How to remove Linux/Rootkit_Agent.AE!tr? Linux/Rootkit_Agent.AE!tr is a virus file that infects computers. Linux/Rootkit_Agent.AE!tr takes over the computer, collects personal data, or tries to manipulate your computer so that computer hackers can access it.
If your antivirus displays a notification of Linux/Rootkit_Agent.AE!tr, there are files left over. These Linux/Rootkit_Agent.AE!tr related files should be deleted. Unfortunately, Antivirus often only partially succeeds in removing the remains of Linux/Rootkit_Agent.AE!tr.
The Linux/Rootkit_Agent.AE!tr virus is malicious code designed to infect a computer or network system, often damaging, disrupting, or stealing data. It can spread from computer to computer and can even affect entire networks. Computer viruses can be spread through downloads, removable storage media such as USB drives, and even email attachments. This malicious content has become increasingly sophisticated over the years, making it increasingly difficult for users to detect and protect their systems from attack. Various computer viruses, each with its characteristics and capabilities, can have disastrous consequences for any device or system infected.
Users need to understand the risks associated with computer viruses and take steps to protect their data from these malicious intruders.
A computer virus is any malicious software designed to infect computers, damage data, or disrupt operations. Computer viruses can spread through networks and removable media (such as USB drives). They can also be sent as email attachments. Some viruses can even self-replicate and infect other computers without human interaction. There are many types of computer viruses and other malicious software, such as worms, Trojans, and other forms of malware. They’re often designed to damage or disrupt computer systems and networks, steal information, or corrupt data. Viruses and other malware can be spread through infected files and websites, email attachments, and other forms of executable code.
Computer viruses can spread in a few different ways, depending on the type of virus and the security settings of the device they infect. Much malicious software spreads through email, websites, or other files. Email attachments are a common way for computer viruses to spread. They can be sent as an email attachment or embedded in the email message itself. If an email attachment is infected, it can infect the device it’s opened and any other devices that the infected attachment is copied to. Computer viruses can also spread through websites that host malicious software, such as social media sites that distribute fake videos, images, and other content. Websites can also host malicious code, which can infect a device if a user clicks on a link or visits the site.
The symptoms of an infection depend heavily on the type of virus that has infected a device. General symptoms of an infection include the following:
- A computer that is running more slowly than normal
- A large amount of data being sent or received
- A computer that is excessively using its memory or processor
- A large number of pop-up advertisements
- A computer that runs programs automatically when it’s not in use
- A large amount of data being deleted from a computer
These symptoms may indicate that a computer is infected with the Linux/Rootkit_Agent.AE!tr virus. Users may want to scan the device for viruses if a computer is experiencing any of these symptoms. A computer virus scanner can help identify viruses and other malicious software on a device. It’s important to note that these scanners aren’t always completely accurate, so users should take a few steps to confirm the results. Users may want to take steps to clean the device if a computer is infected with a computer virus.
Computer viruses can have a wide range of effects on a computer and the user’s data. They can disrupt operations, damage data, or render a computer unusable. Some computer viruses can also spread to other computers and networks, infecting many devices simultaneously. These kinds of viruses can be extremely damaging and difficult to remove. In some cases, purchasing new devices or restoring data from a backup may be necessary to remove the Linux/Rootkit_Agent.AE!tr virus fully. The risks of computer viruses are numerous, and users need to take steps to protect their devices from infection.
Detecting the Linux/Rootkit_Agent.AE!tr computer virus is often a difficult process. Users should regularly check their devices for viruses, as it may be difficult to detect an infection while it’s occurring. Users can check their devices with antivirus software to see if they have any viruses. Follow the instructions below.
How to remove Linux/Rootkit_Agent.AE!tr
Malwarebytes anti-malware is an essential tool in the fight against malware. Malwarebytes can remove many types of Linux/Rootkit_Agent.AE!tr malware that other software does often miss. Malwarebytes is costing you absolutely nothing. When cleaning up an infected computer, Malwarebytes has always been free, and I recommend it as an essential tool in the battle against malware.
