In computing, encountering unknown processes or file names is quite a regular occurrence that can lead to certain apprehensions for users. Conhost.exe is one such file that commonly confuses. In this comprehensive guide, we will explore the essence of Conhost.exe, its functional role in your computer system, and the potential necessity of its removal.
What is Conhost.exe?
Conhost.exe, short for Console Host, is a legitimate system process in the Windows operating system. It manages, and hosts command prompt windows (cmd.exe) or console-based applications.
Conhost.exe is an intermediary between the console application and the Windows graphical user interface (GUI). It handles tasks such as rendering text, handling keyboard input, managing window resizing, and providing a bridge for communication between the console application and the operating system.
When you launch a command prompt window or run a console-based application, Conhost.exe provides the necessary environment to run and interact with the user. It ensures that the console window appears correctly on the screen, handles user input, and manages the underlying console functionalities.
Conhost.exe is typically located in the “C:\Windows\System32” directory on Windows systems. It is a critical system process and is not considered malware. However, as with any executable file, it’s important to ensure the authenticity and legitimacy of the Conhost.exe file running on your system. To verify its legitimacy, you can check the file location, digital signature, and scan your system with reputable antivirus software.
Is Conhost.exe malware?
No, Conhost.exe is not malware. It is a legitimate system process in the Windows operating system responsible for hosting and managing command prompt windows (cmd.exe) or console-based applications.
However, it’s important to exercise caution and ensure the authenticity of the Conhost.exe file running on your system. Malware authors may use names similar to legitimate processes to deceive users.
How to remove Conhost.exe?
Generally speaking, it’s not necessary to delete Conhost.exe from your system. It is a crucial part of particular software, and its removal could disrupt its licensing and activation procedures.
Nonetheless, adopting some protective measures is recommended if you observe any strange activities or have reasons to believe that the file might have been tampered with. Here are a few actions you could consider:
