CONTACT ransomware is designed to encrypt your personal files and personal documents. CONTACT ransomware requests bitcoin cryptocurrency to recover the encrypted files. The ransom charge varies from different versions of the CONTACT ransomware.
CONTACT ransomware encrypts files on your computer and adds a string of unique characters to the extension of the encrypted files. For example, image.jpg becomes image.jpg.CONTACT
The decrypt text-file with instructions is placed on the Windows desktop: DECRYPT-FILES.txt
In most cases, it is not possible to recover the files encrypted by CONTACT ransomware without the intervention of the Ransomware developers.
The only way to recover files infected by CONTACT ransomware is to pay the ransomware developers. Sometimes it is possible to recover your files but this is only possible when the ransomware developers made a flaw in their encryption software, which unfortunately doesn’t occur frequently.
I do not recommend paying for the CONTACT ransomware, instead, make sure you have a valid FULL back-up of Windows and restore it immediately.
Read more about how to restore Windows (microsoft.com) and how to protect your computer from ransomware (microsoft.com).
Having said that there are no tools at this moment to restore your encrypted personal files or documents that are encrypted by the CONTACT ransomware. Although you might want to try to restore encrypted files. In more sophisticated ransomware the decryption key used to recover your files is server-side meaning the decryption key is only available from the ransomware developers. In order to remove the file that downloaded the ransomware files to your computer, you can remove the CONTACT ransomware file with Malwarebytes. Malwarebytes instructions to remove CONTACT ransomware files can be found in this instruction.
Try to decrypt files using online tools
Warning: any attempt to decrypt your CONTACT ransomware encrypted files may cause permanent damage to your encrypted files.
You can try to restore your encrypted files using the ID Ransomware decrypt tools. In order, to proceed you need to upload one of the encrypted files and identify the ransomware that infected your computer and encrypted your files.
