Your MetaMask wallet has not yet been verified is a fake e-mail, sent out to deceive you into thinking the hacker knows your password. In the content of the e-mail your password is included, which is odd as to why and how would a hacker know your password? Well, this is most likely due to a recent hack or data breach on a website where hackers collected many passwords.
What they do, these hackers sent out fake e-mails with a false message and include one of the passwords they hacked in the e-mail, making it look legit and real to the victim. You can find out if your e-mail is compromised during a hack at haveibeenpwned.com.
After the victim has received the fake e-mail the e-mail contains a bitcoin address to pay ransom for a fake crime or fake message such as: Your MetaMask wallet has not yet been verified
 Some information in the mail varies in different examples of the mail and if the attack is successful it may evolve more over time. At the time of writing, the sender’s email address (either in the reply-to field or in one case included, in the text of the mail), the ransom amount, and the bitcoin address all vary.
Some information in the mail varies in different examples of the mail and if the attack is successful it may evolve more over time. At the time of writing, the sender’s email address (either in the reply-to field or in one case included, in the text of the mail), the ransom amount, and the bitcoin address all vary.
No need to panic, all you have to do is to check if the e-mail containing the password matches the password you are using now if so, change it immediately, it not, it is an old password and I only advise you to scan your computer for malware.
- Always use unique passwords, as some websites or services might get hacked soon or later, which can result in hackers gathering passwords and use these passwords on a variety of services to see if they still work.