- Employ a trustworthy security application like Malwarebytes to scan your system for potential threats like viruses and malware.
- Ensure your software is updated to the most recent version. Conhost.exe regularly issues updates to mend security loopholes and enhance software performance.
- If you continue to doubt the authenticity of Conhost.exe, don’t hesitate to contact their customer support. They are equipped to provide necessary guidance and help authenticate the file’s integrity.
Bear in mind that any alteration or deletion of key system files could yield undesired outcomes and potentially hinder the operation of your software. As such, it’s crucial to proceed with caution and seek expert advice if you find yourself in a state of uncertainty.
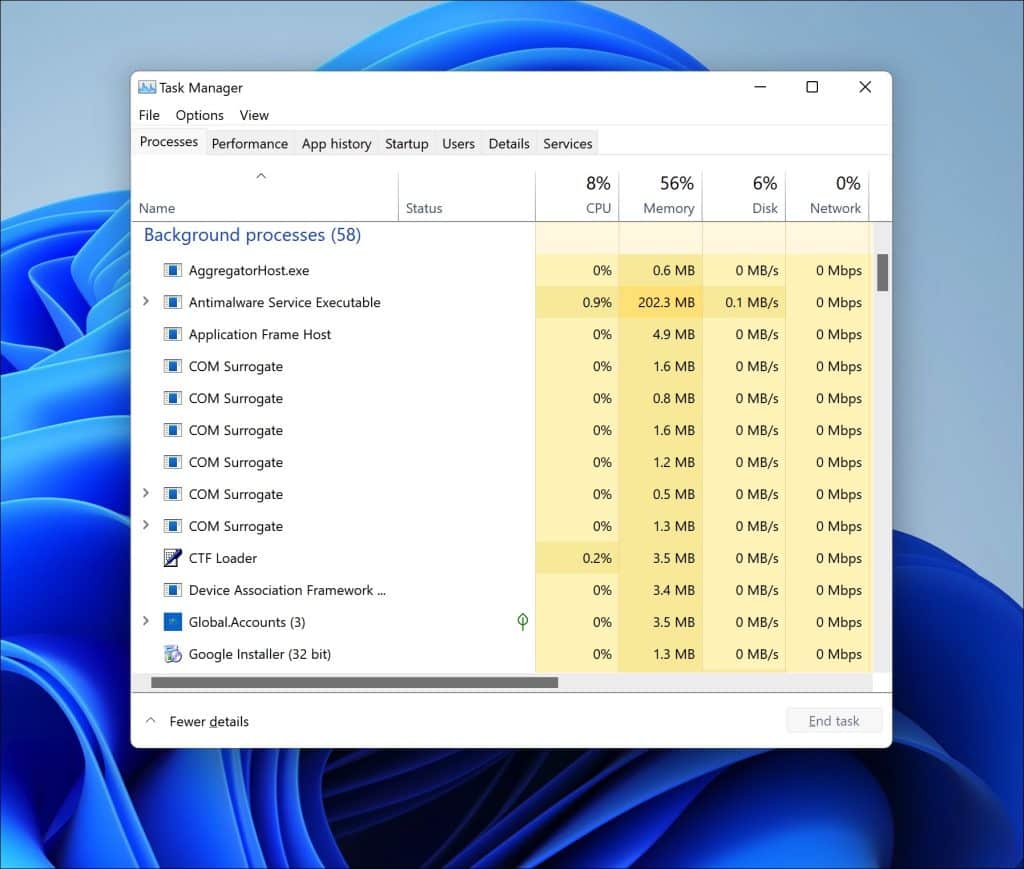
What are common issues with Conhost.exe?
Conhost.exe is generally a stable Windows software component, but like any program, it can occasionally encounter issues. Some of the common issues users might experience with Conhost.exe include:
Conhost.exe High CPU Usage