Install Malwarebytes, and follow the on-screen instructions.
Click Scan to start a malware scan.
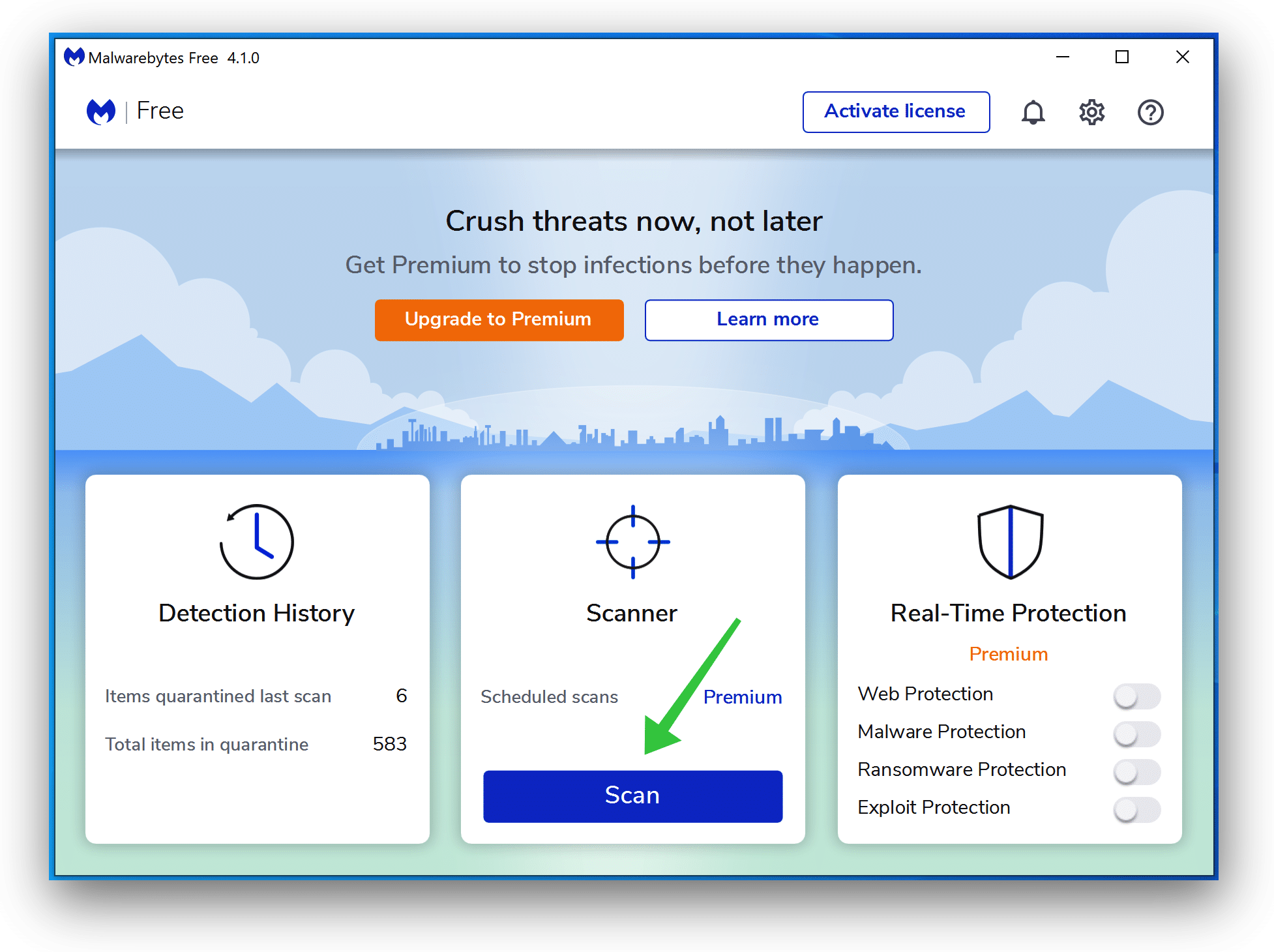
Wait for the Malwarebytes scan to finish. Once completed, review the Linux/Rootkit_Agent.AE!tr adware detections.