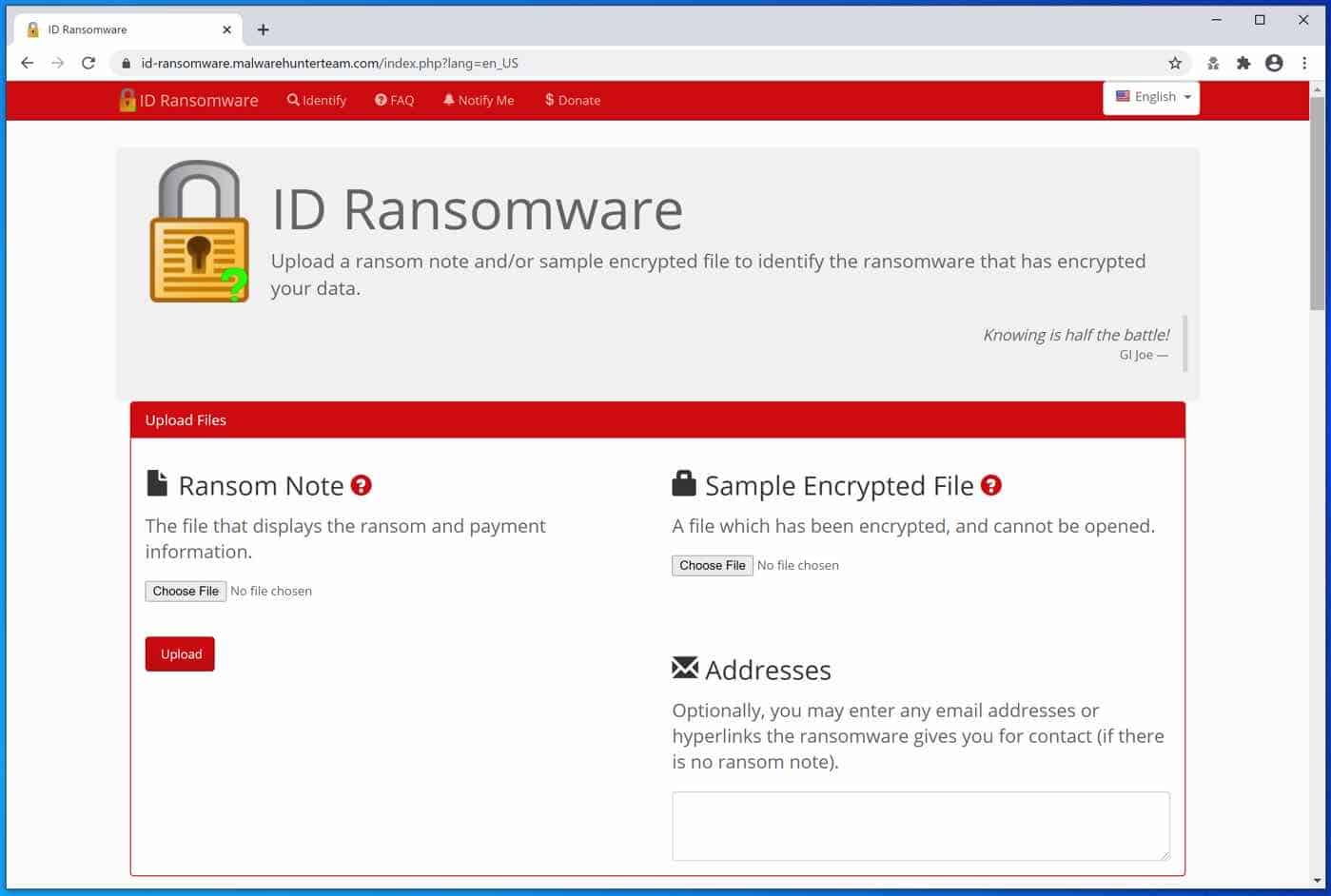
If a CONTACT ransomware decryption tool is available on the NoMoreRansom site, the decryption information will show you how to proceed. Unfortunately, this almost never works out. Worth the try.
You can also use the Emsisoft ransomware decryption tools.
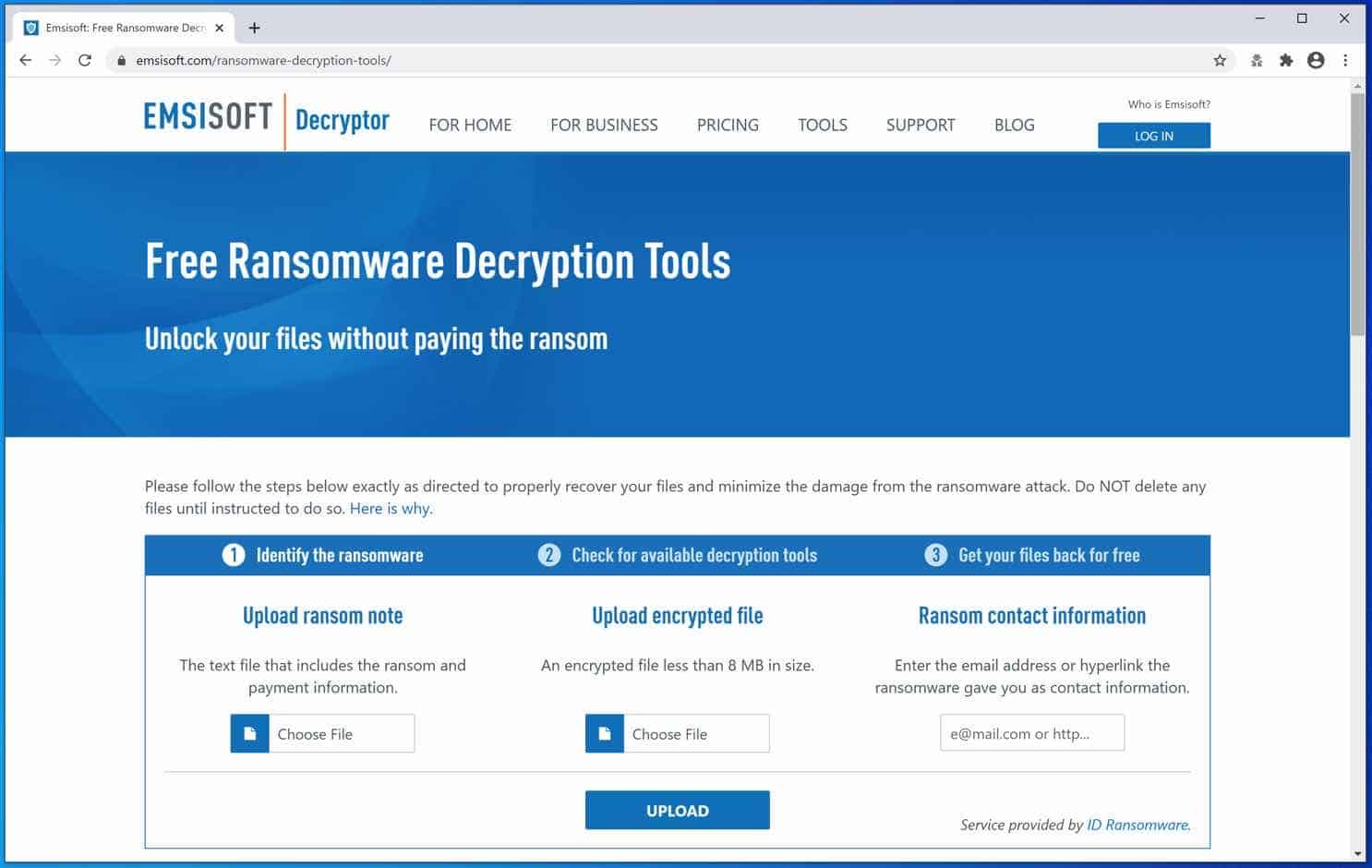
Remove CONTACT Ransomware with Malwarebytes
Note: Malwarebytes will not restore or recover your encrypted files, it does, however, remove the CONTACT virus file that infected your computer with the CONTACT ransomware and downloaded the ransomware file to your computer, this is known as the payload file.
It is important to remove the ransomware file if you are not reinstalling Windows, by doing so you will prevent your computer from another ransomware infection.
Install Malwarebytes, follow on-screen instructions.
Click Scan to start a malware-scan.
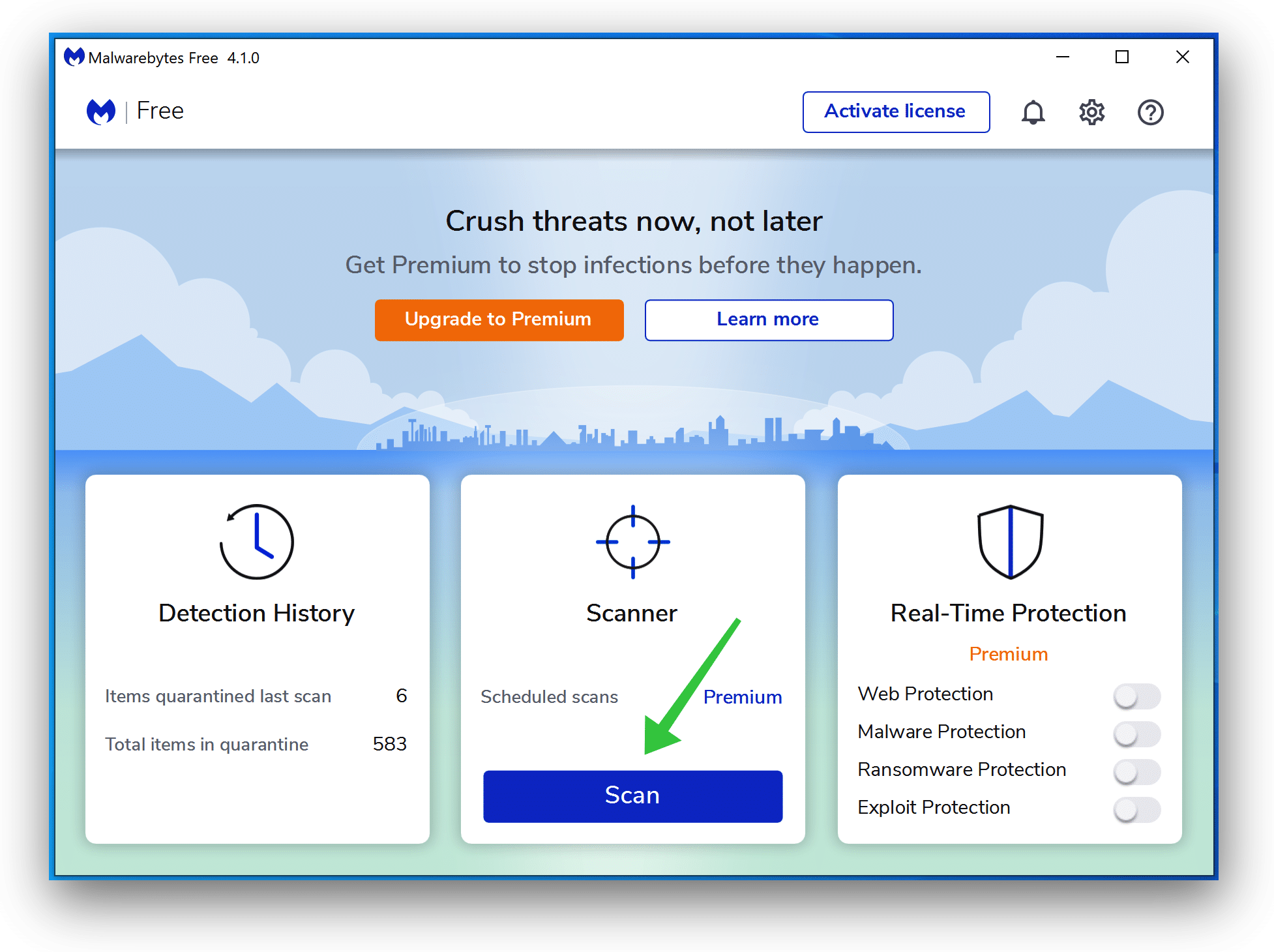
Wait for the Malwarebytes scan to finish.
