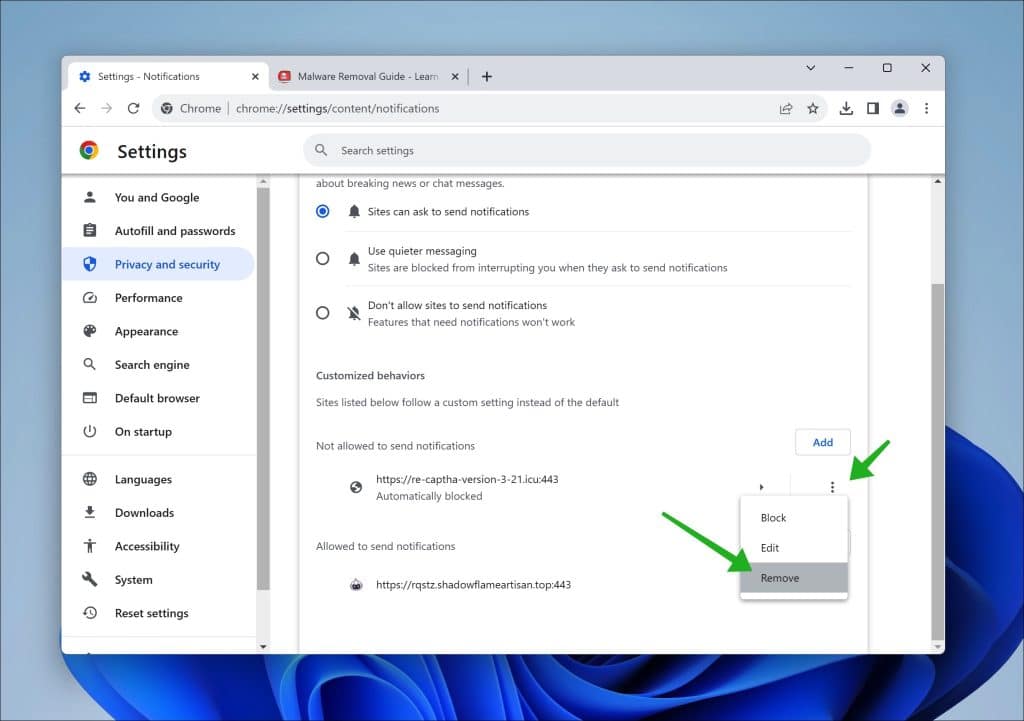
 Remove Jiilyis.info from the Google Chrome browser
Remove Jiilyis.info from the Google Chrome browser
- Open Google Chrome.
- Click on the three vertical dots in the top right corner to open the menu.
- Select “Settings.”
- On the left, click on “Privacy and security.”
- Click on “Site Settings.”
- Scroll down to “Permissions” and select “Notifications.”
- Under the “Allow” section, find and click on the Jiilyis.info entry.
- Click on the three vertical dots next to the entry and choose “Remove”.
→ Go to the next step: Malwarebytes.
 Remove Jiilyis.info from the Android browser
Remove Jiilyis.info from the Android browser
- Open the “Settings” app on your Android device.
- Scroll down and tap on “Apps & notifications” or just “Apps,” depending on your device.
- Tap on “See all apps” if you don’t see the browser you use in the initial list.
- Find and tap on your browser app where you’re receiving the notifications (e.g., Chrome, Firefox).
- Tap on “Notifications.”
- Under the “Sites” or “Categories” section, find Jiilyis.info.
- Turn off the toggle next to it to block notifications.
If it doesn’t work, try the following for Google Chrome on Android.
- Open the Chrome app.
- Tap on the three vertical dots in the top-right corner to open the menu.
- Tap on “Settings.”
- Scroll down and tap on “Site Settings.”
- Tap on “Notifications.”
- Under the “Allowed” section, you will see Jiilyis.info if you’ve permitted it.
- Tap on Jiilyis.info, then turn off the “Notifications” toggle.
→ Go to the next step: Malwarebytes.
 Remove Jiilyis.info from the Firefox browser
Remove Jiilyis.info from the Firefox browser
- Open Mozilla Firefox.
- Click on the three horizontal lines in the top right corner to open the menu.
- Select “Options.”
- Click on “Privacy & Security” in the left sidebar.
- Scroll down to the “Permissions” section and click on “Settings” following “Notifications.”
- Locate Jiilyis.info in the list.
- In the drop-down menu next to its name, select “Block.”
- Click “Save Changes.”
→ Go to the next step: Malwarebytes.