Click Quarantine to continue.
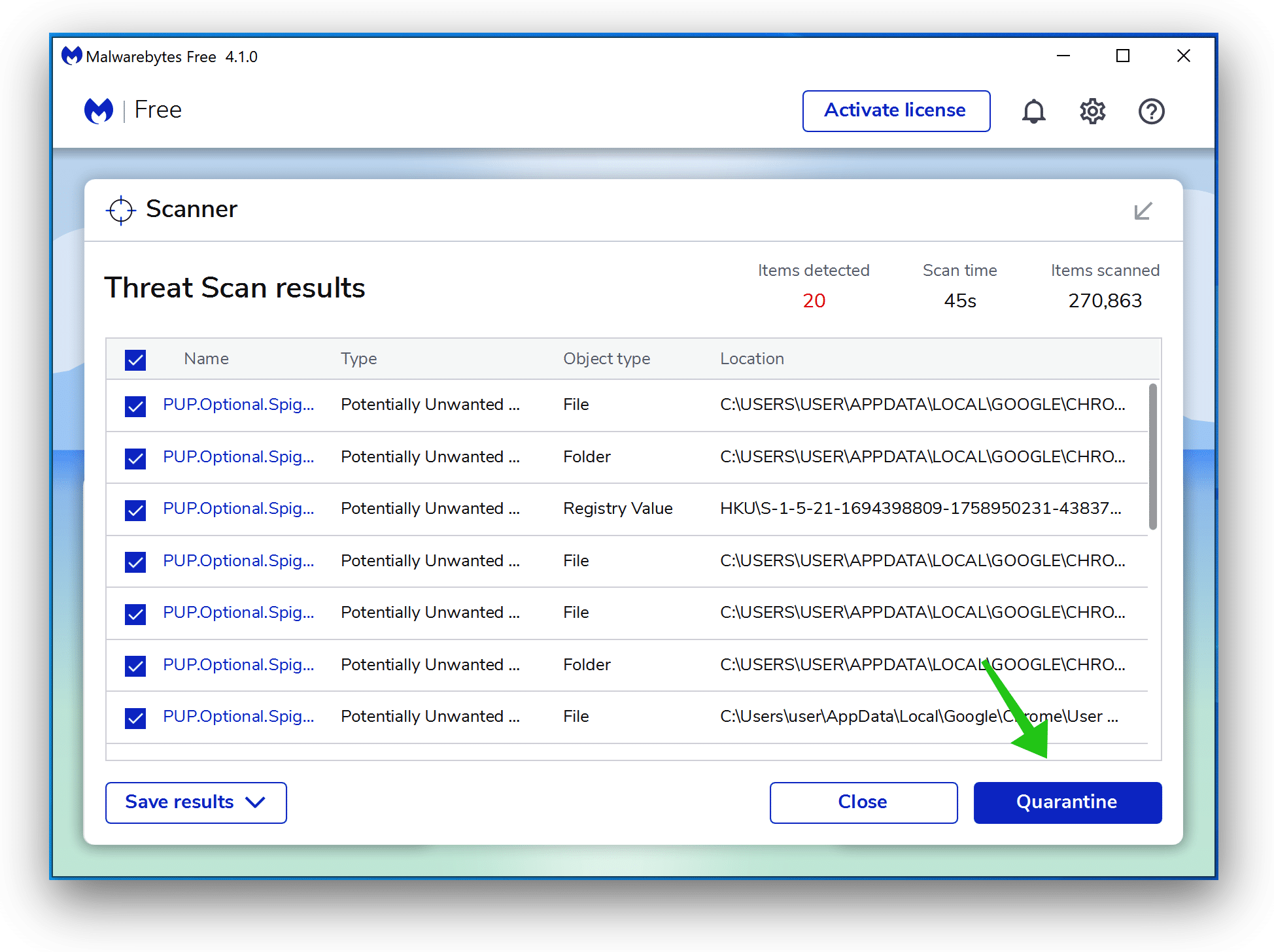
Reboot Windows after all the adware detections are moved to quarantine.