This file might sometimes use unusually high CPU resources, which could slow down your system. This might be due to outdated software or temporary glitches in the system.
Conhost.exe Error Messages
Users might encounter error messages related to Conhost.exe, resulting from issues with the software, connectivity problems, or even outdated software.
Conhost.exe potential security threats
In some rare instances, malware or viruses may disguise themselves as Conhost.exe. If the file is located outside the regular folder or exhibits suspicious behavior, it might be a security threat.
Conhost.exe Conflicts
Conflicts with other software or system processes could sometimes cause issues with Conhost.exe, leading to system instability or crashes.
What if I do not trust Conhost.exe?
Suppose you do not trust Conhost.exe. Try to scan your computer for any potential malware that might have been installed without your consent.
Malwarebytes anti-malware is an essential tool in the fight against malware. Malwarebytes can remove many types of potential Conhost.exe malware that other software does often miss. Malwarebytes is costing you absolutely nothing. When cleaning up an infected computer, Malwarebytes has always been free, and I recommend it as an essential tool in the battle against malware.
Install Malwarebytes, and follow the on-screen instructions.
Click Scan to start a malware scan.
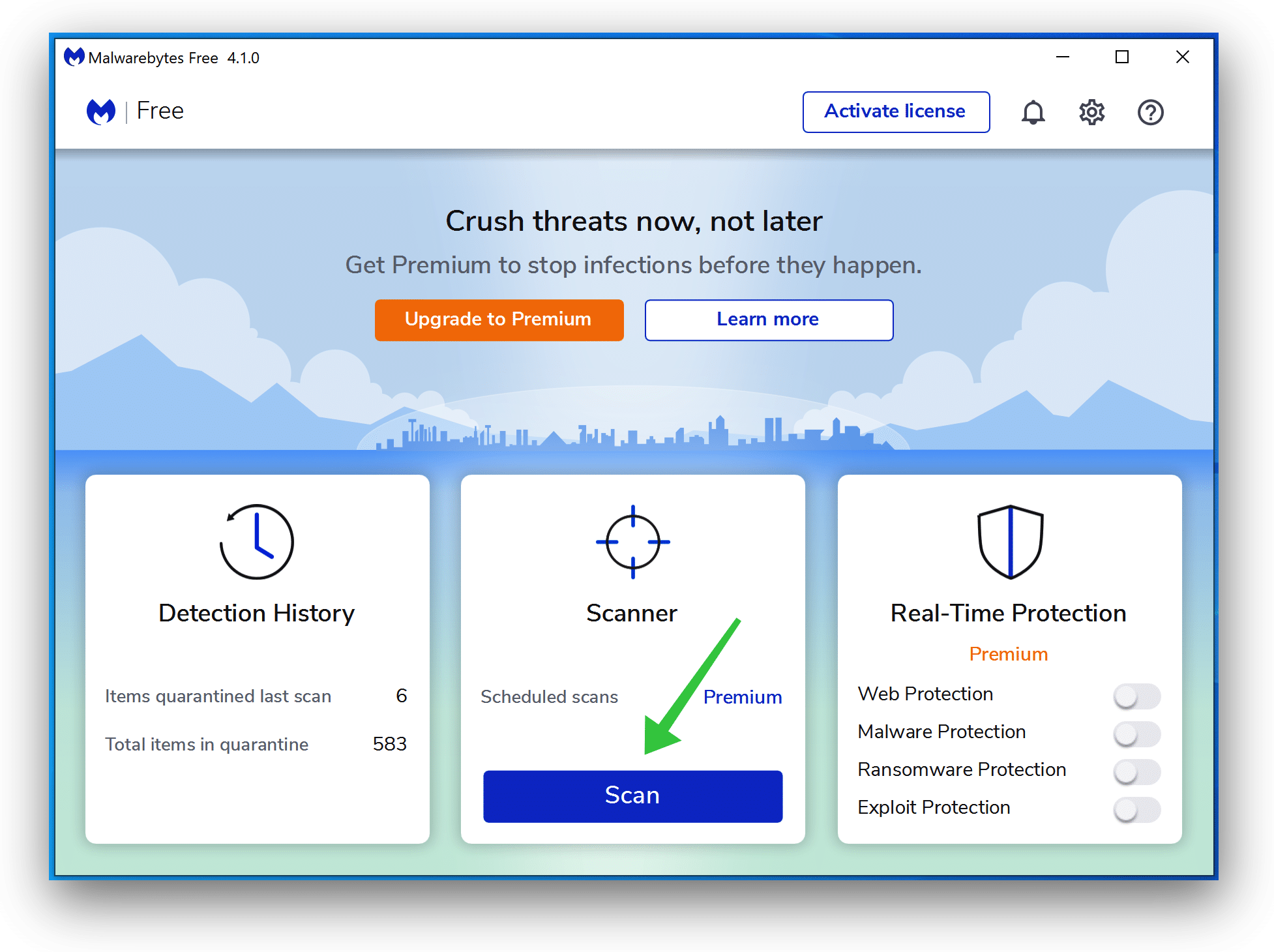
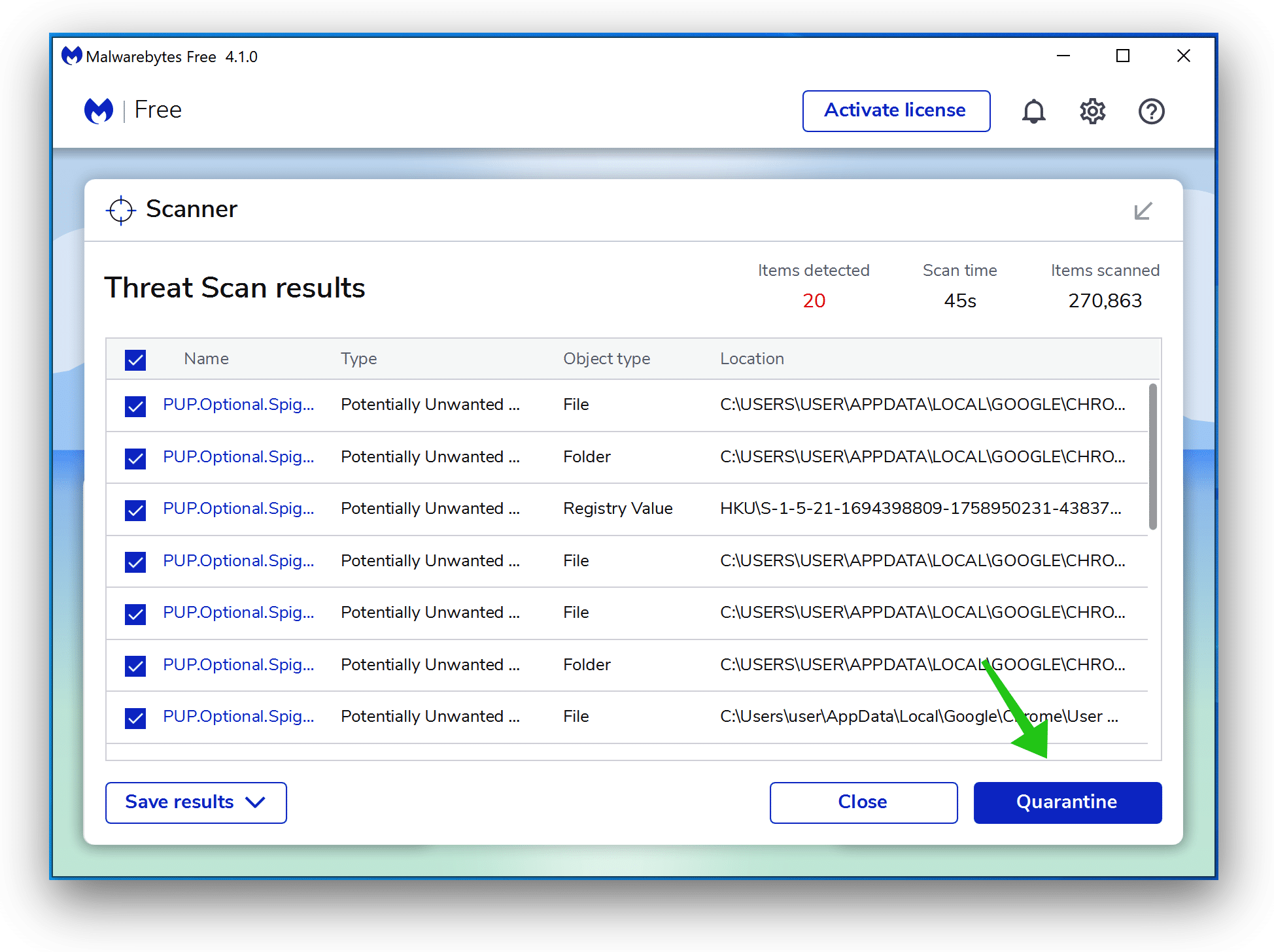
Wait for the Malwarebytes scan to finish. Once completed, review the Conhost.exe detections.
Click Quarantine to continue.
Reboot Windows after all the adware detections are moved to quarantine.
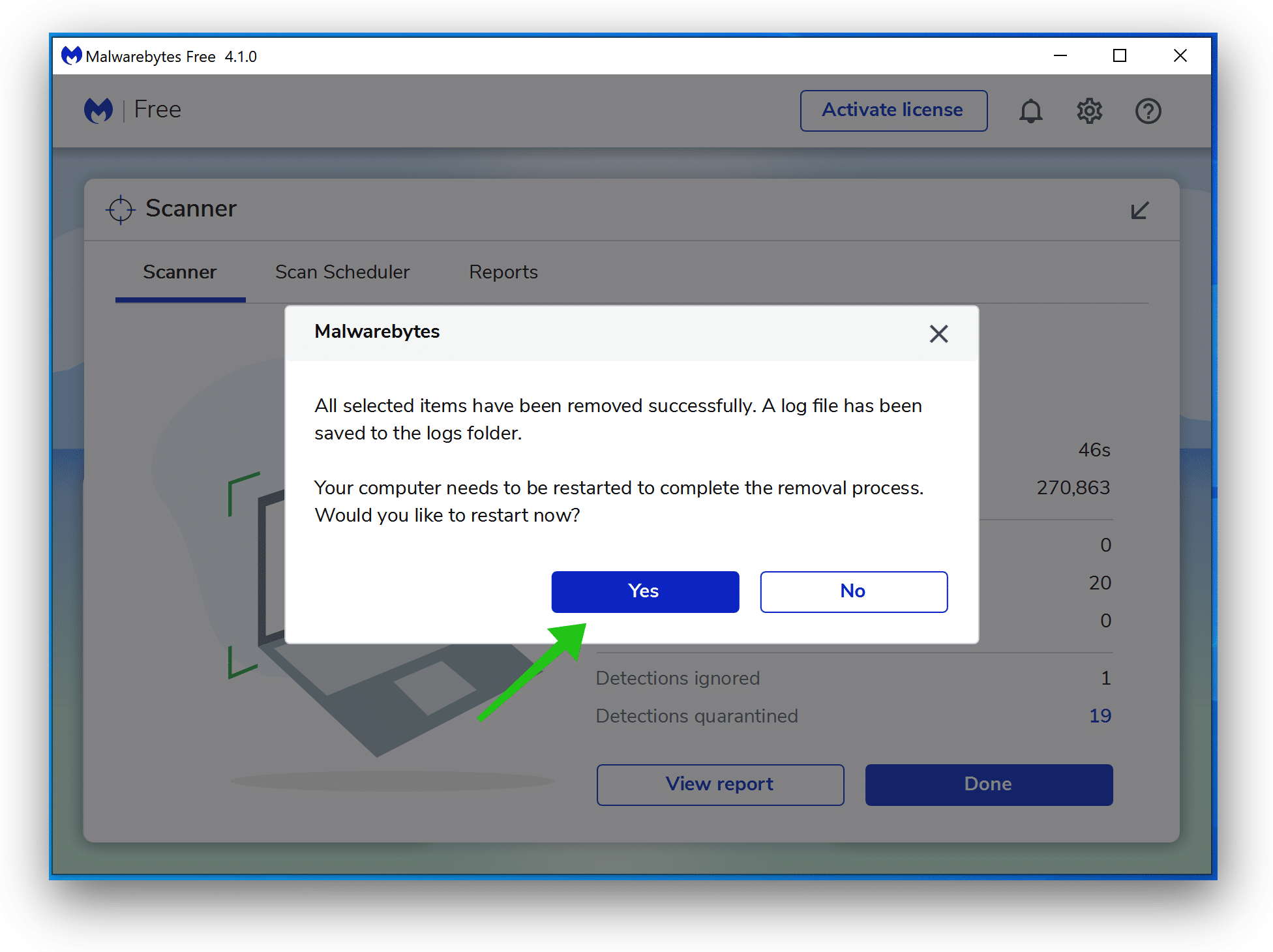
Continue to the next step.
In this second malware removal step, we will start a second scan to ensure no malware remnants are left on your computer. HitmanPRO is a cloud scanner that scans every active file for malicious activity on your computer and sends it to the Sophos cloud for detection. In the Sophos cloud, both Bitdefender antivirus and Kaspersky antivirus scan the file for malicious activities.
When you have downloaded, HitmanPRO, install the HitmanPro 32-bit or HitmanPRO x64. Downloads are saved to the Downloads folder on your computer.
Open HitmanPRO to start the installation and scan.
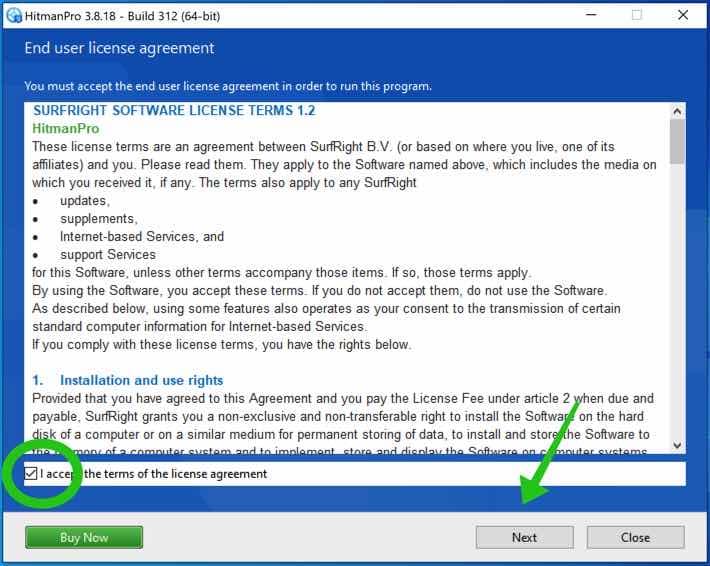
Accept the Sophos HitmanPRO license agreement to continue. Read the license agreement, check the box, and click on Next.