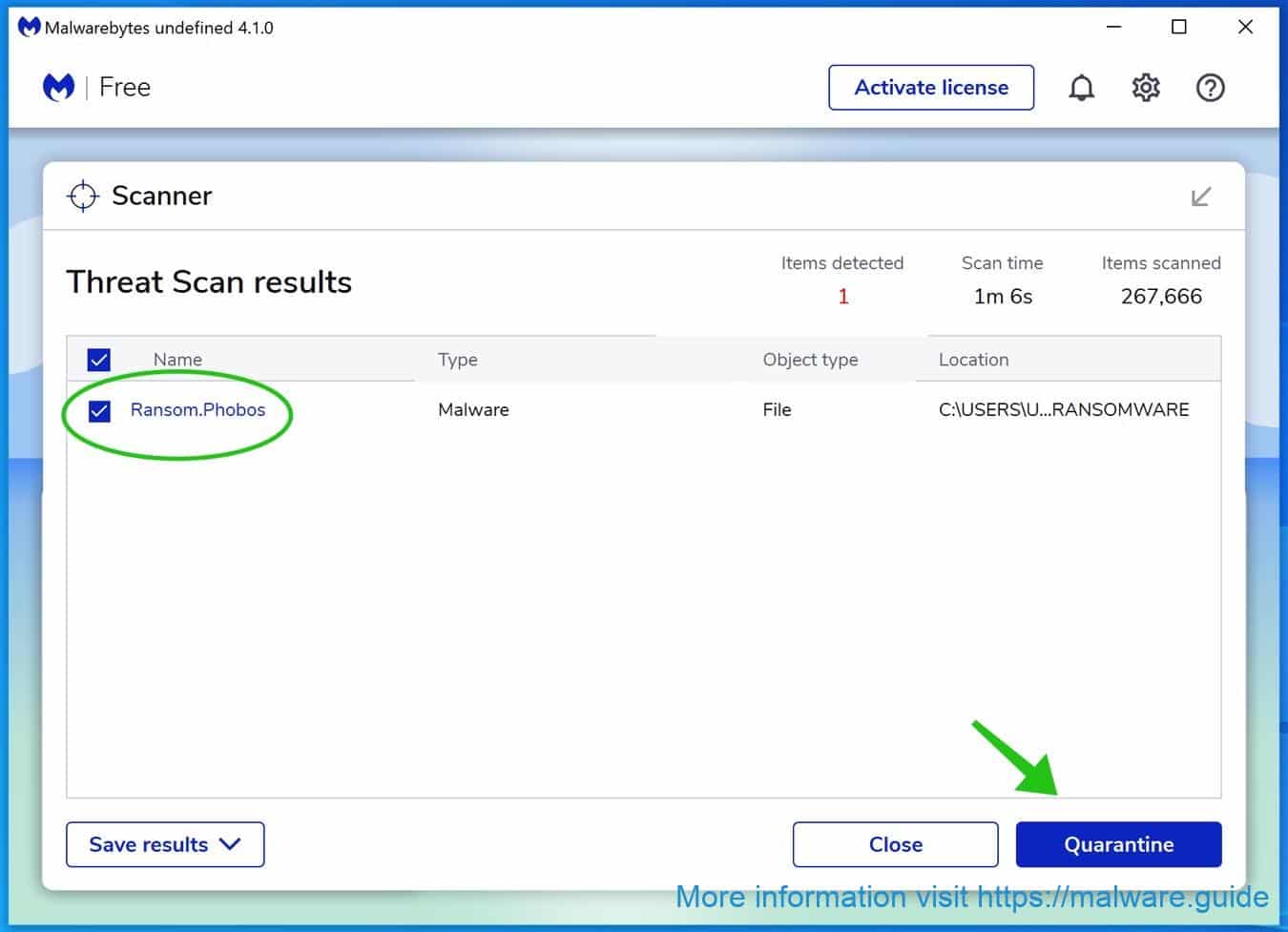
Once completed, review the CONTACT ransomware detections.