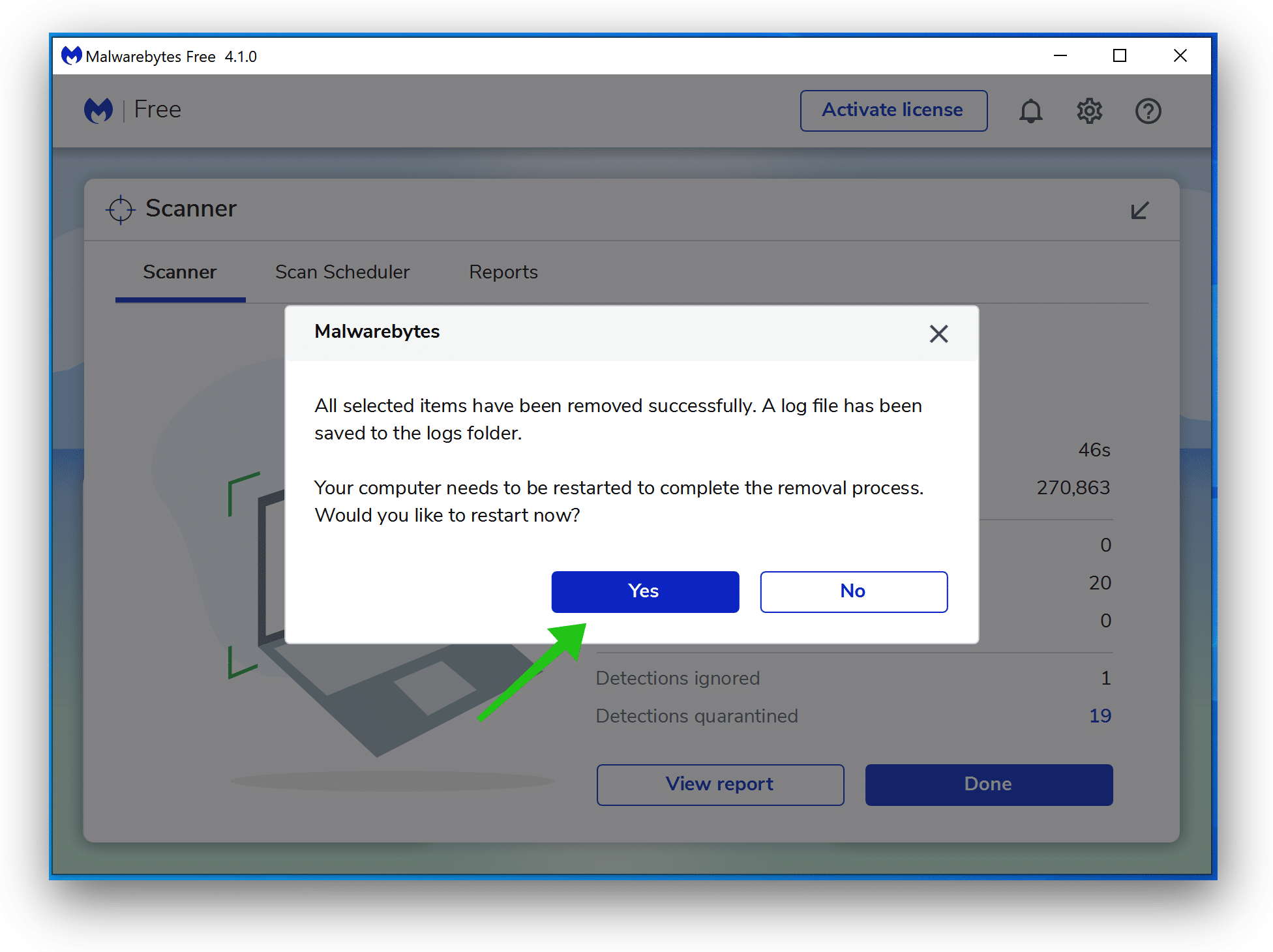
Continue to the next step.