- Use a password manager to store your passwords securely.
- Never pay the ransom asked for in the e-mail to the hackers.
Scan your computer for malware
I recommend scanning and removing malware from your computer with Malwarebytes. Malwarebytes is a comprehensive adware removal tool and free to use.
Sometimes hackers have access to your computer using malware, this malware must be removed as soon as possible. Malwarebytes is able to detect and remove trojan horses, remote administration tools, botnets from your computer.
- Install Malwarebytes, follow on-screen instructions.
- Click Scan to start a malware-scan.
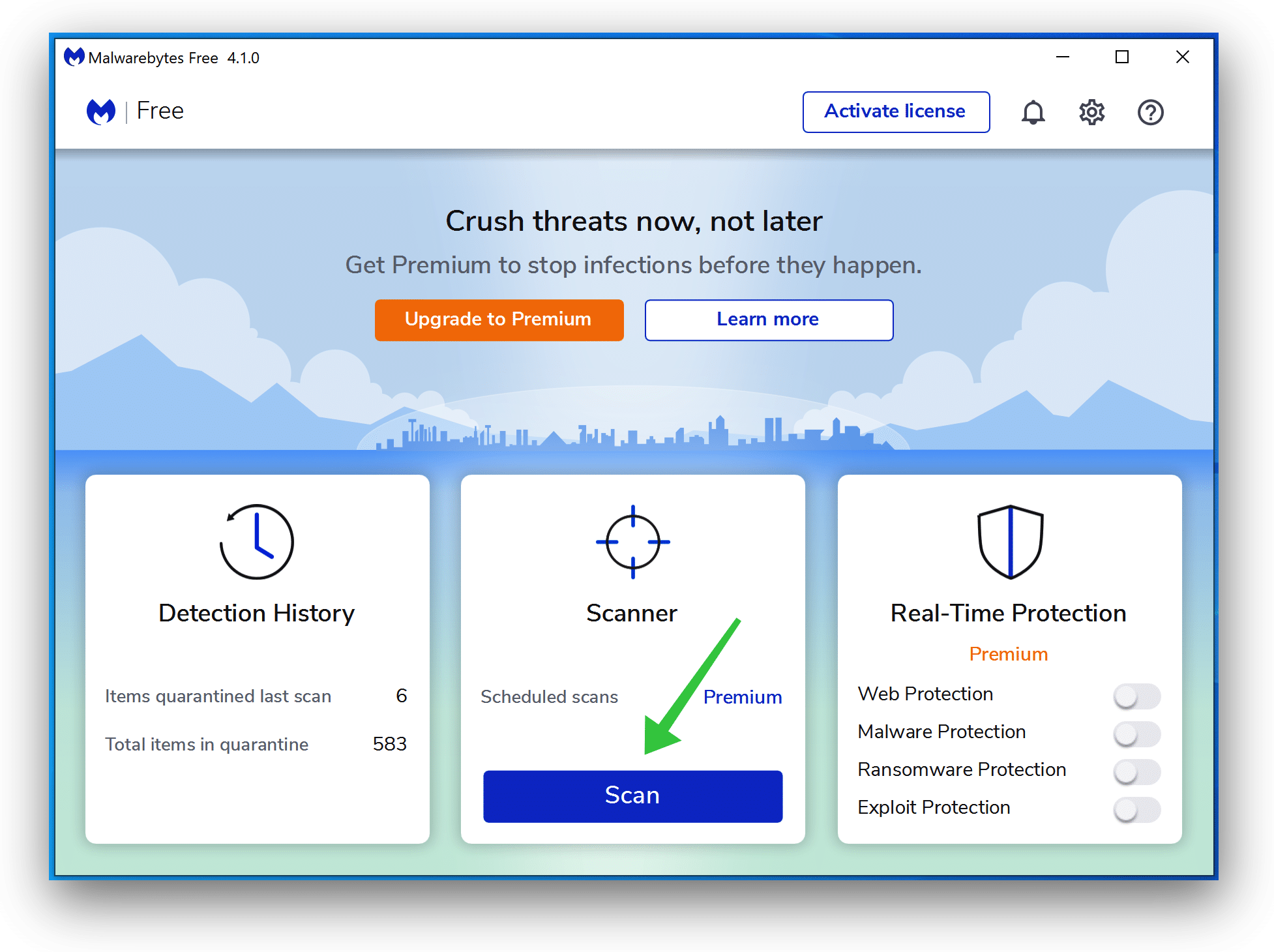
- Wait for the Malwarebytes scan to finish.
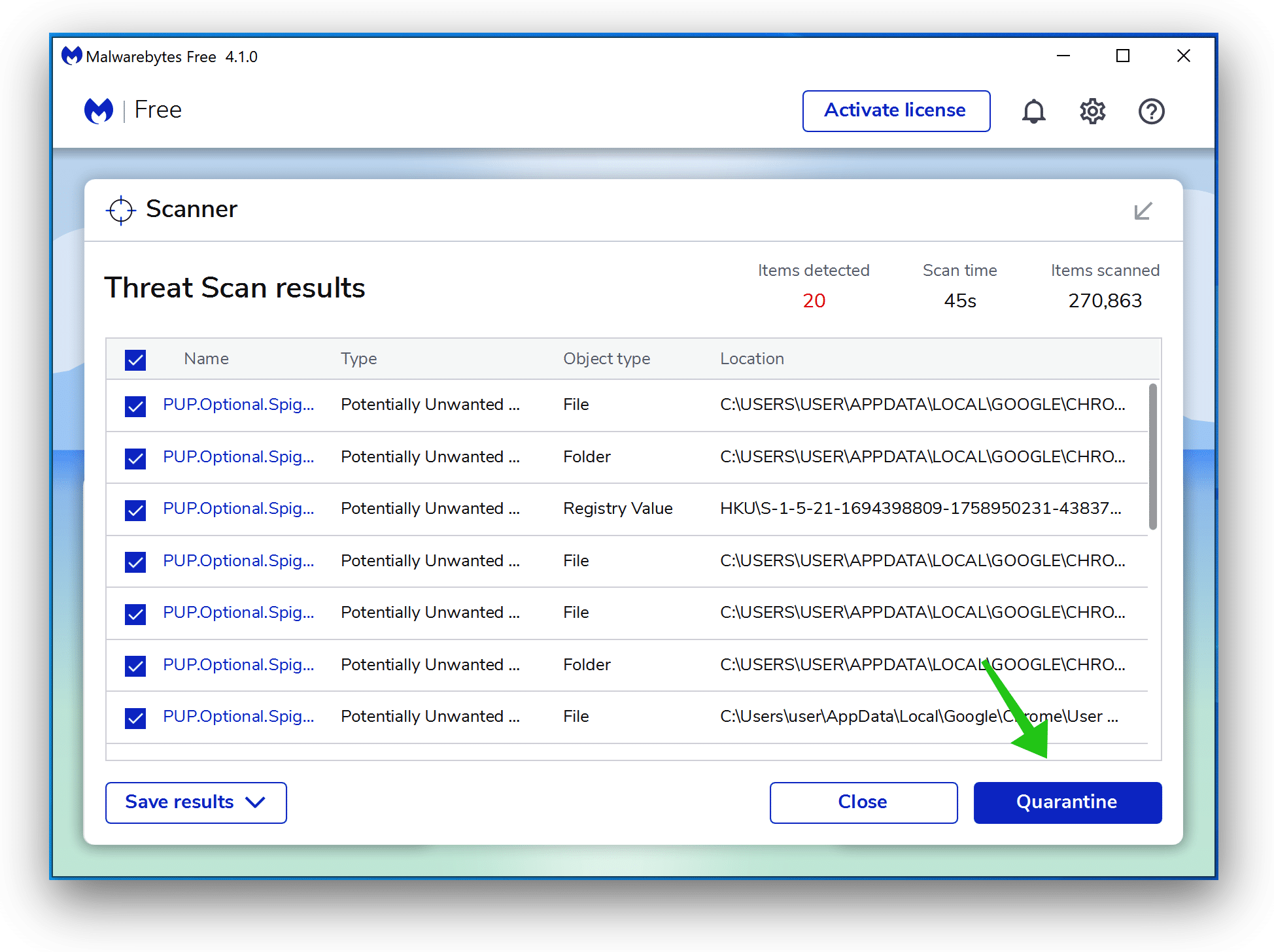
- Once completed, review the virus detections.
- Click Quarantine to continue.