Click Quarantine to continue.
Reboot Windows after all the detections are moved to quarantine.
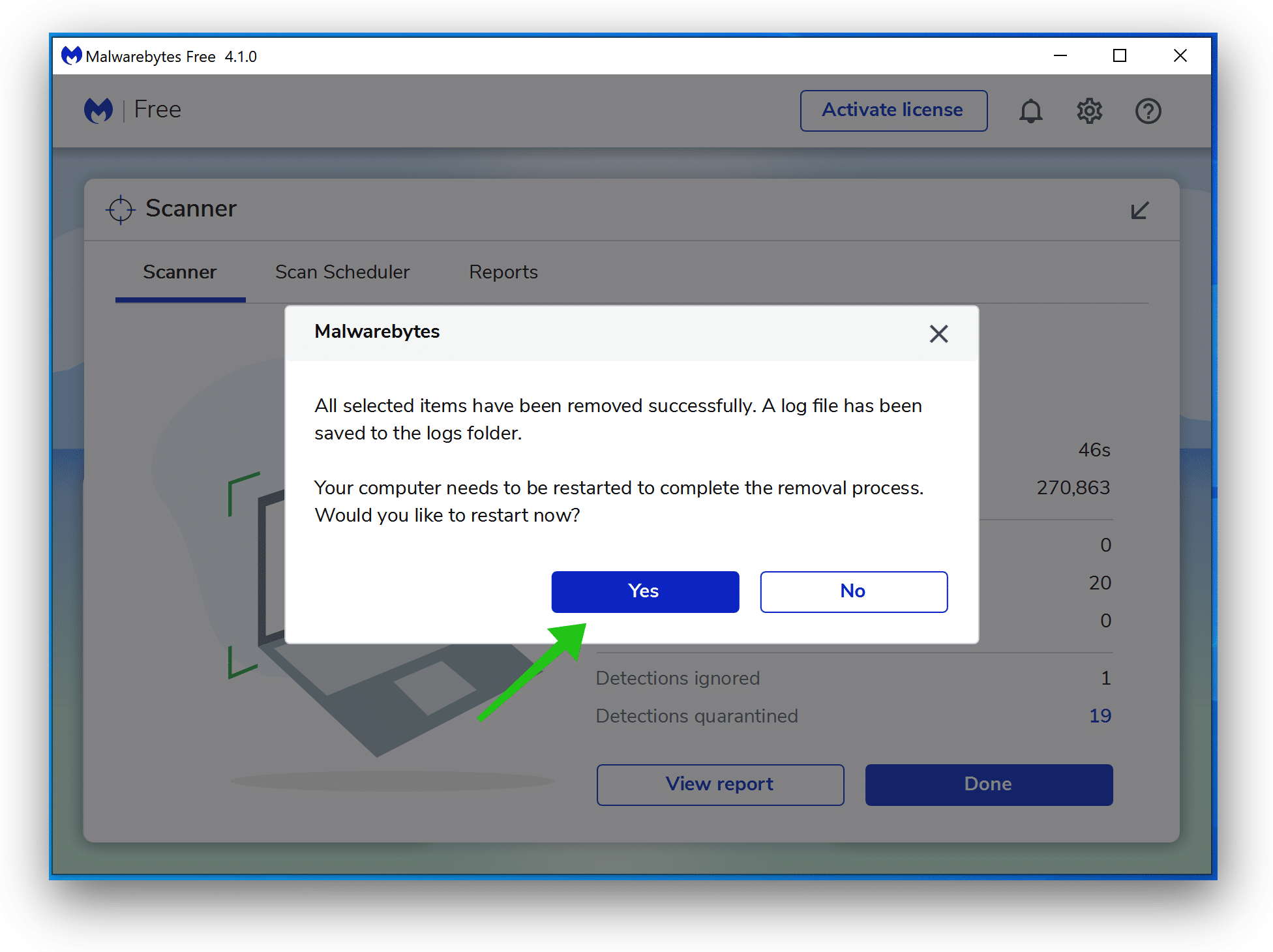
You have now successfully removed CONTACT Ransomware file from your device.