Remove unwanted programs with Sophos HitmanPRO
In this second malware removal step, we will start a second scan to ensure no malware remnants are left on your computer. HitmanPRO is a cloud scanner that scans every active file for malicious activity on your computer and sends it to the Sophos cloud for detection. In the Sophos cloud, both Bitdefender antivirus and Kaspersky antivirus scan the file for malicious activities.
When you have downloaded HitmanPRO install the HitmanPro 32-bit or HitmanPRO x64. Downloads are saved to the Downloads folder on your computer.
Open HitmanPRO to start installation and scan.
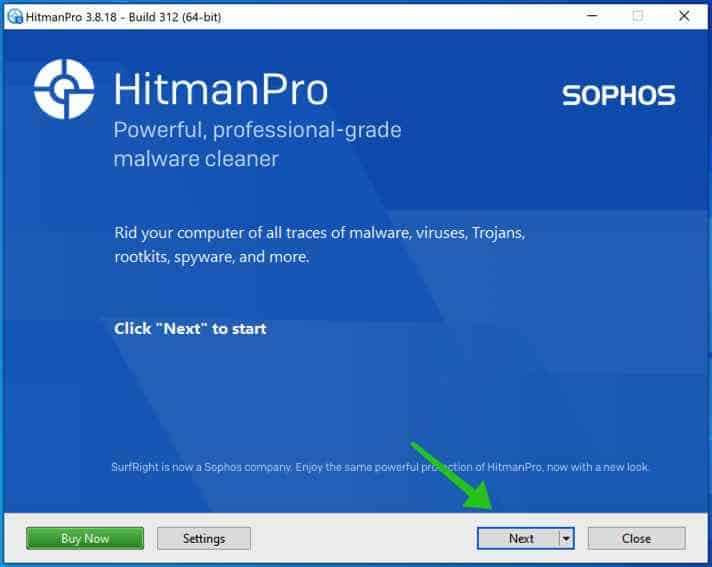
Accept the Sophos HitmanPRO license agreement to continue. Read the license agreement, check the box, and click on Next.
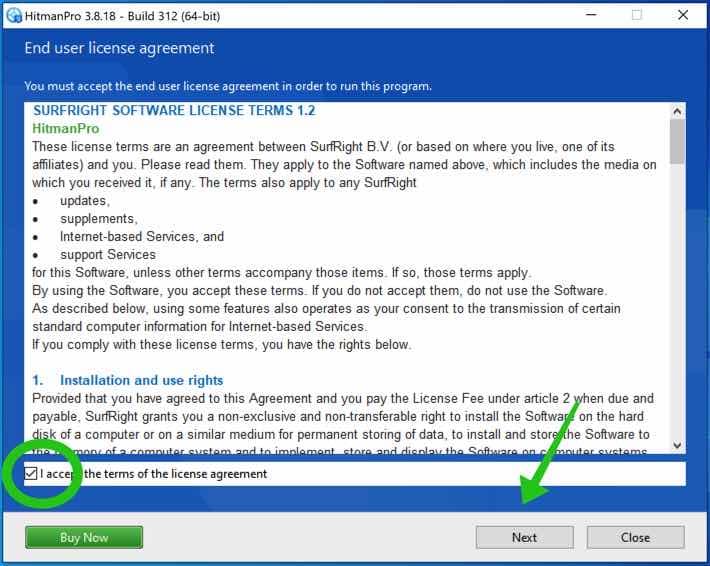
Click the Next button to continue Sophos HitmanPRO installation. Make sure to create a copy of HitmanPRO for regular scans.