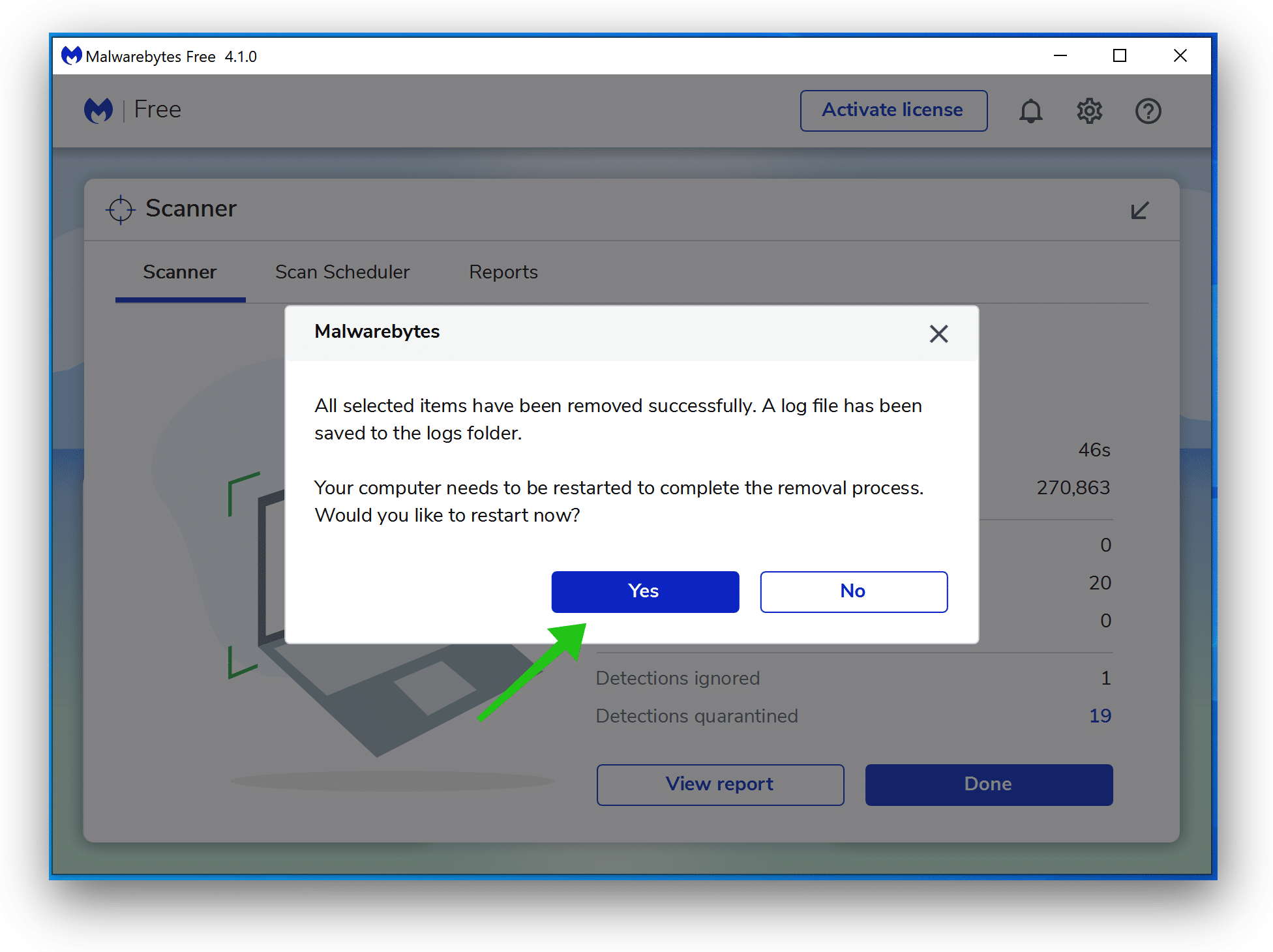
- Reboot Windows after all the detections are moved to quarantine.
 Remove malware with Sophos HitmanPRO
Remove malware with Sophos HitmanPRO
In this second malware removal step, we will start a second scan to make sure there are no malware remnants left on your computer. HitmanPRO is a cloud scanner that scans every active file for malicious activity on your computer and sends it to the Sophos cloud for detection. In the Sophos cloud both Bitdefender antivirus and Kaspersky antivirus scan the file for malicious activities.
When you have downloaded HitmanPRO install the HitmanPro 32-bit or HitmanPRO x64. Downloads are saved to the Downloads folder on your computer.
Open HitmanPRO to start installation and scan.
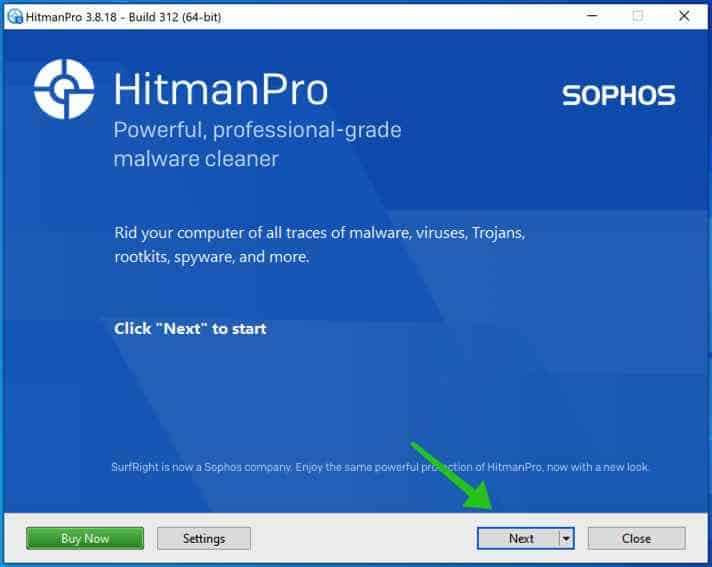
Accept the Sophos HitmanPRO license agreement to continue. Read the license agreement, check the box and click on Next.