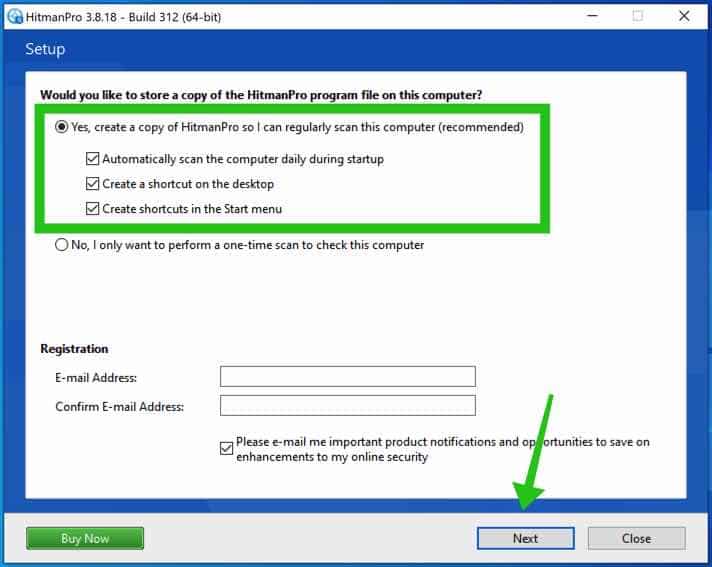
Click the Next button to continue Sophos HitmanPRO installation. Make sure to create a copy of HitmanPRO for regular scans.
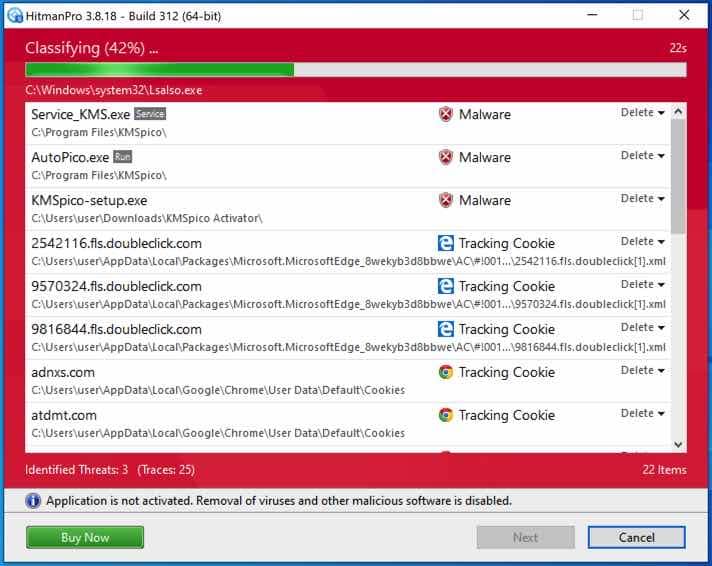
HitmanPRO begins with a scan. Wait for the antivirus scan results.
After the scan, click Next and activate the free HitmanPRO license. Click on Activate Free license.
Enter your e-mail for a Sophos HitmanPRO free thirty days license. Click on Activate.
The free HitmanPRO license is successfully activated.