 Remove malware with Sophos HitmanPRO
Remove malware with Sophos HitmanPRO
In this second malware removal step, we will start a second scan to make sure there are no malware remnants left on your computer. HitmanPRO is a cloud scanner that scans every active file for malicious activity on your computer and sends it to the Sophos cloud for detection. In the Sophos cloud both Bitdefender antivirus and Kaspersky antivirus scan the file for malicious activities.
When you have downloaded HitmanPRO install the HitmanPro 32-bit or HitmanPRO x64. Downloads are saved to the Downloads folder on your computer.
Open HitmanPRO to start installation and scan.
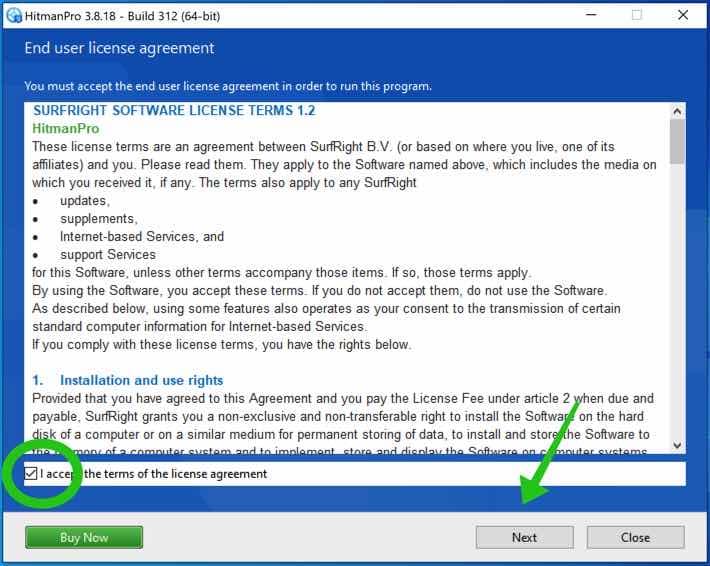
Accept the Sophos HitmanPRO license agreement to continue. Read the license agreement, check the box and click on Next.
Click the Next button to continue Sophos HitmanPRO installation. Make sure to create a copy of HitmanPRO for regular scans.
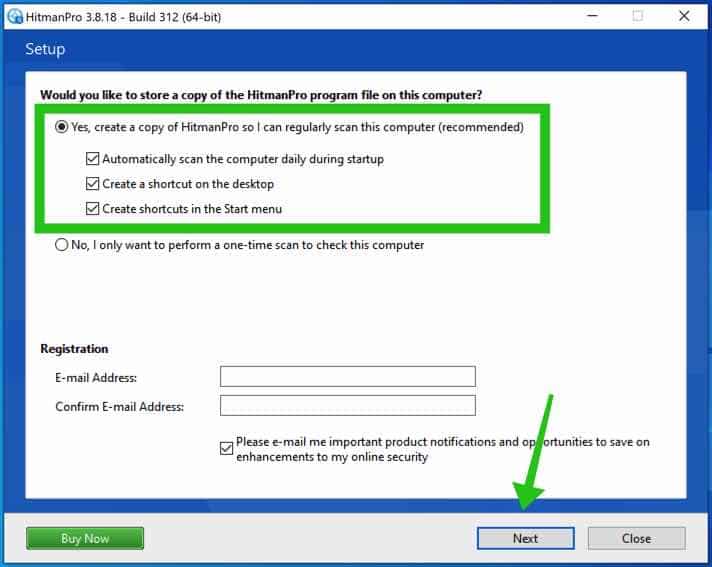
HitmanPRO begins with a scan, wait for the antivirus scan results.