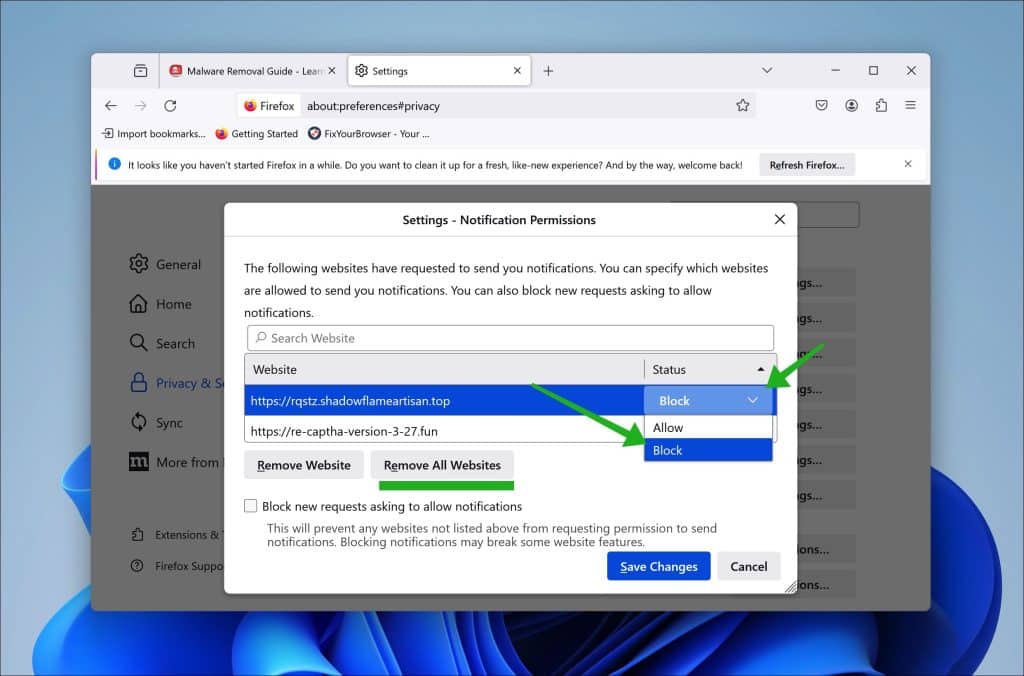
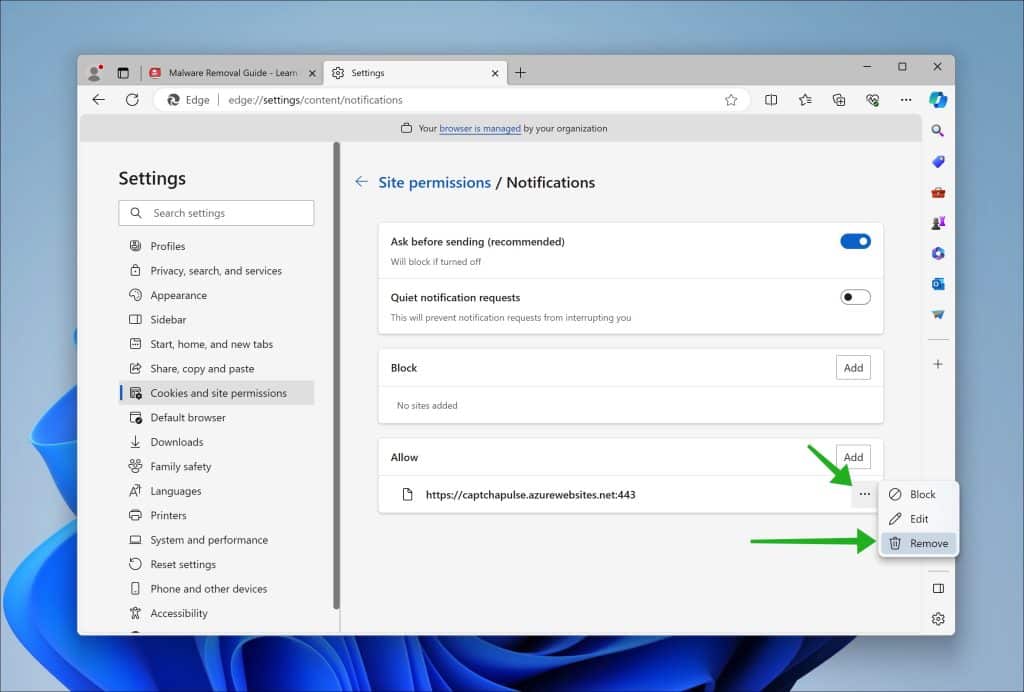
 Remove Jiilyis.info from the Microsoft Edge browser
Remove Jiilyis.info from the Microsoft Edge browser
- Open Microsoft Edge.
- Click on the three horizontal dots in the top right corner.
- Select “Settings.”
- Under “Privacy, search, and services,” click on “Site permissions.”
- Select “Notifications.”
- Under the “Allow” section, find the Jiilyis.info entry.
- Click on the three horizontal dots next to the entry and select “Block.”
→ Go to the next step: Malwarebytes.
 Remove Jiilyis.info from Safari on Mac browser
Remove Jiilyis.info from Safari on Mac browser
- Open Safari.