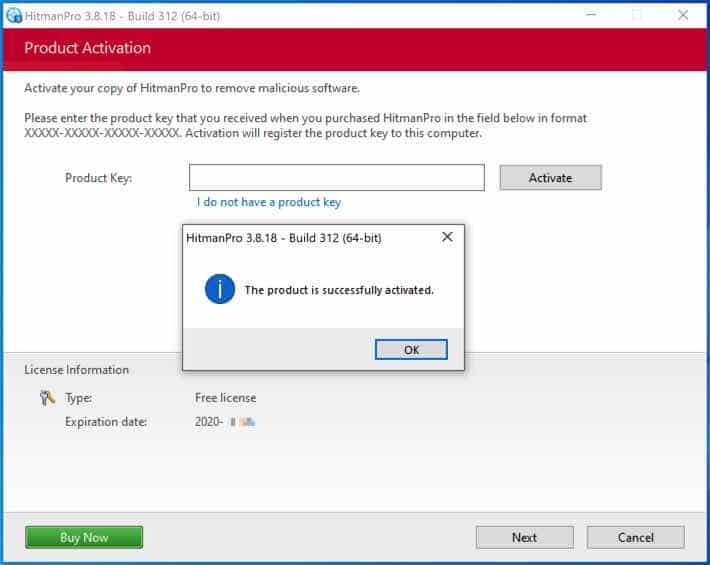
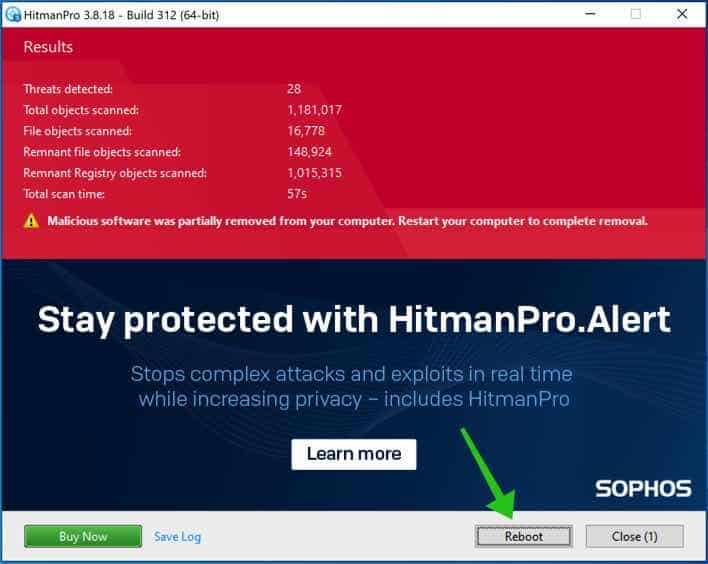
You’ll be presented with the malware removal results. Click Next to continue.
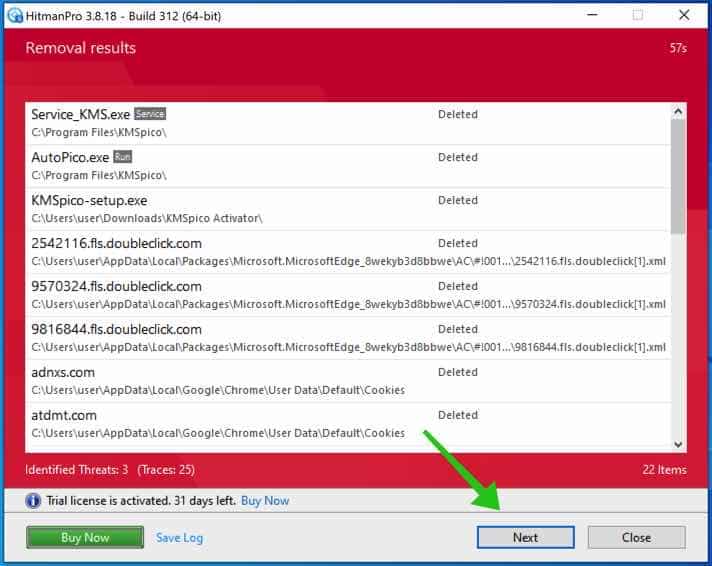
Malicious software was partially removed from your computer. Restart your computer to complete the removal.
Stay safe!