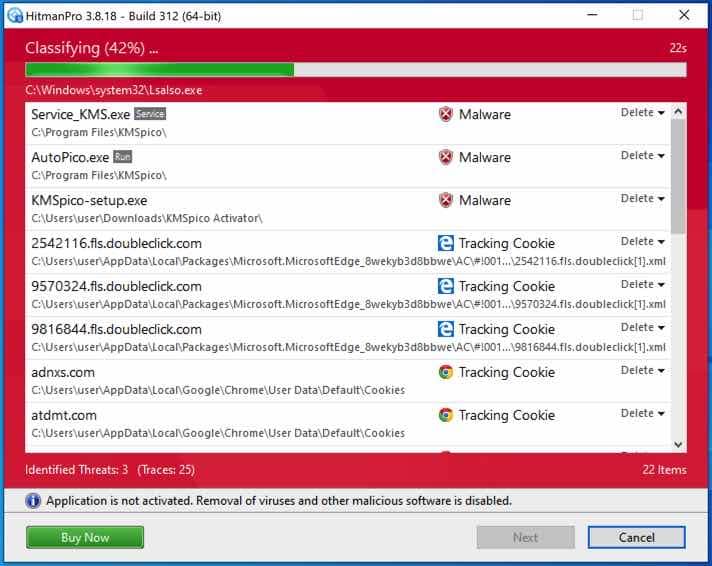
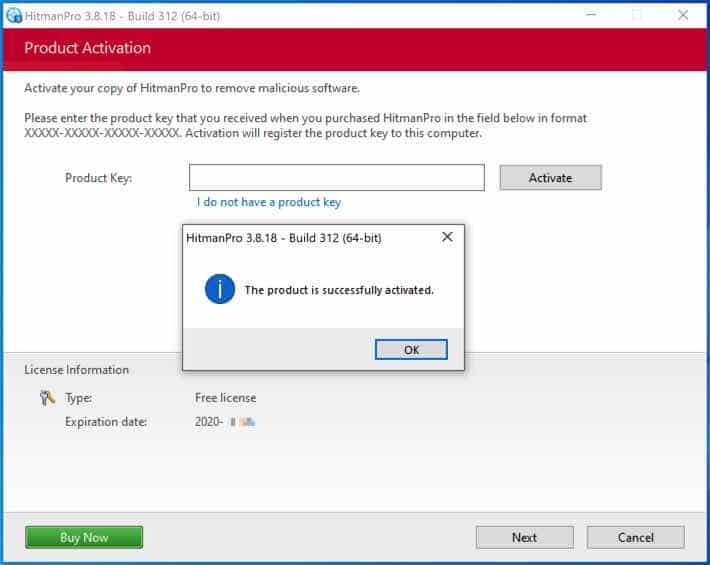
When the scan is done, click Next and activate the free HitmanPRO license. Click on Activate Free license.
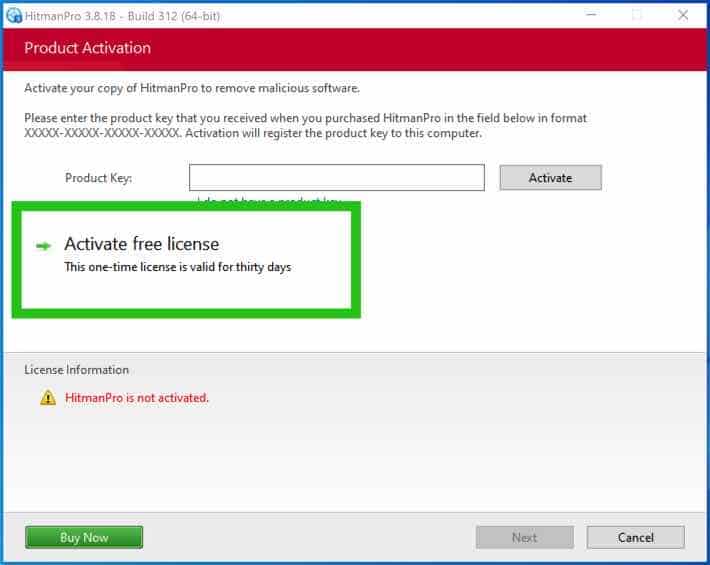
Enter your e-mail for a Sophos HitmanPRO free thirty days license. Click on Activate.