- In the top menu, click “Safari” and choose “Preferences.”
- Go to the “Websites” tab.
- In the left sidebar, select “Notifications.”
- Locate Jiilyis.info in the list.
- In the drop-down menu next to its name, select “Deny.”
→ Go to the next step: Malwarebytes.
Step 2: Remove adware browser extensions
Web browsers are extensively used for gathering information, communication, work, and leisure activities. Extensions enhance these tasks by providing additional functionality. However, it is crucial to exercise caution as not all extensions are benign. Some may attempt to obtain your personal data, display advertisements, or redirect you to malicious websites.
Identifying and removing such extensions is essential for safeguarding your security and ensuring a smooth browsing experience. This guide outlines the process of removing extensions from popular web browsers like Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari. By following the steps provided for each browser, you can enhance your browsing safety and improve the overall user experience.
 Google Chrome browser
Google Chrome browser
- Open Google Chrome.
- type: chrome://extensions/ in the address bar.
- Search for any adware browser extensions and click the “Remove” button.
It is important to check every extension installed. If you do not know or do not trust a specific extension, remove or disable it.
→ See the next step: Malwarebytes.
 Firefox browser
Firefox browser
- Open Firefox browser.
- type: about:addons in the address bar.
- Search for any adware browser add-ons and click the “Uninstall” button.
It is important to check every add-on that is installed. If you do not know or do not trust a specific addon, remove or disable it.
→ See the next step: Malwarebytes.
 Microsoft Edge browser
Microsoft Edge browser
- Open the Microsoft Edge browser.
- type: edge://extensions/ in the address bar.
- Search for any adware browser extensions and click the “Remove” button.
It is important to check every extension installed. If you do not know or do not trust a specific extension, remove or disable it.
→ See the next step: Malwarebytes.
 Safari browser
Safari browser
- Open Safari.
- In the top left corner, click on the Safari menu.
- In the Safari menu, click on Preferences.
- Click on the Extensions tab.
- Click on the unwanted extension you want to be removed, then Uninstall.
→ See the next step: Malwarebytes.
It is important to check every extension installed. If you do not know or trust a specific extension, uninstall it.
Step 3: Uninstall adware software
Ensuring your computer is free from unwanted software like adware is crucial. Adware programs often hitchhike alongside legitimate applications you install from the internet.
They can slip in unnoticed during installation if you hastily click through prompts. This deceptive practice sneaks adware onto your system without explicit consent. To prevent this, tools like Unchecky can help you scrutinize each step, allowing you to opt out of bundled software. Following the steps below, you can scan for existing adware infections and remove them, regaining control over your device.
In this second phase, we’ll thoroughly inspect your computer for any adware that may have crept in. While you might inadvertently install such programs yourself when obtaining free software online, their presence is often masked as “helpful tools” or “offerings” during the setup process.
If you’re not vigilant and breeze through installation screens, adware can quietly embed itself on your system. However, by exercising caution and employing utilities like Unchecky, you can avoid this underhanded bundling and keep your machine clean. Let’s proceed to detect and eliminate any adware currently residing on your computer.
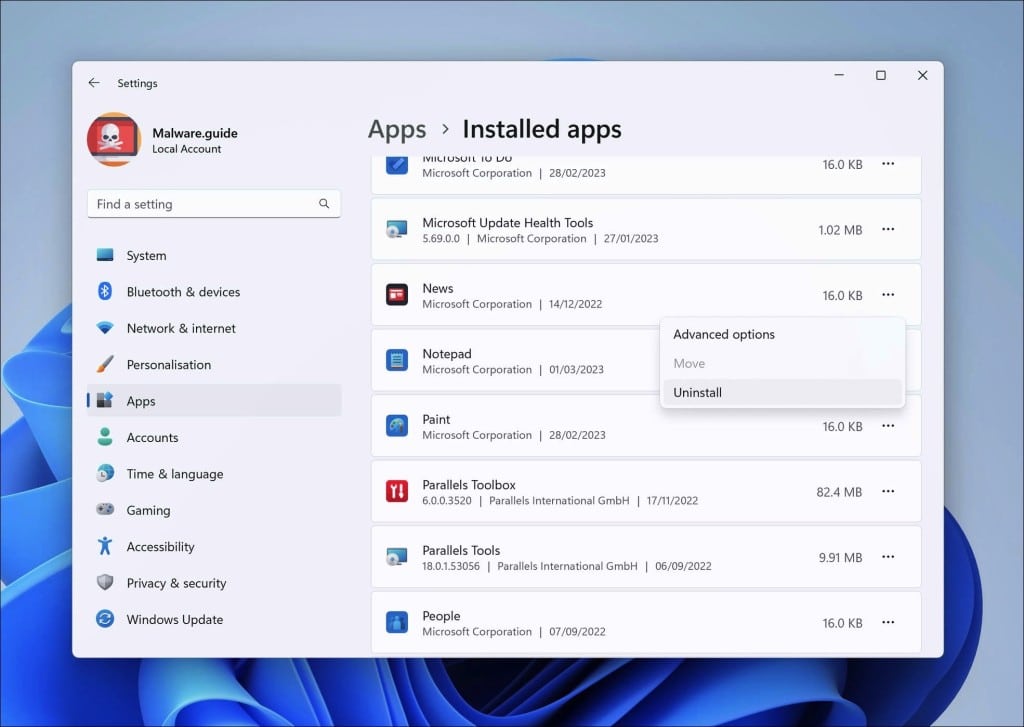
Windows 11
- Click on “Start.”