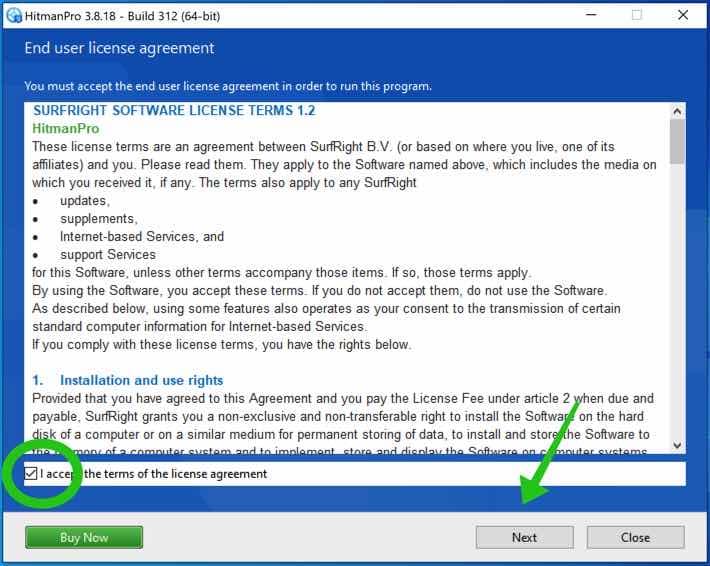
Click the Next button to continue Sophos HitmanPRO installation. Make sure to create a copy of HitmanPRO for regular scans.
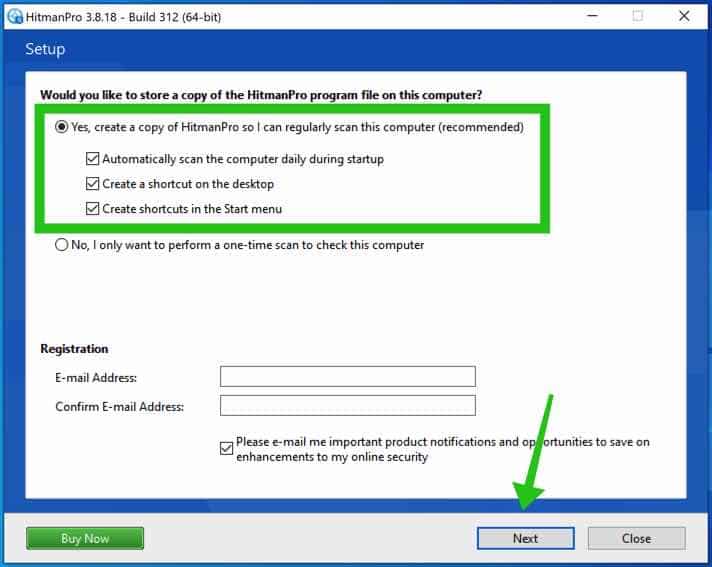
HitmanPRO begins with a scan, wait for the antivirus scan results.
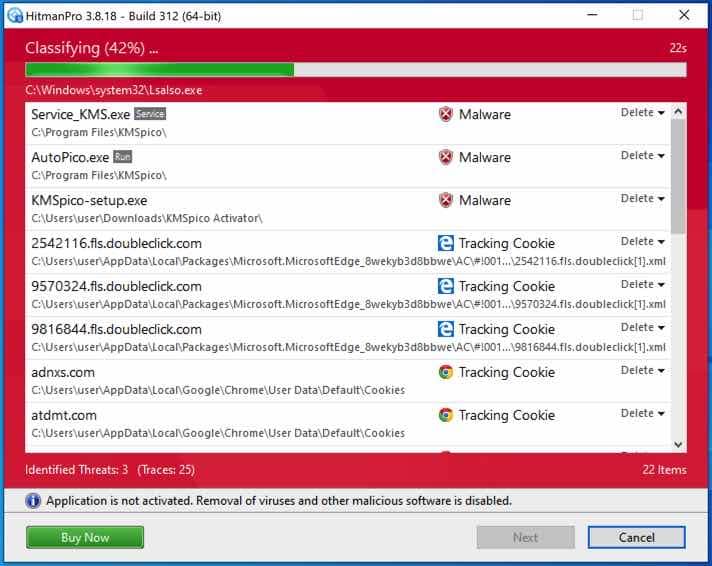
When the scan is done, click Next and activate the free HitmanPRO license. Click on Activate Free license.