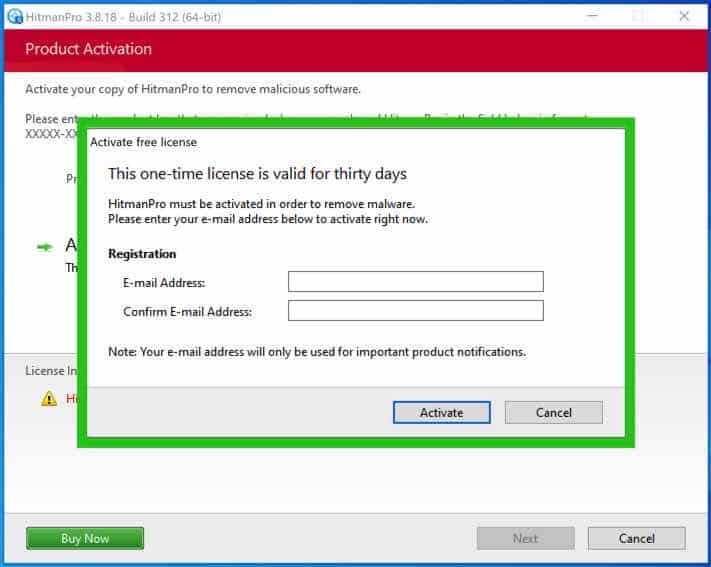
The free HitmanPRO license is successfully activated.
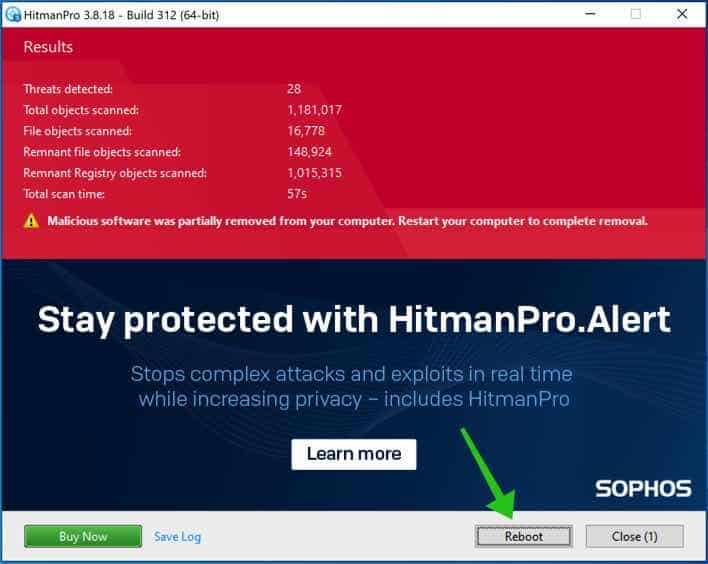
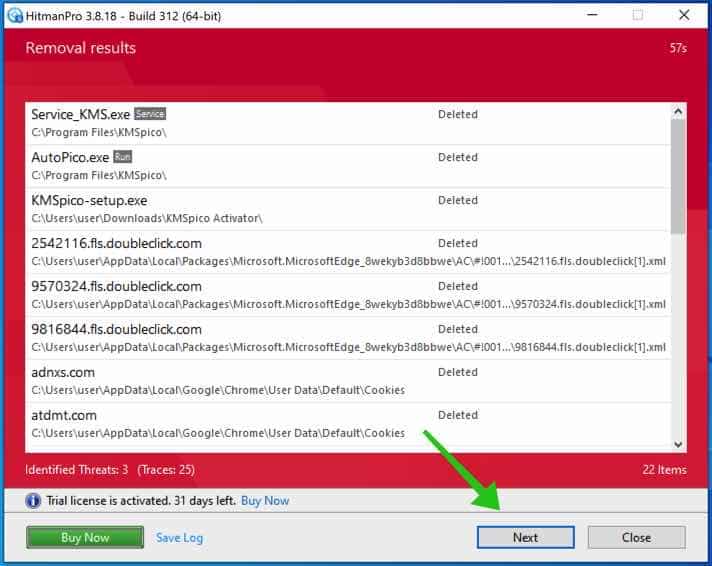
You’ll be presented with the CONTACT ransomware removal results, click Next to continue.
Malicious software was partially removed from your computer. Restart your computer to complete removal.