- Click on “Settings.”
- Click on “Apps.”
- Lastly, click on “Installed apps.”
- Search for any unknown or unused software in the list of recently installed apps.
- On the right-click on the three dots.
- In the menu, click on “Uninstall.”
→ See the next step: Malwarebytes.
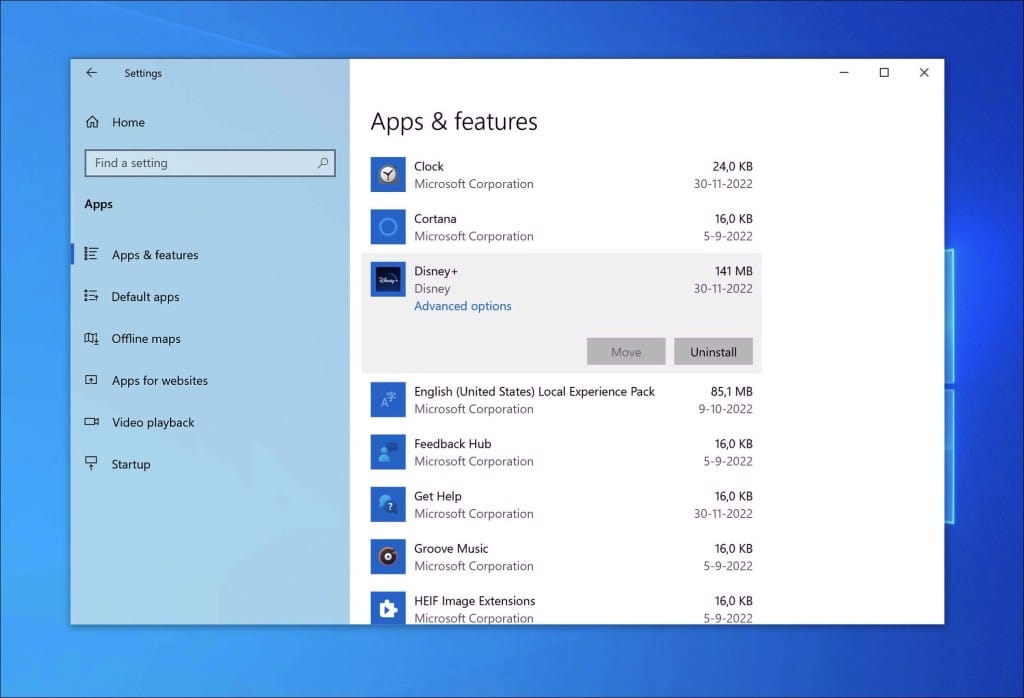
Windows 10
- Click on “Start.”
- Click on “Settings.”
- Click on “Apps.”
- In the list of apps, search for any unknown or unused software.
- Click on the app.
- Lastly, click on the “Uninstall” button.
→ See the next step: Malwarebytes.
Step 4: Scan your PC for malware
Alright, now it is time to remove malware from your PC automatically. Using Malwarebytes, you can quickly scan your computer, review detections, and safely remove them from your PC.
Malwarebytes
Malwarebytes is the best – and most used – malware removal tool available today. It can detect all sorts of malware, such as adware, browser hijackers, and spyware. If it detects any malware on your computer, you can use it to remove it for free. Try it and see for yourself.
- Download Malwarebytes
- Install Malwarebytes, and follow the on-screen instructions.
- Click Scan to initiate a malware scan on your PC.