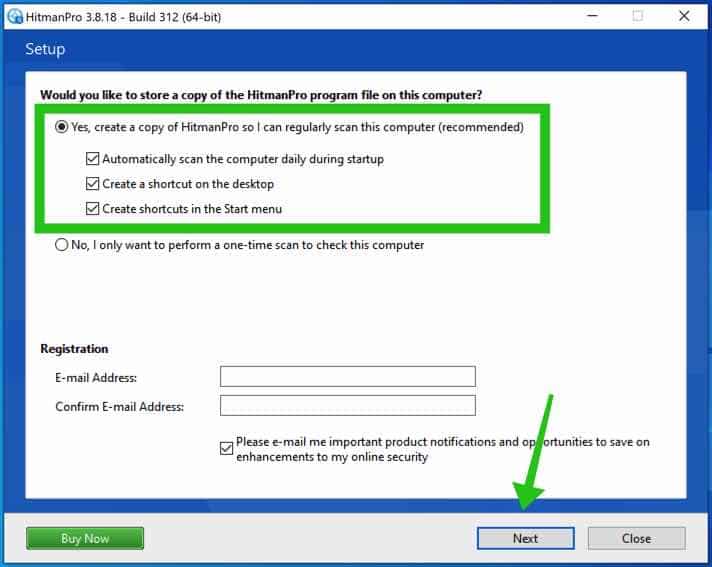
HitmanPRO begins with a scan, wait for the antivirus scan results.
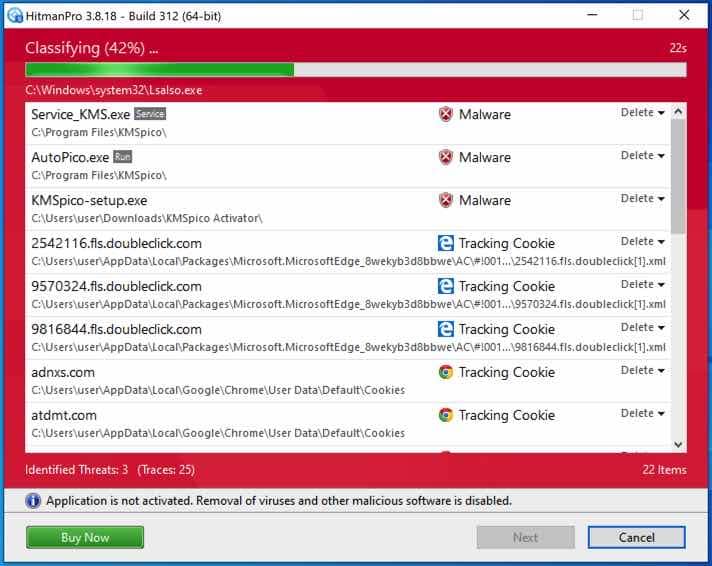
When the scan is done, click Next and activate the free HitmanPRO license. Click on Activate Free license.