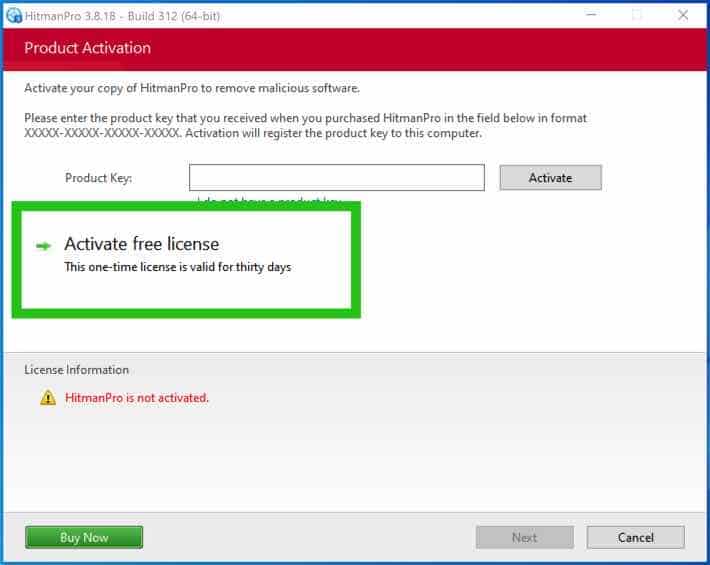
Enter your e-mail for a Sophos HitmanPRO free thirty days license. Click on Activate.
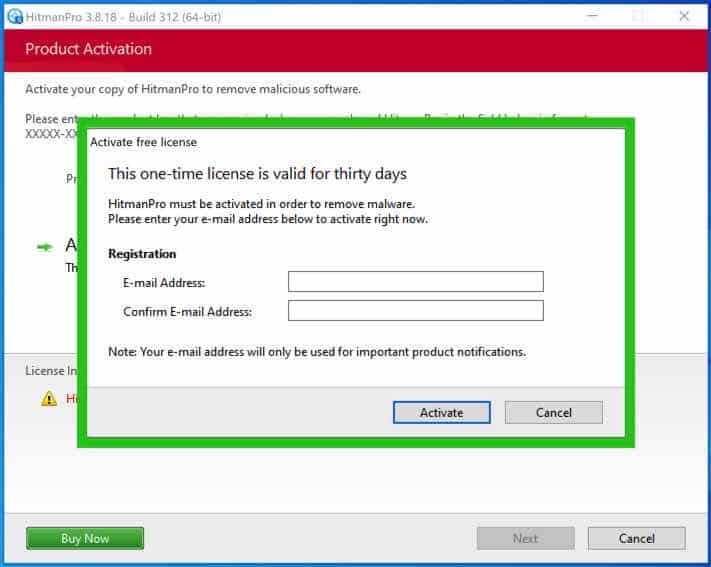
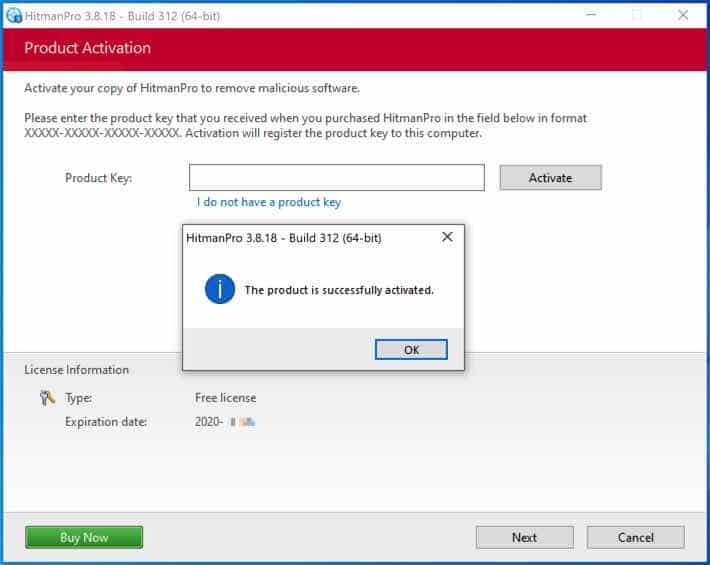
The free HitmanPRO license is successfully activated.