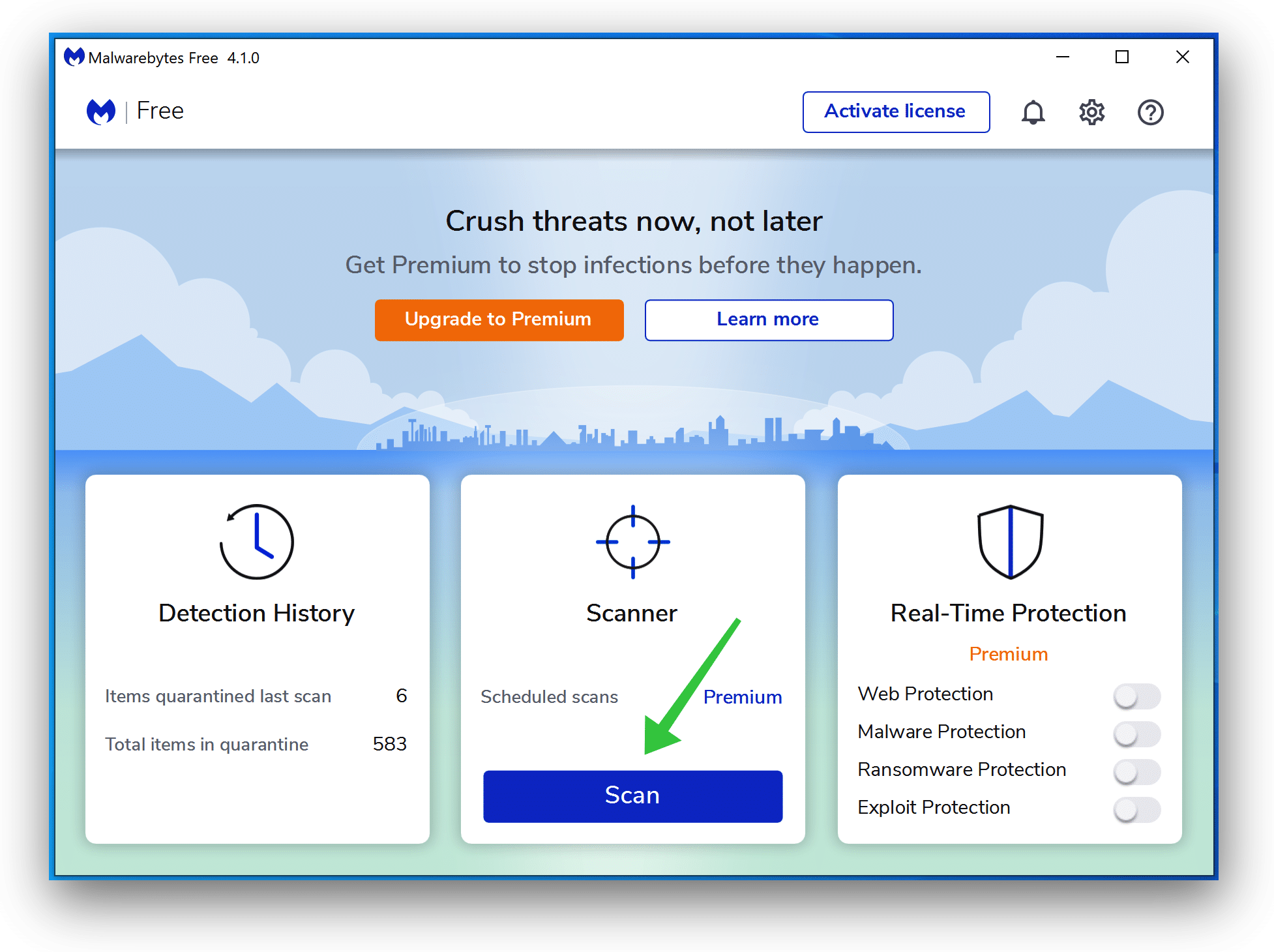
- Wait for the Malwarebytes scan to finish.
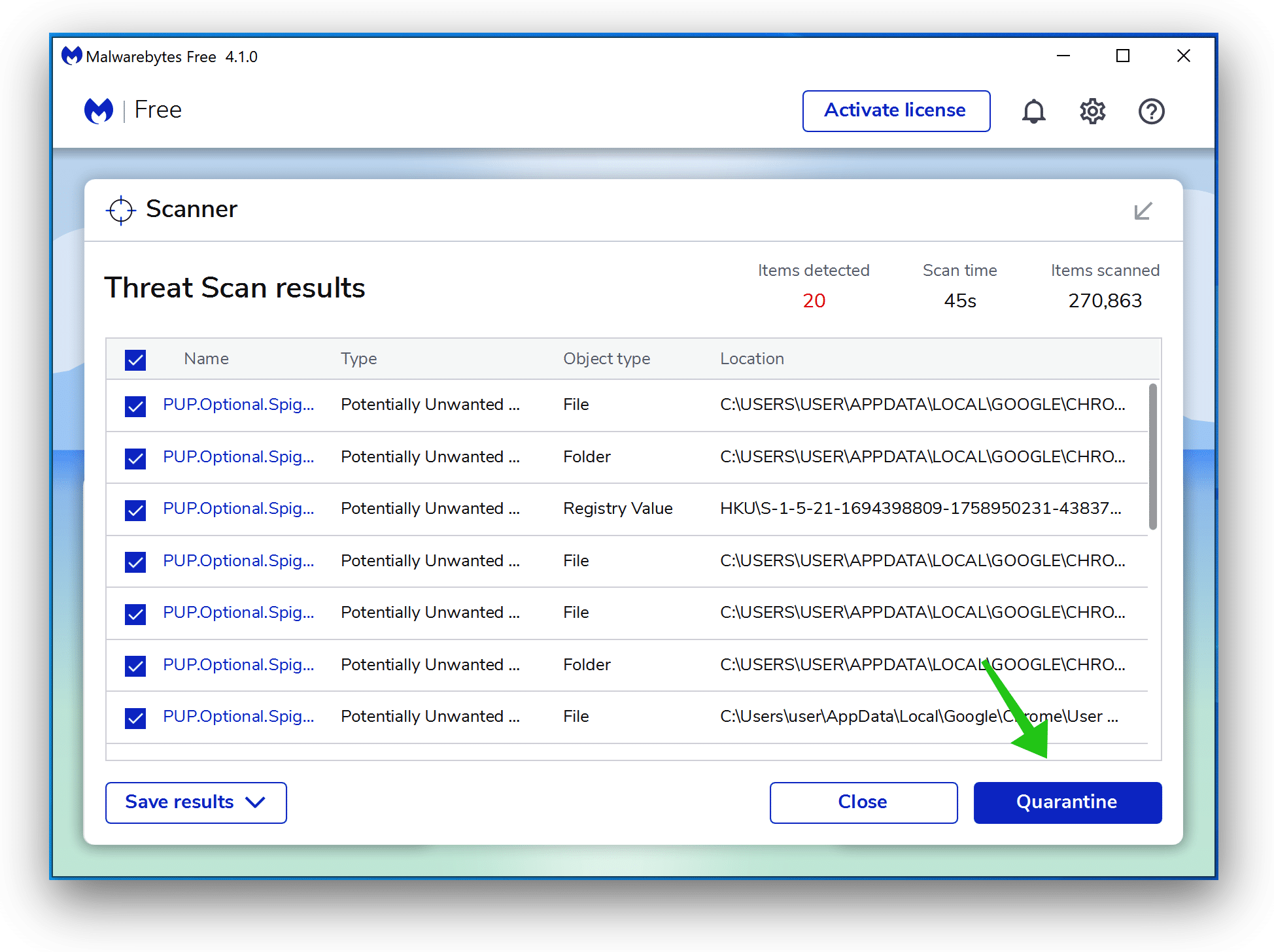
- Once completed, review the malware detections.
- Click Quarantine to continue.
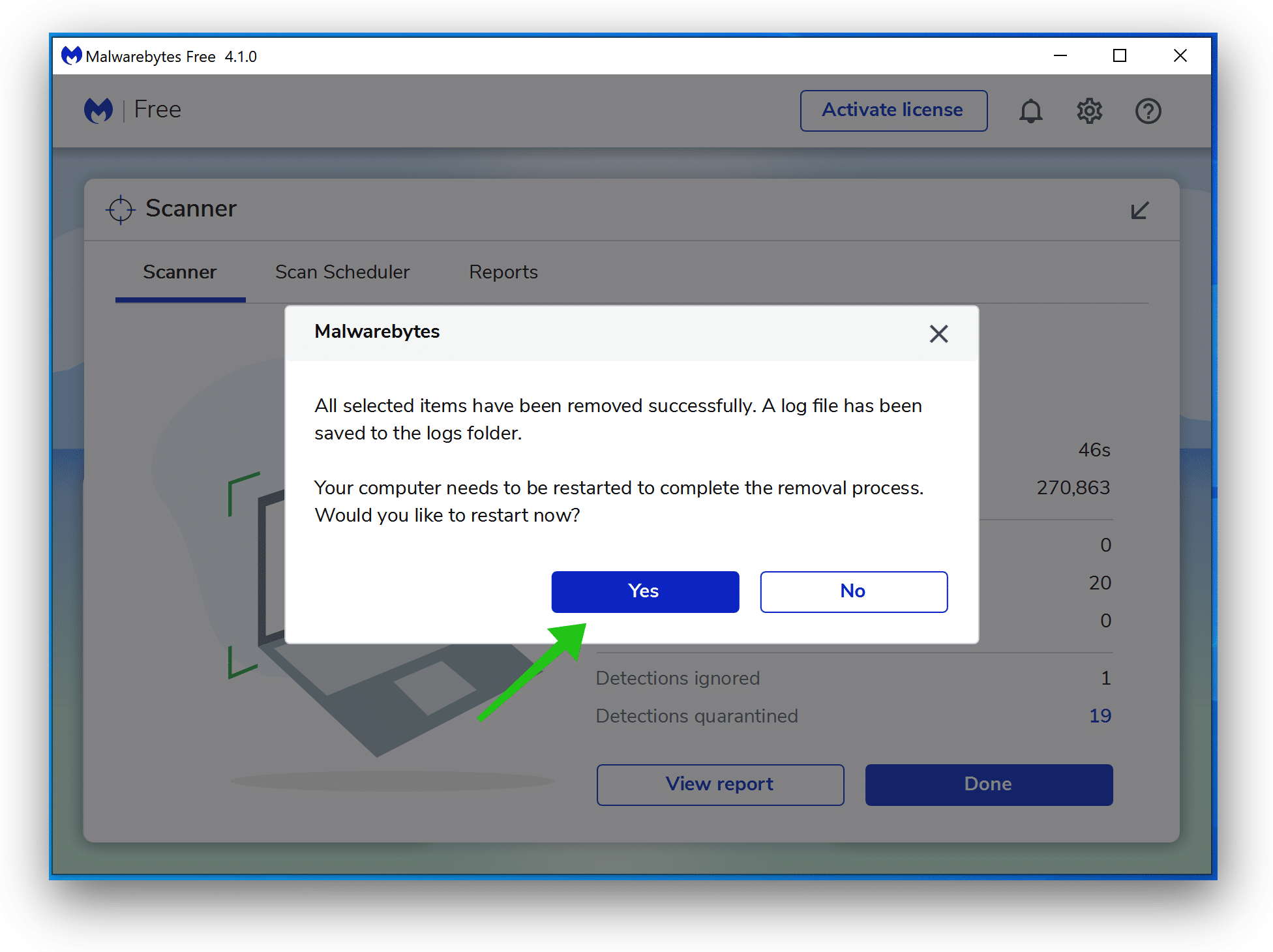
- Reboot Windows after all the malware detections are moved to quarantine.
Combo Cleaner