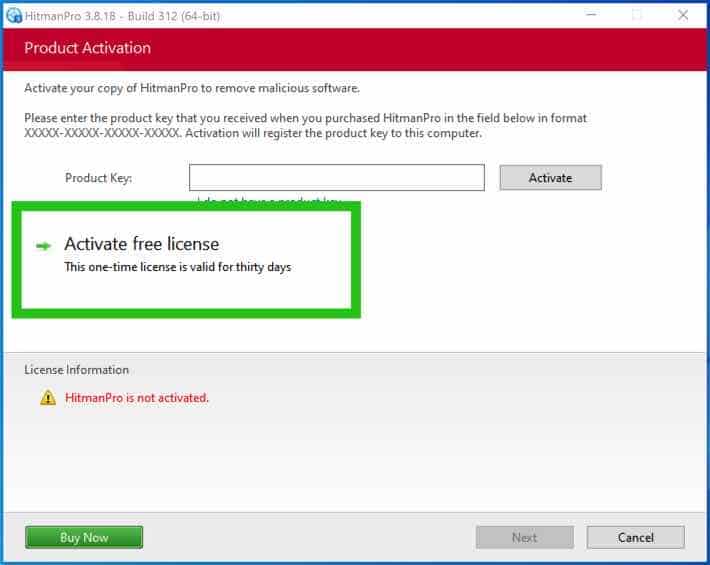
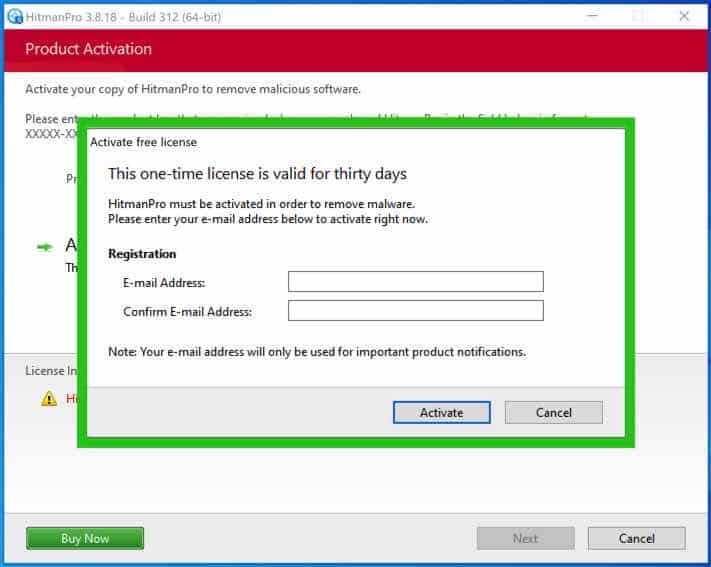
Enter your e-mail for a Sophos HitmanPRO free thirty days license. Click on Activate.
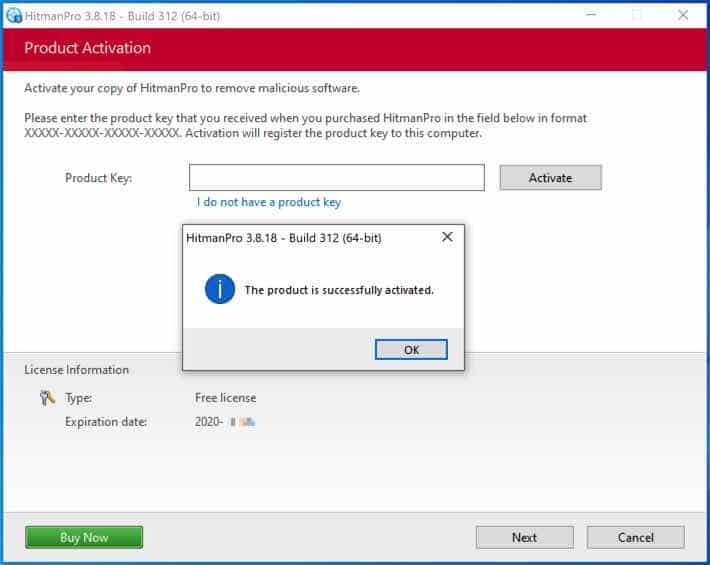
The free HitmanPRO license is successfully activated.