You’ll be presented with the malware removal results, click Next to continue.
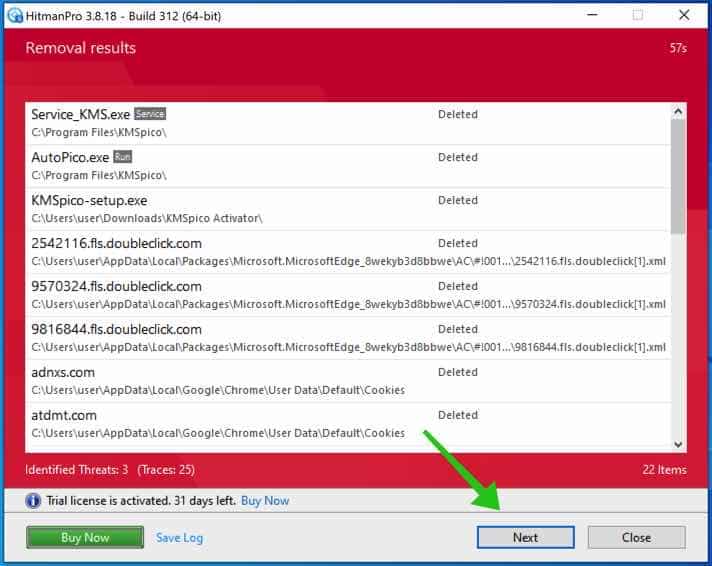
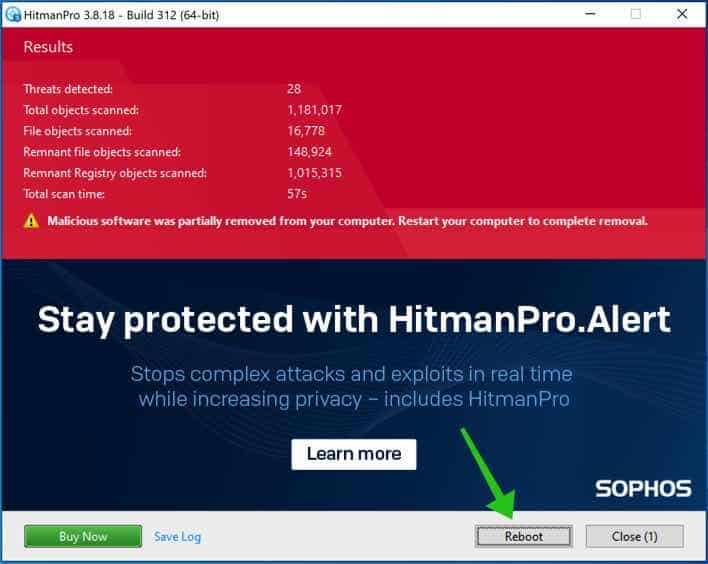
Malicious software was partially removed from your computer. Restart your computer to complete removal.