Combo Cleaner is a cleaning and antivirus program for Mac, PC, and Android devices. It is equipped with features to protect devices from various types of malware, including spyware, trojans, ransomware, and adware. The software includes tools for on-demand scans to remove and prevent malware, adware, and ransomware infections. It also offers features like a disk cleaner, big files finder (free), duplicate files finder (free), privacy scanner, and application uninstaller.
Follow the installation instructions to install the application on your device. Open Combo Cleaner after installation.
- Click the "Start scan" button to initiate a malware removal scan.
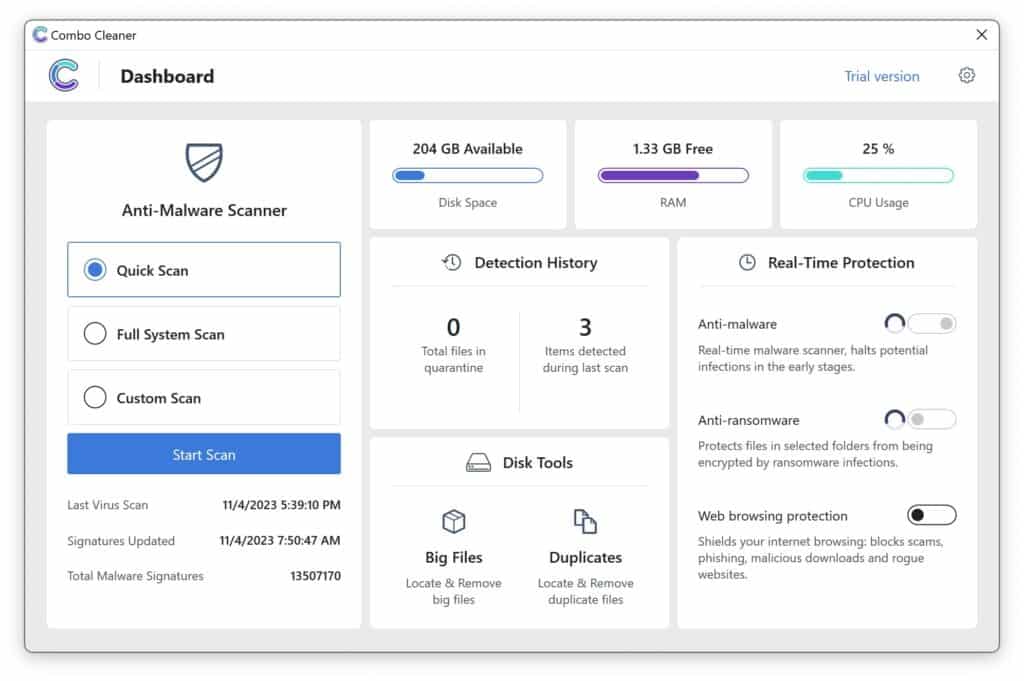
- Wait for Combo Cleaner to detect malware threats on your computer.