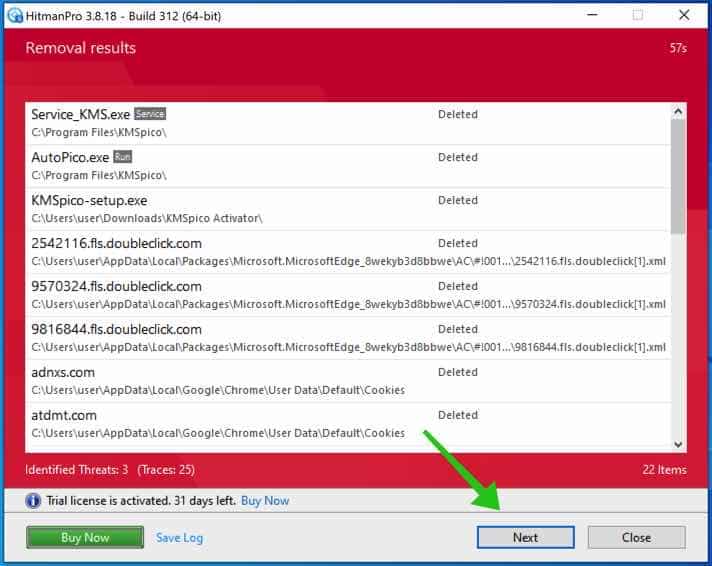
You’ll be presented with the malware removal results. Click Next to continue.
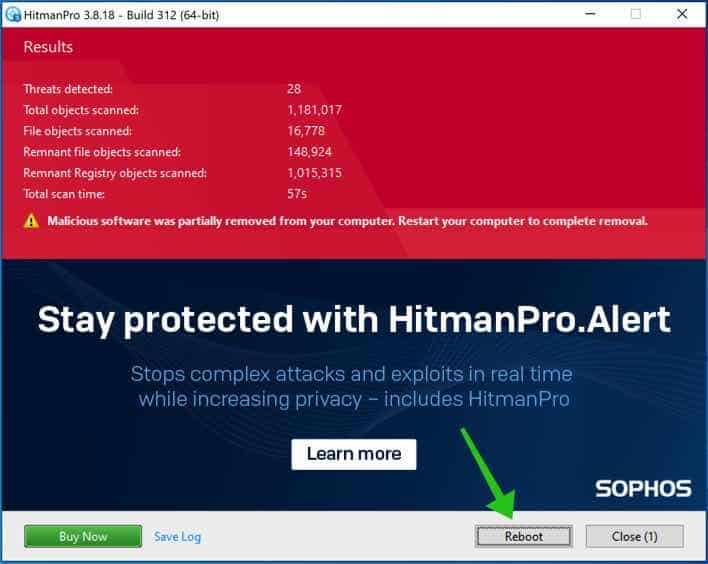
Malicious software was partially removed from your computer. Restart your computer to complete the removal.
Bookmark this page when you reboot your computer.
How to prevent Linux/Rootkit_Agent.AE!tr virus?
The best way to prevent the Linux/Rootkit_Agent.AE!tr virus is to install antivirus software on every device, such as Malwarebytes. It’s also important to keep all devices connected to a network up-to-date with the latest software patches and security updates. Users should also avoid clicking on links within emails from unknown senders, downloading files from unknown websites, or visiting websites that are known to distribute viruses or malicious software.
Users should also avoid opening email attachments unless they are expecting them. If a link or email attachment is expected, users should scan it with antivirus software before opening it. Users should also be careful about what devices they plug into their network and what removable media they use to transfer data between devices. It’s important to note that no device is 100% immune to viruses. Even devices with antivirus software installed can become infected with a computer virus.
Users can follow a few best practices to protect themselves against computer viruses. These include the following:
- Keep all devices up-to-date with the latest software updates.
- Use antivirus software on all devices.
- Scan all links, files, and email attachments before opening them.
- Avoid clicking on links from unknown senders.
- Avoid downloading files from unknown websites.
- Avoid visiting websites that are known to distribute viruses or malicious software.
- Be careful about what devices you plug into your network.
- Be careful about what removable media you use to transfer data between devices.
- Regularly check your devices for viruses.
I hope this helped. Thank you for reading!