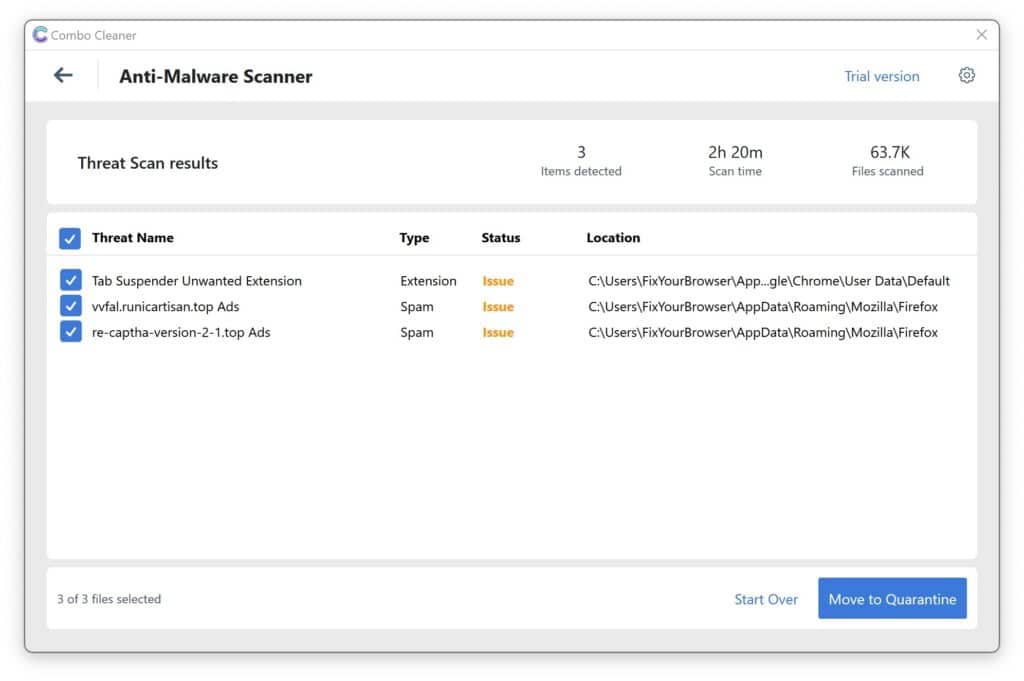
- When the Scan is finished, Combo Cleaner will show the found malware.
- Click "Move to Quarantine" to move the found malware to quarantine, where it can't harm your computer anymore.
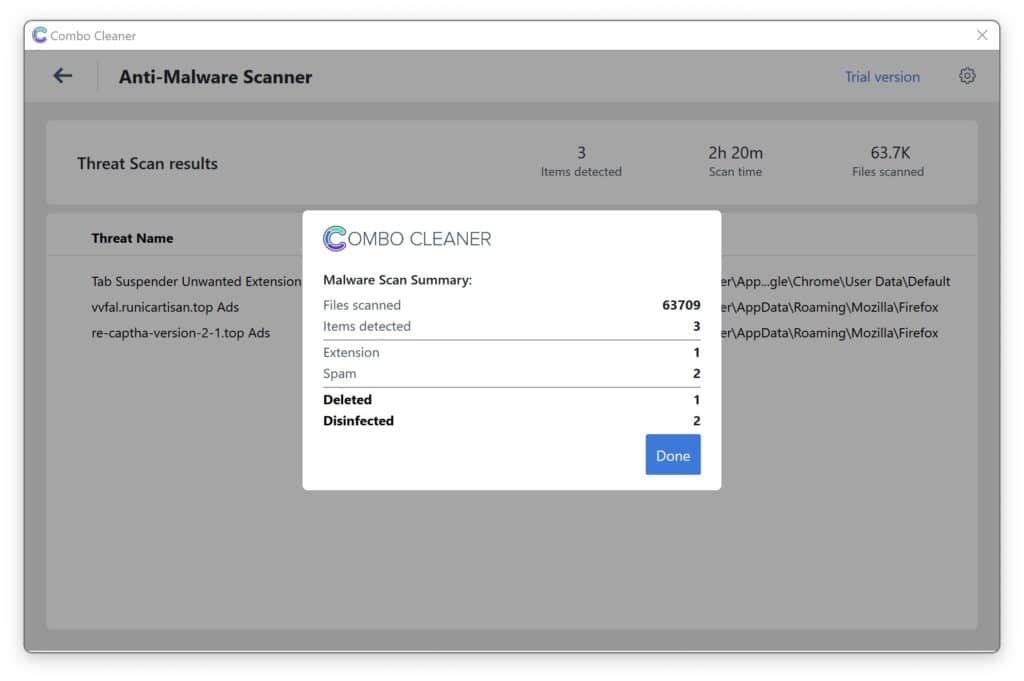
- A malware scan summary is shown to inform you about all threats found.
- Click "Done" to close the scan.
Use Combo Cleaner regularly to keep your device clean and protected. Combo Cleaner will remain active on your computer to protect your computer from future threats that try to attack your computer. If you have any questions or issues, Combo Cleaner offers a dedicated support team available 24/7.
Thank me later 😍 Please support my work and share this instruction with others so they do not become victims of Jiilyis.info.